Nagios is an open source software that can be used for network and infrastructure monitoring. Nagios will monitor servers, switches, applications and services. It alerts the System Administrator when something goes wrong and also alerts back when the issues has been rectified.
Using Nagios, you can:
- Monitor your entire IT infrastructure.
- Identify problems before they occur.
- Know immediately when problems arise.
- Share availability data with stakeholders.
- Detect security breaches.
- Plan and budget for IT upgrades.
- Reduce downtime and business losses.
Scenario
In this tutorial i am going to use two systems as mentioned below.
Nagios server:
Operating system : Ubuntu 14.10 Server IP Address : 192.168.1.150/24
Nagios client:
Operating System : Ubuntu 14.04 Server IP Address : 192.168.1.250/24
Prerequisites
Make sure your server have installed with fully working LAMP stack. If not, follow the below link to install LAMP server.
And, install the following prerequisites too:
sudo apt-get install build-essential libgd2-xpm-dev apache2-utils
Create Nagios User And Group
Create a new nagios user account and give it a password:
sudo useradd -m nagios sudo passwd nagios
Create a new nagcmd group for allowing external commands to be submitted through the web interface. Add both the nagios user and the apache user to the group.
sudo groupadd nagcmd sudo usermod -a -G nagcmd nagios sudo usermod -a -G nagcmd www-data
Download Nagios And Plugins
Go to the nagios download page, and get the latest version. As of writing this, the latest version was 4.0.8.
wget http://prdownloads.sourceforge.net/sourceforge/nagios/nagios-4.0.8.tar.gz
And, download nagios plugins too.
wget http://nagios-plugins.org/download/nagios-plugins-2.0.3.tar.gz
Install Nagios And Plugins
Install nagios:
Go to the folder where you’ve downloaded nagios, and extract it using command:
tar xzf nagios-4.0.8.tar.gz
Change to the nagios directory, and run the following commands one by one from the Terminal to compile and install nagios.
cd nagios-4.0.8
sudo ./configure --with-command-group=nagcmd
sudo make all
sudo make install
sudo make install-init
sudo make install-config
sudo make install-commandmode
Install Nagios Web interface:
Enter the following commands to compile and install nagios web interface.
sudo make install-webconf
You may get the following error:
/usr/bin/install -c -m 644 sample-config/httpd.conf /etc/httpd/conf.d/nagios.conf /usr/bin/install: cannot create regular file ‘/etc/httpd/conf.d/nagios.conf’: No such file or directory Makefile:296: recipe for target 'install-webconf' failed make: *** [install-webconf] Error 1
The above error message describes that nagios is trying to create the nagios.conf file inside the /etc/httpd.conf/ directory. But, in Ubuntu systems the nagios.conf file should be placed in /etc/apache2/sites-enabled/ directory.
So, run the following command instead of using sudo make install-webconf.
sudo /usr/bin/install -c -m 644 sample-config/httpd.conf /etc/apache2/sites-enabled/nagios.conf
Check if nagios.conf is placed in /etc/apache2/sites-enabled directory.
sudo ls -l /etc/apache2/sites-enabled/
Sample output:
total 4
lrwxrwxrwx 1 root root 35 Dec 17 17:59 000-default.conf -> ../sites-available/000-default.conf
-rw-r--r-- 1 root root 982 Dec 17 19:01 nagios.conf
Create a nagiosadmin account for logging into the Nagios web interface. Remember the password you assign to this account. You’ll need it while logging in to nagios web interface..
sudo htpasswd -c /usr/local/nagios/etc/htpasswd.users nagiosadmin
Restart Apache to make the new settings take effect.
sudo service apache2 restart
Install Nagios plugins:
Go to the directory where you downloaded the nagios plugins, and extract it.
tar xzf nagios-plugins-2.0.3.tar.gz
Change to the nagios plugins directory:
cd nagios-plugins-2.0.3
Run the following commands one by one to compile and install it.
sudo ./configure --with-nagios-user=nagios --with-nagios-group=nagios
sudo make
sudo make install
We aren’t finished yet.
Configure Nagios
Nagios sample configuration files have now been installed in the /usr/local/nagios/etc directory. These sample files should work fine for getting started with Nagios. However, you’ll need to put your actual email ID to receive alerts.
To do that, Edit the /usr/local/nagios/etc/objects/contacts.cfg config file with your favorite editor and change the email address associated with the nagiosadmin contact definition to the address you’d like to use for receiving alerts.
sudo nano /usr/local/nagios/etc/objects/contacts.cfg
Find the following line and enter the email id:
[...]
define contact{
contact_name nagiosadmin ; Short name of user
use generic-contact ; Inherit default values from generic-contact template (defined above)
alias Nagios Admin ; Full name of user
email sk@unixmen.com ; <<***** CHANGE THIS TO YOUR EMAIL ADDRESS ******
}
[...]
Save and close the file.
Then, Edit file /etc/apache2/sites-enabled/nagios.conf,
sudo nano /etc/apache2/sites-enabled/nagios.conf
And edit the following lines if you want to access nagios administrative console from a particular IP series. Here, I want to allow nagios administrative access from 192.168.1.0/24 series only.
[...] ## Comment the following lines ## # Order allow,deny # Allow from all ## Uncomment and Change lines as shown below ## Order deny,allow Deny from all Allow from 127.0.0.1 192.168.1.0/24 [...]
Enable Apache’s rewrite and cgi modules:
sudo a2enmod rewrite
sudo a2enmod cgi
Restart apache service.
sudo service apache2 restart
Check nagios,conf file for any syntax errors:
sudo /usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg
If there are no errors, start nagios service and make it to start automatically on every boot.
sudo service nagios start
sudo ln -s /etc/init.d/nagios /etc/rcS.d/S99nagios
Access Nagios Web Interface
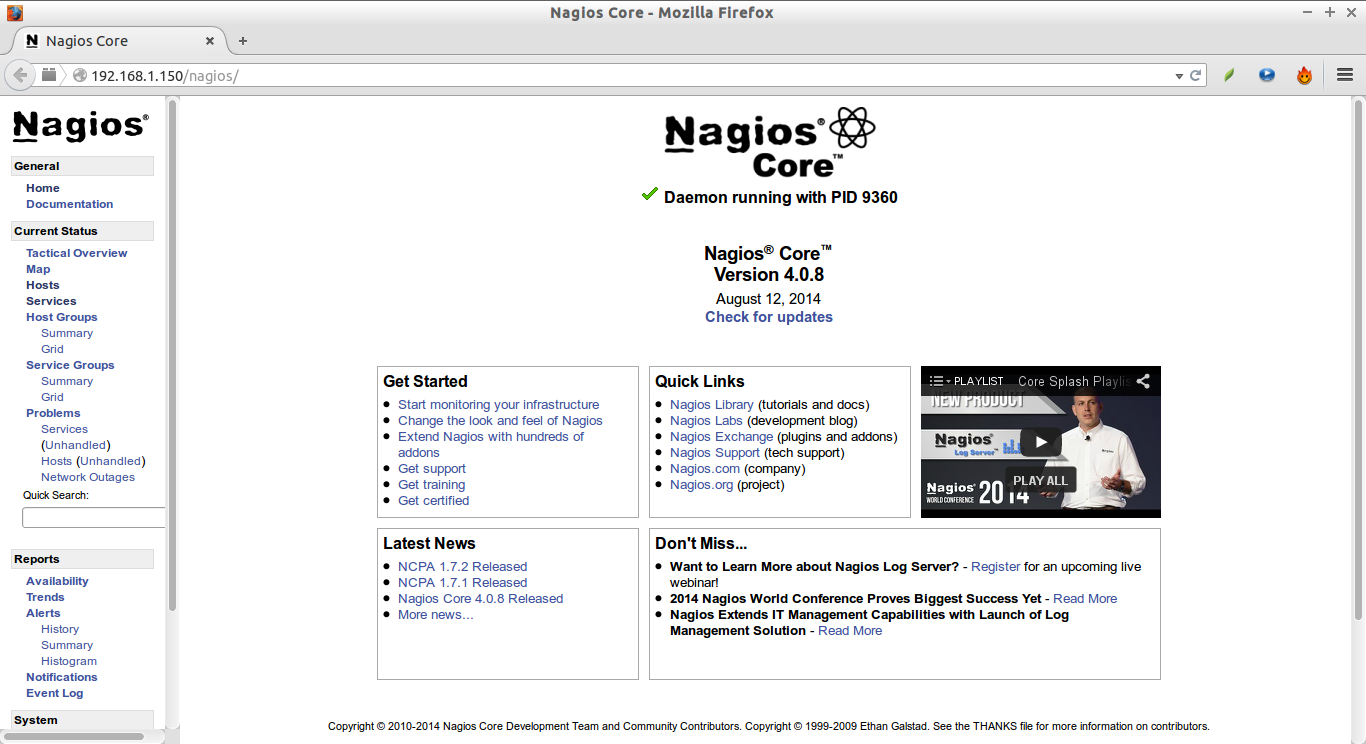
Open nagios administrator console with URL http://nagios-server-ip/nagios and enter the username as nagiosadmin and its password which we created in the earlier steps.
This is how Nagios administrative console looks:
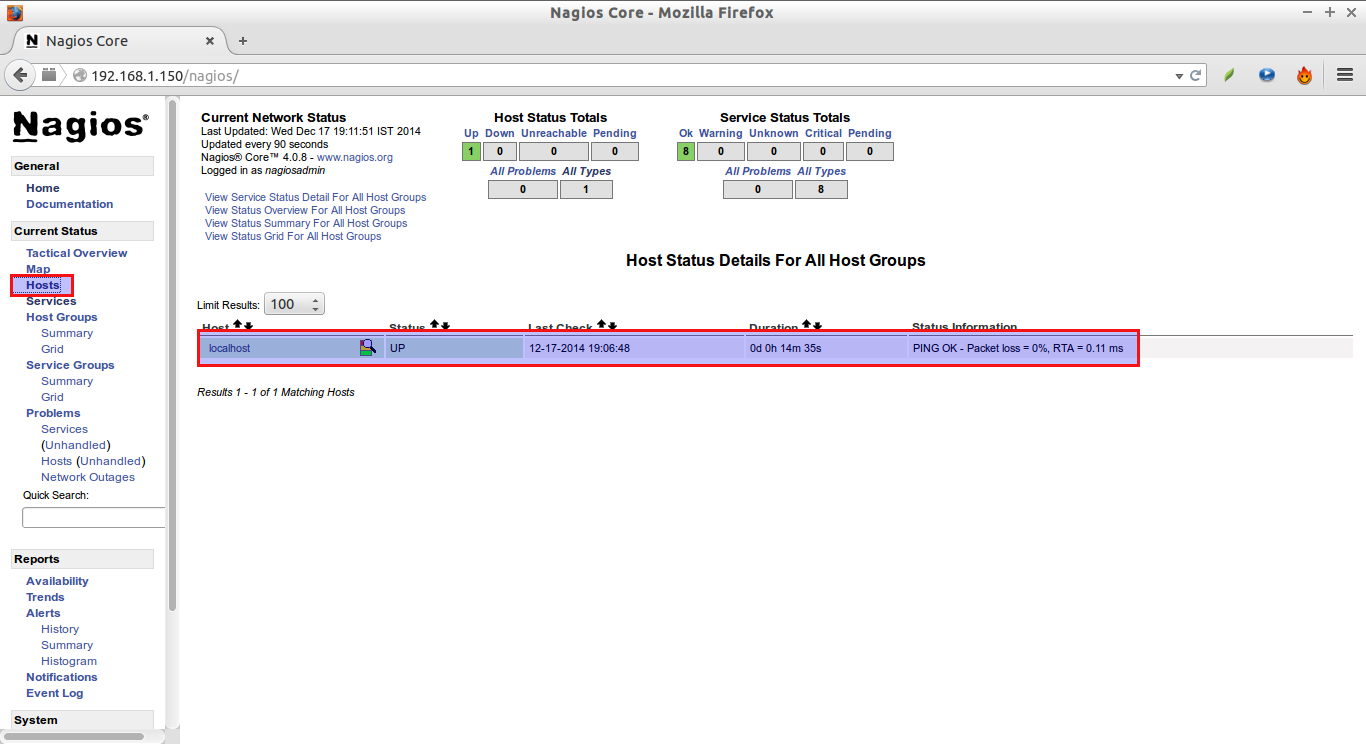
Click on the “Hosts” section in the left pane of the console. You will see there the no of hosts to be monitored by Nagios server. We haven’t added any hosts yet. So it simply monitors the localhost itself only.
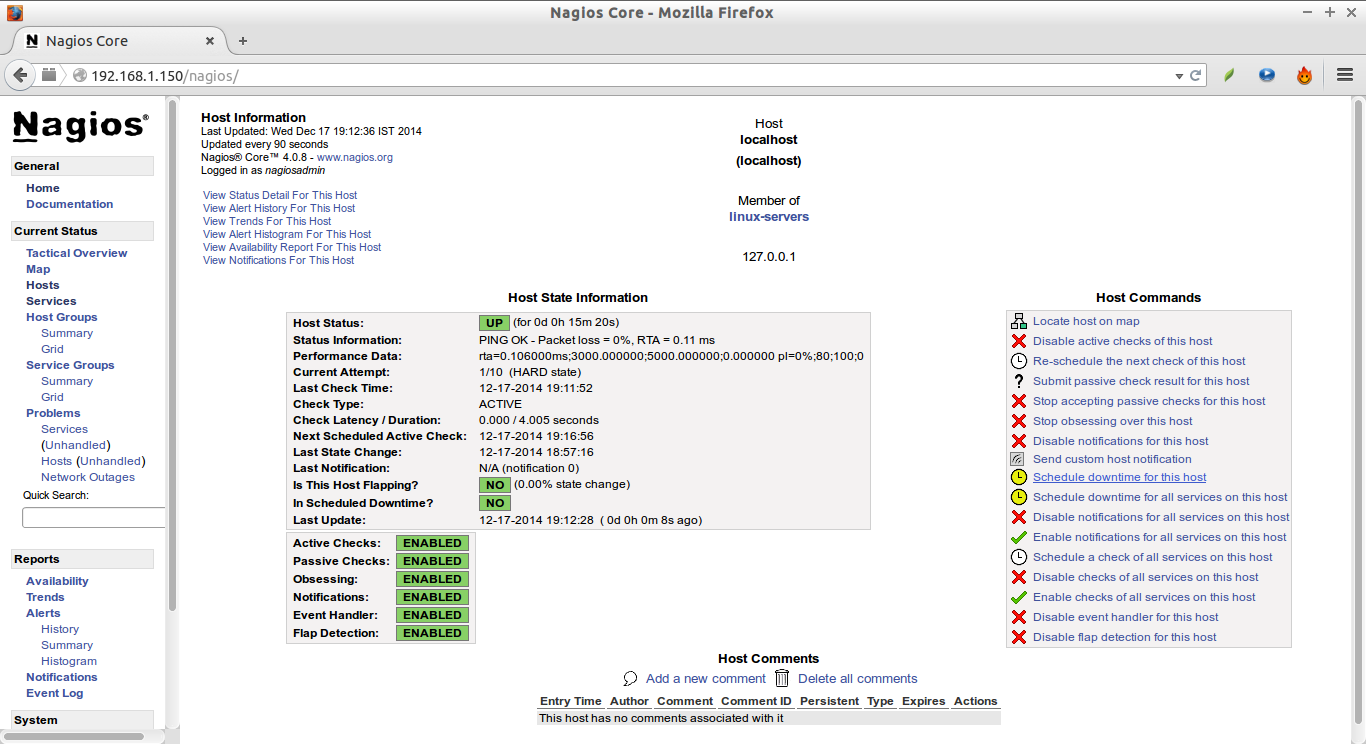
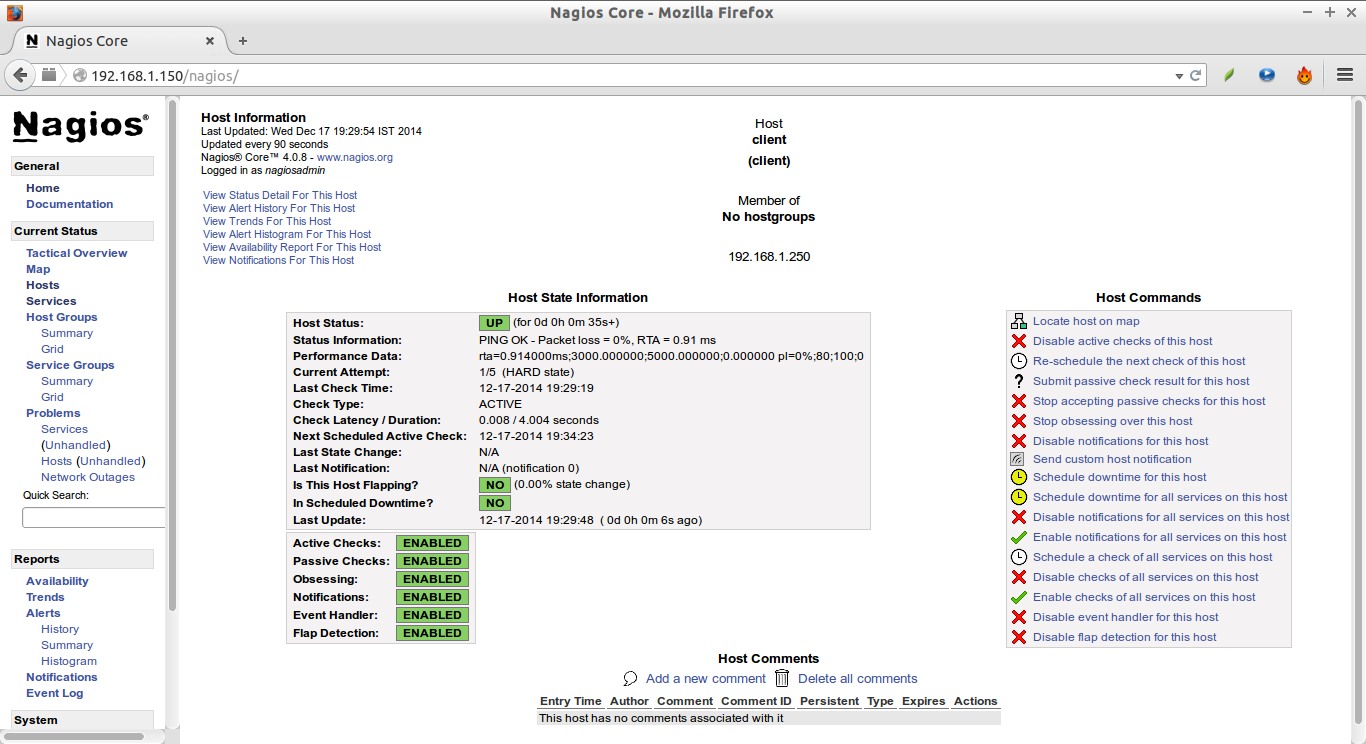
Click on the particular host to display more details:
Add Monitoring targets to Nagios server
Now, let us add some clients to monitor by Nagios server. To do that we have to install nrpe and nagios-plugins in our monitoring targets.
On CentOS/RHEL/Scientifc Linux clients:
Add EPEL repository in your CentOS/RHEL/Scientific Linux 6.x or 7 clients to install nrpe package.
To install EPEL on CentOS 7, run the following command:
yum install epel-release
On CentOS 6.x systems, refer the following link.
Install “nrpe” and “nagios-plugins” packages in client systems:
yum install nrpe nagios-plugins-all openssl
On Debian/Ubuntu clients:
sudo apt-get install nagios-nrpe-server nagios-plugins
Configure Monitoring targets
Edit /etc/nagios/nrpe.cfg file,
sudo nano /etc/nagios/nrpe.cfg
Add your Nagios server ip address:
[...] ## Find the following line and add the Nagios server IP ## allowed_hosts=127.0.0.1 192.168.1.150 [...]
Start nrpe service on CentOS clients:
CentOS 7:
systemctl start nrpe chkconfig nrpe on
CentOS 6.x:
service nrpe start chkconfig nrpe on
For Debian/Ubuntu Clients, start nrpe service as shown below:
sudo /etc/init.d/nagios-nrpe-server restart
Now, go back to your Nagios server, and add the clients in the configuration file.
To do that, Edit “/usr/local/nagios/etc/nagios.cfg” file,
sudo nano /usr/local/nagios/etc/nagios.cfg
and uncomment the following lines.
## Find and uncomment the following line ## cfg_dir=/usr/local/nagios/etc/servers
Create a directory called “servers” under “/usr/local/nagios/etc/”.
sudo mkdir /usr/local/nagios/etc/servers
Create config file to the client to be monitored:
sudo nano /usr/local/nagios/etc/servers/clients.cfg
Add the following lines:
define host{
use linux-server
host_name client
alias client
address 192.168.1.250
max_check_attempts 5
check_period 24x7
notification_interval 30
notification_period 24x7
}
Here, 192.168.1.250 is my nagios client IP address. Finally restart nagios service.
sudo service nagios restart
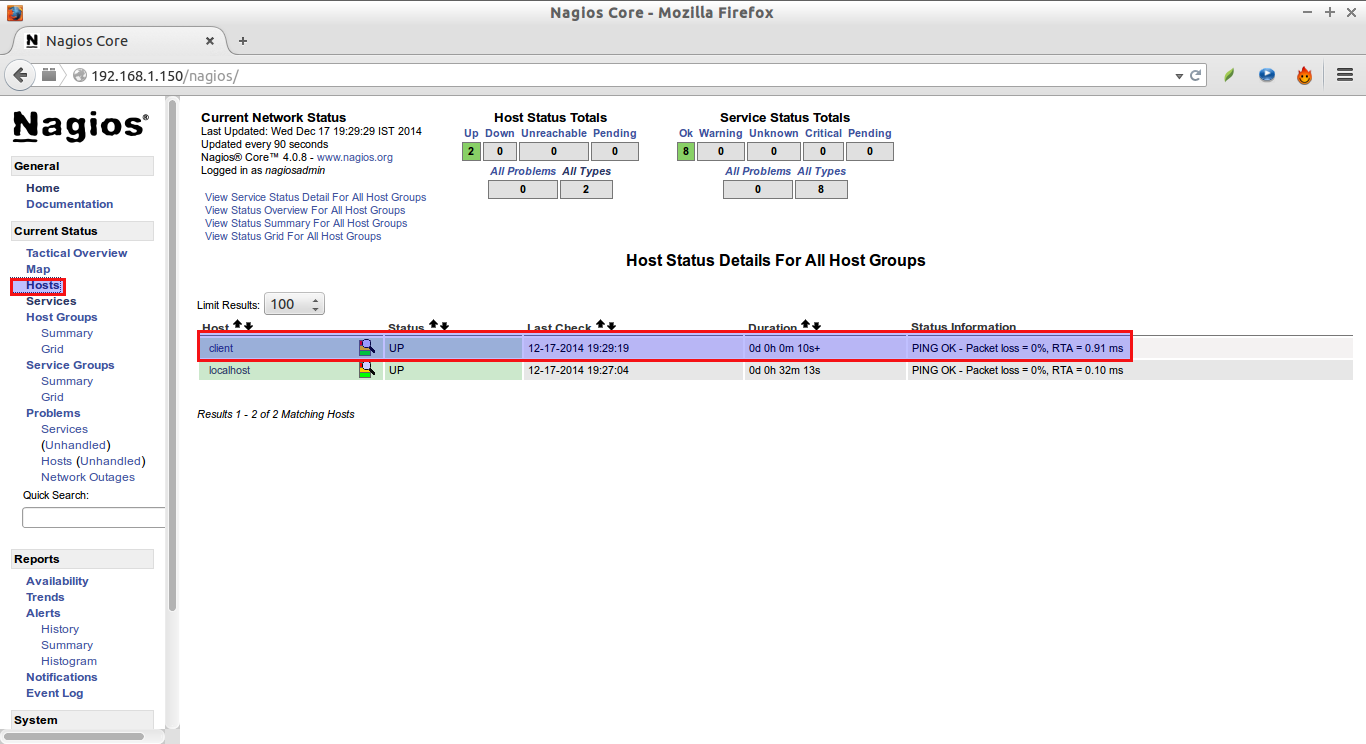
Wait for few seconds, and refresh nagios admin console in the browser and navigate to “Hosts” section in the left pane. You will see the newly added client will be visible there. Click on the host to see if there is anything wrong or any alerts it has.
Click on the monitoring target (client) to view the detailed output:
Similarly, you can define more clients by creating a separate config files “/usr/local/nagios/etc/servers” directory for each client.
Define services
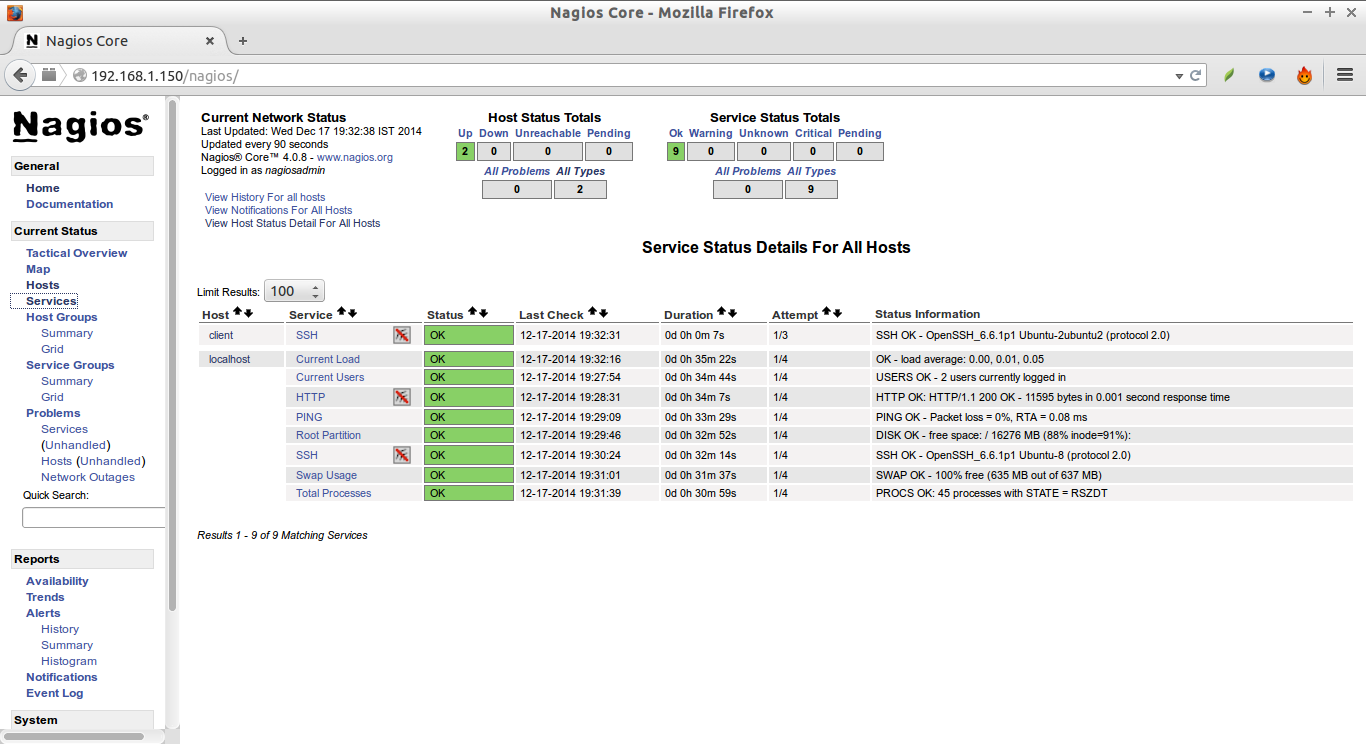
We have just defined the monitoring host. Now, let us add some services of the monitoring host. For example, to monitor the ssh service, add the following lines shown in bold in the “/usr/local/nagios/etc/servers/clients.cfg” file.
sudo nano /usr/local/nagios/etc/servers/clients.cfg
Add the following lines shown in bold:
define host{
use linux-server
host_name client
alias client
address 192.168.1.250
max_check_attempts 5
check_period 24x7
notification_interval 30
notification_period 24x7
}
define service {
use generic-service
host_name client
service_description SSH
check_command check_ssh
notifications_enabled 0
}
Save and close the file. Restart Nagios.
sudo service nagios restart
Wait for few seconds, and check for the added services (i.e ssh) in the nagios web interface. Navigate to Services section on the left side bar, you’ll see the ssh service there.
To know more about object definitions such as Host definitions, service definitions, contact definitions, please do visit here. This page will explain you the description and format of all object definitions.
Additional Tip:
If you’re trying to use check_http with the -S flag (for https), this guide misses a big step.
Make sure you install openssl and libssl-dev first. And yes, even if your Nagios server is checking a remote client, you need openssl and libssl-dev locally.
The when you get to configuring the Nagios plugins, add –with-openssl so you end up with:
./configure --with-nagios-user=nagios --with-nagios-group=nagios --with-openssl
I would like to thank our Unixmen reader for this useful tip.
That’s it. Cheers!