What is Nikto web scanner and it’s use ?
Nikto Web-scanner is a open source web-server scanner which can be used to scan the web-servers for malicious programs and files. Nikto can be used to scan the outdated versions of programs too. Nikto will provide us a quick and easy scan to find out the dangerous files and programs in server, At the end of scan result with a log file. Using nikto we can scan http, https, httpd traffics too.
To run the Nikto we don’t need any hard resource using software’s, If our server installed with Perl it’s fine to run the nikto. It’s available for every Operating systems such as Linux, Unix like RedHat, Centos, Debian, Ubuntu, Solaris, BackTrack, MacOSX. Supports SSL, http proxy, Scan multiple ports on a server, Check for outdated server components etc.. We can get the output of result in following formats TXT, CSV, HTML, XML.
Newly released version of Nikto Web scanner:
Nikto released it’s version 2.1.5 in 2012 but it’s under updates for each and every new vulnerabilities till date.
vulnerabilities Database:
We can find each and every vulnerabilities database in following URL.
My Environment Setup:
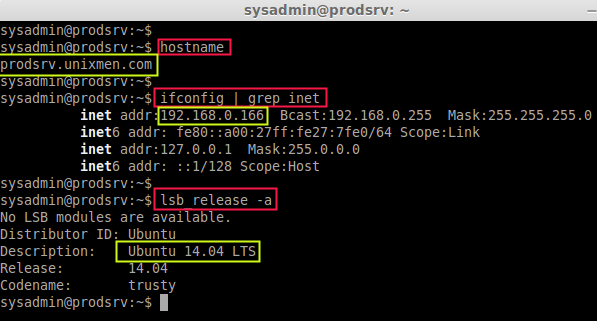
- Hostname : prodsrv.unixmen.com
- IP address : 192.168.0.166
- Operating system : Ubuntu 14.04 LTS
Run the following commands to check the hostname, IP address, and OS version.
hostname
ifconfig | grep inet
lsb_release -a
A Brief History of Nikto
Nikto was first released in December 2001 by creator Chris Sullo, pen tester and security consultant, who continued his career in computer security while maintaining this open-source project.
Nikto is impressive since the base package was entirely written by Sullo and later enhanced by other enthusiasts.
Presently, Nikto’s development is supported by the paid exploit rules package. In other words, the free tool is not entirely free to use. This puts the tool in the same category as commercial vulnerability managers with access to much bigger budgets.
Supporting the development of the tool remained a struggle until Invicti partnered with the project in February 2014. As of 2022, Invicti remains a partner of Nikto.
Uses of Nikto
The 20-year-old tool is currently on version 2.5 and billed as “Nikto2.” The server scanner can scan over 6,700 vulnerabilities on a web server and also attempts an array of attacks to find security lapses. It is also equipped to look for dated software.
Nikto can scan server ports and can be set up to scan multiple servers in one session. What’s more, the anti-IDS attack test helps you gauge the protection of your intrusion detection system (if one is installed).
While the results of the scan are summarized on the screen after it ends, you can export it to text, HTML, CSV, or other formats. Users can also create a format template for the results of the scans.
It’s important to note that finishing a scan can take some time. Nikto does not include a progress bar, so it can be hard to tell whether it’s still going. However, the tool deals with this setback by allowing users to press the space bar to interrupt the procedure.
When interrupted, the tool provides a progress report, allowing you to estimate the time remaining for the scan to complete.
Step by Step Installation
First we need to download and install nikto web scanner from Official website.
