TACACS+ – (Terminal Access Controller Access Control System plus) — is a session protocol developed by Cisco.
Security(encryption) of the Protocol has improved. TACACS+ is a separately handles authentication, authorization, and accounting (AAA) services.
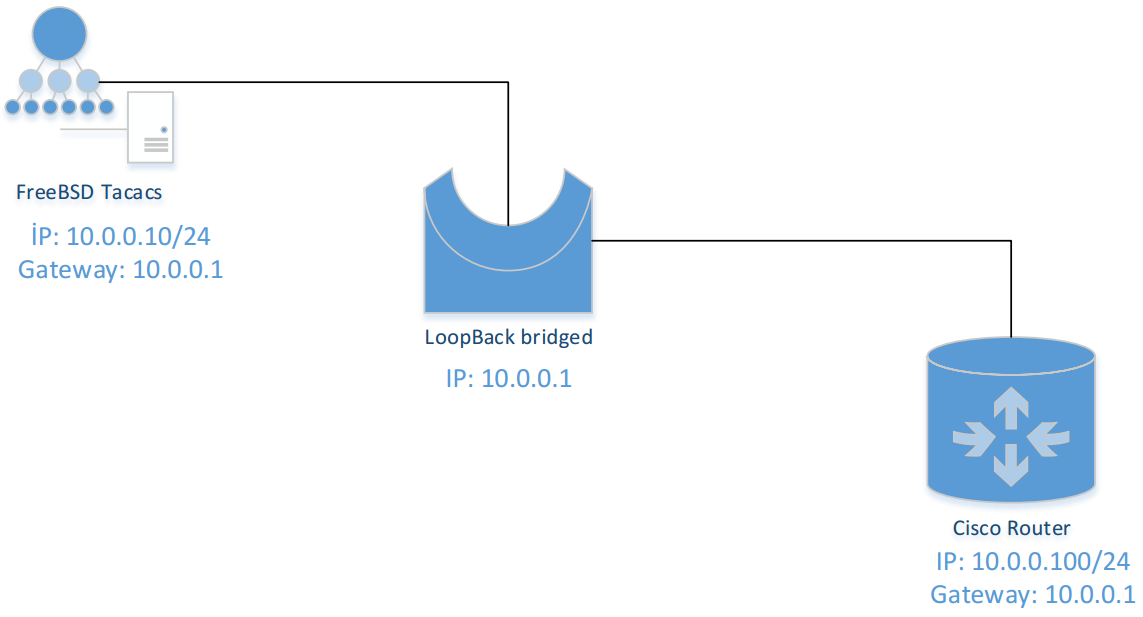
Used resources:
- FreeBSD 9.2 x64 (VM, IP: 10.0.0.10)
- GNS3 (Router 3700, IP: 10.0.0.100)
- Windows LoopBACK_Adapter (IP: 10.0.0.1)
Flow structure will be as follows:
FreeBSD x64 10.0.0.10 => LoopBACK Adapter (10.0.0.1) => GNS Cloud => Cisco Router 10.0.0.100
Network topology will be as follows:
Start the server configuration
Note: As virtual machine I used VmWare Workstation.
Before connect FreeBSD virtual port to LoopBack adapter update all ports and reboot thee server.
portsnap fetch extract update
cd /usr/ports/net/tac_plus4 # Go to the tac_plus4 port
make install clean # install
rehash # Update binary database
Add tac_plus to startup.
cat /etc/rc.conf
ifconfig_em0=”inet 10.0.0.10 netmask 255.255.255.0″
hostname=”tacacs.az”
sshd_enable=”YES”
tac_plus_enable=”YES” # StartUP tac_plus
tac_plus_flags=”-d 8 -d 16 -d 32 -d 64 -C /usr/local/etc/tac_plus.conf”
‘-d‘ – debuging
8 – authorization debugging
16 – authentication debugging
32 – crypt file debugging
64 – accounting debugging
‘-C‘ – ‘/usr/local/etc/tac_plus.conf‘ configuration file
The configuration file will be as follows:
cat /usr/local/etc/tac_plus.conf
# Path for accounting file
accounting file = /var/log/tac_plus.acct
# Pre-shared key which will be used between Cisco device and TACACS server
key = “freebsd”
# Groups
# Create groups with names ‘admin‘ and ‘service‘ and give access to this groups.
group = admin {
default service = permit # Allow all by default.