Let we download the package which in .bz2 or gz format using wget in our production server.
https://cirt.net/nikto/nikto-2.1.5.tar.bz2
https://cirt.net/nikto/nikto-2.1.5.tar.gz
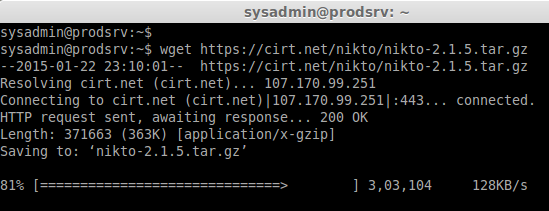
Step 1: Download the package
wget https://cirt.net/nikto/nikto-2.1.5.tar.gz
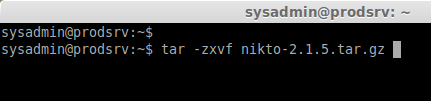
Step 2: Extract the package using below command
tar -zxvf nikto-2.1.5.tar.gz
Step 3: Navigate to the home directory
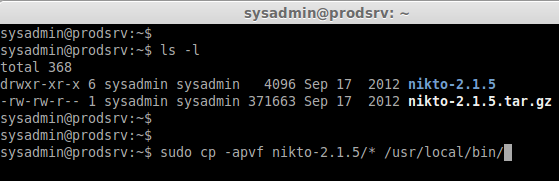
Then move the extracted nikto package to /usr/local/bin/:
cd ~
sudo cp -apvf nikto-2.1.5/* /usr/local/bin/
ls -l /usr/local/bin/
* Nikto config file need to be in /etc/, But now it’s currently under /usr/local/bin/ While having a look into conf we can find that nikto will skip the scan for ports 21 & 111, And from were it want to download it’s update and much more.
sudo vim /usr/local/bin/nikto-2.1.5/nikto.conf
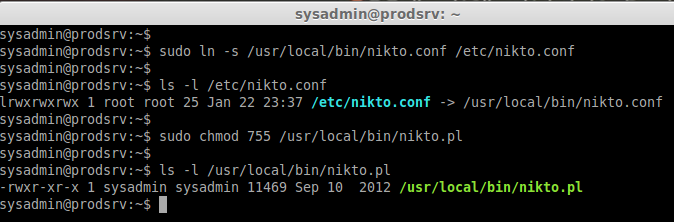
Step 4: Creating Symlink & Permission.
Now we need to create a symlink for our conf file to /etc/ because nikto look for conf file under /etc/. Then make our nikto script as executable using chmod.
sudo ln -s /usr/local/bin/nikto.conf /etc/nikto.conf
ls -l /etc/nikto.conf
sudo chmod 755 /usr/local/bin/nikto.pl
ls -l /usr/local/bin/nikto.pl
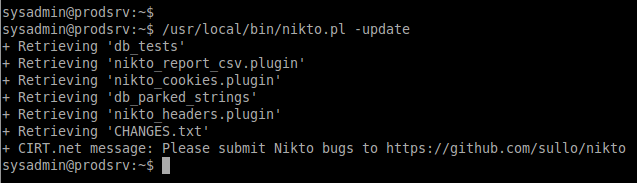
Step 5: Update the nikto Database.
Before performing any scan we need to update the nikto database packages using.
/usr/local/bin/nikto.pl -update
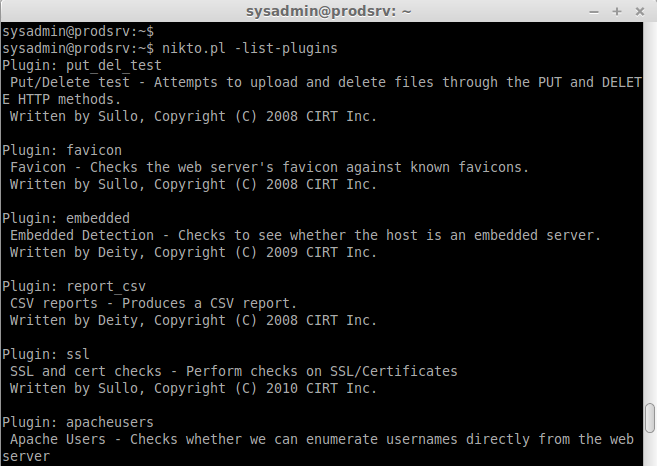
To list the available Plugins for nikto we can use the below command.
nikto.pl -list-plugins // To list the installed plugins //
Step 6: Scan for vulnerabilities:
To Scan for a website using hostname we can use the option -h followed by niktop command.
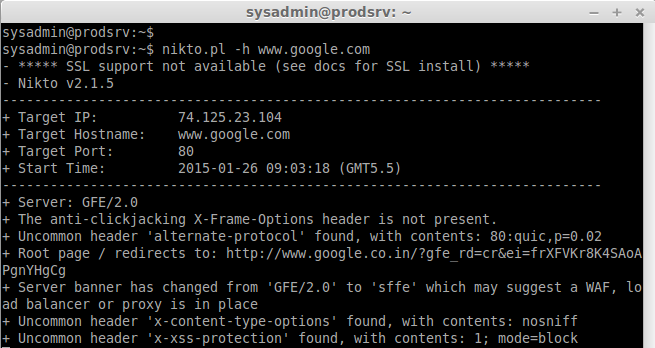
nikto.pl -h www.unixmen.com // To scan a website //
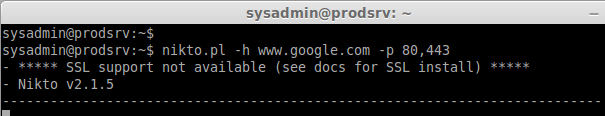
Scan for a hostname using multiple ports we can use -p option followed by nikto.pl
nikto.pl -h www.google.com -p 80,443
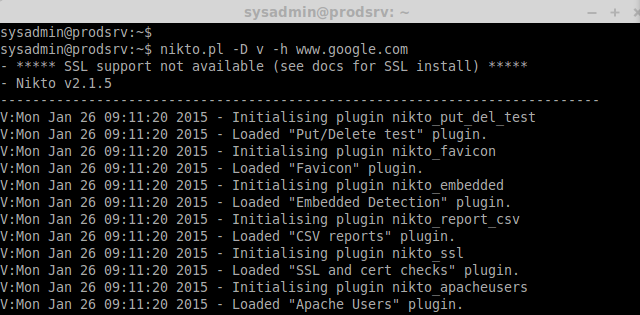
While scanning for vulnerabilities we can see the process, If we need to see the live process we need to use option Display.
nikto.pl -D v -h www.google.com
Where,
- -D = Display
- v = Verbose
- -h = hostname
Scan Only using specific check using tuning option:
While Tuning options used we can specify which test need to made, Using x option we can exclude the tests which we don’t need.
Below Options are available for specific scan’s.
0 – File Upload
1 – Interesting File // we will get in logs
2 – Misconfiguration / Default File
3 – Information Disclosure
4 – Injection (XSS/Script/HTML)
5 – Remote File Retrieval – Inside Web Root
6 – Denial of Service // Scan for DDOS
7 – Remote File Retrieval – Server Wide
8 – Command Execution // Remote Shell
9 – SQL Injection // Scan for mysql vulnerabilities
a – Authentication Bypass
b – Software Identification
c – Remote Source Inclusion
x – Reverse Tuning Options
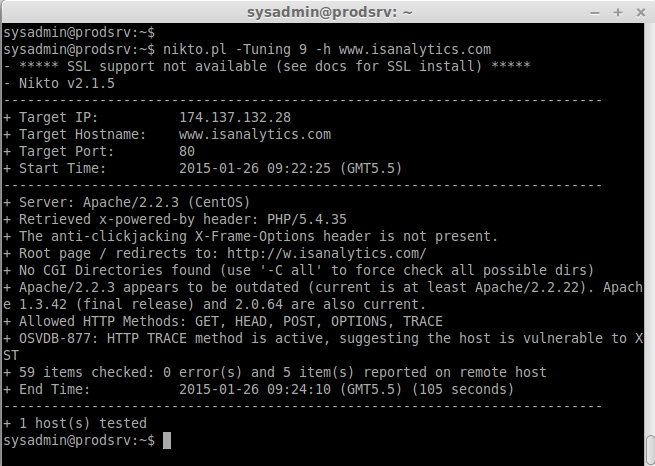
Now here let me scan for SQL vulnerabilities for a website. A single test will finish in short time if we not specified for a single scan it will take the full scan and take hours to complete.
nikto.pl -Tuning 9 -h www.isanalytics.com
nikto.pl -Tuning 69 -h www.isanalytics.com
Scan and save the result to a file using below command to find the vulnerabilities.
nikto.pl -Display V -o nikto_scan_result.html -Format html -h 192.168.0.166
After scan completes we will get the result in html format in current directory as show below.
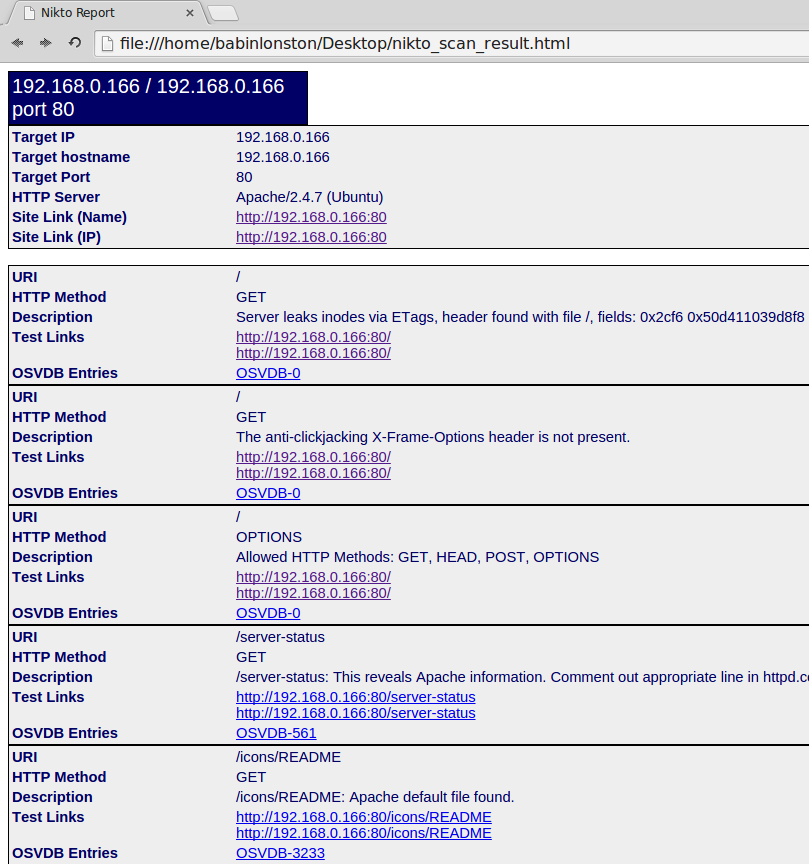
We will get a decent format of output as show below in html format to find the vulnerabilities.
That’s it, Here we have seen how to protect our website from several vulnerabilities. To know the up to date vulnerabilities we need to keep the nikto package update before scanning.
Resources:
- Home page : https://cirt.net/Nikto2
- Documentation : https://cirt.net/nikto2-docs/
- Development : https://github.com/sullo/nikto
Nikto Pros and Cons
It’s important to understand the state of the project before weighing out its pros and cons. Since Nikto is free and the lovechild of one active developer, you can expect software updates to take long before becoming available.
While Invicti has sponsored the project for a few years now, the development strategy remains more or less unchanged.
The Nikto website explains that release management is still manual. While there are plans to automate it, they haven’t been put in motion.
This makes it seem like Sullo is still both sole developer and support technician for Nikto. Further, the lack of a message board or community support can make using the tool more challenging compared to other open-source projects.
Here are the pros and cons of Nikto:
| Pros | Cons |
| The base program is free | Lacks a GUI |
| Nikto checks the same number of websites in a standard scan as paid vulnerability managers | No dedicated development or support team |
| Web applications can be externally checked | The lack of community support makes working around issues challenging for some |
| It comes included in Kali Linux | Nikto does not work without a paid vulnerability list |
Conclusion
To those who searching for web scanner nikto will be one of powerful tool to end your web scanner search. Hope this will will bring you a good idea to scan vulnerbalites for you site even your site are well harden in several settings.