service = exec { # Privilege level is 15
priv-lvl = 15
}
}
group = service {
default service = deny # Deny by default.
service = exec { # Privilege level is 15
priv-lvl = 15
}
}
# Users
# Create users, add users to already created groups. Filter user commands.
user = jamal { # Create user by name ‘jamal‘
member = admin # and add to ‘admin‘ group.
login = des NQU3rObo2Ntoc # Crypt password with ‘des‘ algorithm (About crypt password with ‘tac_pwd‘ we will speak later)
}
user = auditor { # Create user by name ‘auditor‘,
member = admin # and add to ‘admin‘ group. Deny command list below.
cmd = configure {
deny .*
}
cmd = enable {
deny .*
}
cmd = clear {
deny .*
}
cmd = reload {
deny .*
}
cmd = write {
deny .*
}
cmd = copy {
deny .*
}
cmd = erase {
deny .*
}
cmd = delete {
deny .*
}
cmd = archive {
deny .*
}
login = cleartext secret # Password for ‘auditor‘ user we wrote as ‘cleartext‘.
}
user = event_manager { # ‘event_manager‘ user is member of,
member = service # ‘service‘ group(By default everything is deny for this group)
cmd = clear { # Here are allowed to use only the following commands.
permit .*
}
cmd = tclsh {
permit .*
}
cmd = squeeze {
permit .*
}
cmd = event {
permit .*
}
cmd = more {
permit .*
}
cmd = show {
permit version
}
cmd = delete {
permit .*
}
cmd = “delete /force” {
permit .*
}
cmd = “enable” {
permit .*
}
login = des 07xU3lvh1hC3I # Of course and here we encrypting password with ‘des‘ algorithm.
}
Qeyd: If we don’t want to see our passwords as cleartext, we must encrypt our passwords with ‘des‘ algorithm. For this we will use ‘tac_pwd‘ command.
tac_pwd # Just write this command and press the ENTER button. Then write password which you need, and press the ENTER button. Then copy ‘des‘ encrypted new line. You will use this encrypted password in ‘login = des‘ directive.
touch /var/log/tac_plus.acct # Create tacacs accounting file for logs.
chown tacacs /var/log/tac_plus.acct # Change owner to tacacs.
chmod 755 /var/log/tac_plus.acct # Give access to file.
/usr/local/etc/rc.d/tac_plus start # restart the service
netstat -a | grep tac # Check the daemon listener
tcp4 0 0 *.tacacs *.* LISTEN
Configure Cisco Router in GNS3.
conf t # Go to global mode.
interface fastEthernet 0/0 # Configure interface connected to cloud
ip address 10.0.0.100 255.255.255.0 # Set the IP address.
aaa new-model # Enter the AAA model
tacacs-server host 10.0.0.10 key 0 freebsd # Set IP address of tacacs server ‘10.0.0.10‘ and write pre-shared key ‘freebsd‘.
tacacs-server timeout 2 # Login timeout will be 2 second
tacacs-server directed-request # Request will be directly
aaa group server tacacs+ tac-int # Create aaa tacacs+ group with ‘tac-int‘ name
server 10.0.0.10 # And add ‘10.0.0.10‘ tacacs server to this list.
Add all aaa to tac-int admin group:
aaa authentication login admin group tac-int local
aaa authorization exec admin group tac-int local
aaa authorization commands 15 admin group tac-int local
aaa accounting update newinfo
aaa accounting commands 15 admin start-stop group tac-int
Apply admin login to terminal sessions between 0 and 4:
line vty 0 4
authorization commands 15 admin
authorization exec admin
accounting commands 15 admin
login authentication admin
For debug Router we can use the following commands.
Debug for AAA:
debug aaa per-user
debug aaa authentication
debug aaa authorization
debug aaa accounting
Debug for tacacs we can use the following commands:
debug tacacs authentication
debug tacacs authorization
debug tacacs accounting
debug tacacs events
debug tacacs packet
At the end from our Windows7 desktop connect to our router:
telnet 10.0.0.100
If you will see lines as follow then TACACS is working:
User Access Verification
Username:
If you will see line as follow then, something is wrong and go to debug.
Password: