Nagios is the leader and industry standard in enterprise-class monitoring solutions. Nagios provides two monitoring tools Nagios Core and Nagios XI.
Nagios Core is a free and open source tool that allows you to monitor your entire IT infrastructure to ensure hosts, services and applications are functioning properly. For more information, you can visit the website of Nagios. This article is intended for use by Nagios Administrators who wish to monitor Linux servers with Nagios Core using the linux SNMP.
SNMP stands for simple network management protocol. It is a way that servers can share information about their current state, and also a channel through which an administer can modify pre-defined values. While the protocol itself is very simple, the structure of programs that implement SNMP can be very complex.
If you still didn’t install Nagios Core , check the following articles.
- Install and Configure Nagios On CentOS, RHEL, Scientific Linux 6.5/6.4
- Install and configure Nagios 4 In CentOS 7
- Install and configure Nagios 4 in Ubuntu 14.10
In this article we will show you how to install and configure SNMP in the remote server and how to add the host to Nagios Core.
Installing and Configuring SNMP Agent On The Remote Linux Machine
Install and Configure SNMP on Ubuntu 14.04/14.10
We can begin to explore how SNMP can be implemented on a system by installing the SNMP agent on some Ubuntu systems.
1- Install SNMPd agent on Ubuntu Server
Type the following command as root, enter:
apt-get update && apt-get install snmpd
2- SNMPd Configuration
The snmpd daemon must be configured to work with Cacti. The configuration file is located at “/etc/snmp/snmpd.conf“. Make sure you are editing the snmpd.conf file and not the snmp.conf file.
To get started, on our agent computer, we need to open the daemon’s configuration file with sudo privileges:
sudo nano /etc/snmp/snmpd.conf
First, we need to change the
directive. Currently, it is set to only allow connections originating from the local computer. We need to comment out the current line, and uncomment the line underneath, which allows all connections
# Listen for connections from the local system only
<span class="highlight">#</span>agentAddress udp:127.0.0.1:161
# Listen for connections on all interfaces (both IPv4 *and* IPv6)
<span class="highlight">agentAddress udp:161,udp6:[::1]:161</span>
Add view
<span class="title">view</span> all included .<span class="number">1</span> <span class="number">80</span>
ACCESS CONTROL
Change the following line:
rocommunity <span class="keyword">public</span> <span class="keyword">default</span> -V systemonly
To:
rocommunity test1252serc <span class="keyword">default</span> -V <span class="built_in">all</span>
The snmp community is test1252serc.
SYSTEM INFORMATION
You can add the physical location of your server and a contact email. These may be helpful for distinguishing machines if you are monitoring a large number of cloud servers.
<span class="title">sysLocation</span> Your System Location
sysContact contact<span class="variable">@email</span>.com
After you are done with your modifications, save the file, exit and restart the snmpd service.
$su<span class="operator"><span class="keyword">do</span> service snmpd restart</span>
Install and Configure SNMP on Centos
1- Install SNMP and SNMP Utilities
Installing SNMP and some optional SNMP utilities is as simple as running one command:
yum -y install net-snmp net-snmp-utils
2- Add a Basic Configuration for SNMP
Now, let’s take the default SNMP configuration file, /etc/snmp/snmpd.conf and move it to an alternate location,/etc/snmp/snmpd.conf.orig.
mv /etc/snmp/snmpd.conf /etc/snmp/snmpd.conf.orig
And now we’ll create a new /etc/snmp/snmpd.conf:
vim /etc/snmp/snmpd.conf
# Map 'tes90w90t' community to the 'AllUser'
# sec.name source community
com2sec AllUser default tes90w90t
# Map 'ConfigUser' to 'ConfigGroup' for SNMP Version 2c
# Map 'AllUser' to 'AllGroup' for SNMP Version 2c
# sec.model sec.name
group AllGroup v2c AllUser
# Define 'SystemView', which includes everything under .1.3.6.1.2.1.1 (or .1.3.6.1.2.1.25.1)
# Define 'AllView', which includes everything under .1
# incl/excl subtree
view SystemView included .1.3.6.1.2.1.1
view SystemView included .1.3.6.1.2.1.25.1.1
view AllView included .1
# Give 'ConfigGroup' read access to objects in the view 'SystemView'
# Give 'AllGroup' read access to objects in the view 'AllView'
# context model level prefix read write notify
access AllGroup "" any noauth exact AllView none none
The above text is noted with basic information on the function of each configuration line. In short, we’re creating this scenarios for the polling
AllUser is assigned to AllGroup and may only use SNMP security model 2c , AllGroup can use the AllView .
AllView is assigned to the entire OID tree, and all of this is referenced in an SNMP poll by the secret, and uniquecommunity string tes90w90t.
service snmpd restart
Configure SNMP to start when the server boots:
chkconfig snmpd on
3- Test the SNMP Configuration
If you have a firewall configured, ensure that you have UDP port 161 open to your SNMP lookup server.
On your SNMP lookup server, you can do the following to perform a quick SNMP test to ensure that it’s working.
snmpwalk -v 2c -c tes90w90wer -O e 127.0.0.1
you should get an output like below :
SNMPv2-MIB::sysDescr.0 = STRING: Linux 2.6.18-194.11.4.el5xen #1 SMP Tue SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (242211) 0:40:22.11 SNMPv2-MIB::sysContact.0 = STRING: root@localhost SNMPv2-MIB::sysName.0 = STRING: SNMPv2-MIB::sysLocation.0 = STRING: Unknown SNMPv2-MIB::sysORLastChange.0 = Timeticks: (2) 0:00:00.02 SNMPv2-MIB::sysORID.1 = OID: SNMPv2-MIB::snmpMIB SNMPv2-MIB::sysORID.2 = OID: TCP-MIB::tcpMIB SNMPv2-MIB::sysORID.3 = OID: IP-MIB::ip SNMPv2-MIB::sysORID.4 = OID: UDP-MIB::udpMIB SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup SNMPv2-MIB::sysORID.6 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance SNMPv2-MIB::sysORID.7 = OID: SNMP-MPD-MIB::snmpMPDCompliance SNMPv2-MIB::sysORID.8 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance
Configure Nagios To Monitor The Linux Host
Before you start configuring nagios , Here are some useful OID’s on Linux:
List NIC names: .1.3.6.1.2.1.2.2.1.2 Get Bytes IN: .1.3.6.1.2.1.2.2.1.10 Get Bytes IN for NIC 4: .1.3.6.1.2.1.2.2.1.10.4 Get Bytes OUT: .1.3.6.1.2.1.2.2.1.16 Get Bytes OUT for NIC 4: .1.3.6.1.2.1.2.2.1.16.4
1 minute Load: .1.3.6.1.4.1.2021.10.1.3.1 5 minute Load: .1.3.6.1.4.1.2021.10.1.3.2 15 minute Load: .1.3.6.1.4.1.2021.10.1.3.3
percentage of user CPU time: .1.3.6.1.4.1.2021.11.9.0 raw user cpu time: .1.3.6.1.4.1.2021.11.50.0 percentages of system CPU time: .1.3.6.1.4.1.2021.11.10.0 raw system cpu time: .1.3.6.1.4.1.2021.11.52.0 percentages of idle CPU time: .1.3.6.1.4.1.2021.11.11.0 raw idle cpu time: .1.3.6.1.4.1.2021.11.53.0 raw nice cpu time: .1.3.6.1.4.1.2021.11.51.0
Total Swap Size: .1.3.6.1.4.1.2021.4.3.0 Available Swap Space: .1.3.6.1.4.1.2021.4.4.0 Total RAM in machine: .1.3.6.1.4.1.2021.4.5.0 Total RAM used: .1.3.6.1.4.1.2021.4.6.0 Total RAM Free: .1.3.6.1.4.1.2021.4.11.0 Total RAM Shared: .1.3.6.1.4.1.2021.4.13.0 Total RAM Buffered: .1.3.6.1.4.1.2021.4.14.0 Total Cached Memory: .1.3.6.1.4.1.2021.4.15.0
Path where the disk is mounted: .1.3.6.1.4.1.2021.9.1.2.1 Path of the device for the partition: .1.3.6.1.4.1.2021.9.1.3.1 Total size of the disk/partion (kBytes): .1.3.6.1.4.1.2021.9.1.6.1 Available space on the disk: .1.3.6.1.4.1.2021.9.1.7.1 Used space on the disk: .1.3.6.1.4.1.2021.9.1.8.1 Percentage of space used on disk: .1.3.6.1.4.1.2021.9.1.9.1 Percentage of inodes used on disk: .1.3.6.1.4.1.2021.9.1.10.1
.1.3.6.1.2.1.1.3.0
Now make sure your nagios is able to excute snmp on remote Linux system. Try to execute following command. In this example 192.168.5.178 is the ip address of the remote host.
snmpwalk -v 1 -c tes90w90wer 192.168.5.178 .1.3.6.1.4.1.2021.9.1.7.1 UCD-SNMP-MIB::dskAvail.1 = INTEGER: 110247880
Then add host entry for each remote box you will monitor. This example is using the linuxserver template, be sure to
check that template out to verify the settings are the ones you want to use.
Edit the hosts.cfg file and add the default host template name and define remote hosts as shown below
nano /usr/local/nagios/etc/hosts.cfg
define host{
use linuxserver
host_name class
alias Base
address 192.168.5.178
}
The last step is the configure services. Each service you want to monitor on the remote host must be entered individually.The check_nrpe command is used to access the remote server and then execute the Nagios plugin that is on the remote server and retrieve the information.
Now open services.cfg file add the following services to be monitored.
define service{
use generic-service
host_name class
service_description CPU Load
check_command check_snmp!tes90w90wer!1.3.6.1.2.1.2.2.1.2!
}
Next, verify Nagios Configuration files for any errors.
/usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg Total Warnings: 0 Total Errors: 0
Finally, restart Nagios.
service nagios restart
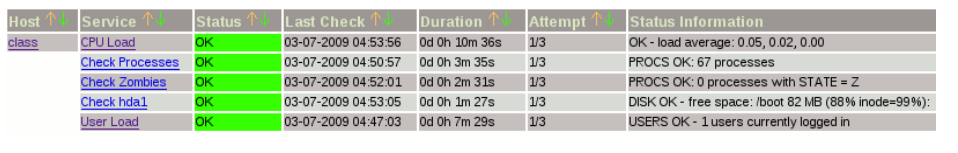
Log into the web interface via : http://[SERVER_IP]/nagios , enter your login information and check for new Linux hosts added in nagios core service.
That’s all.
Congratulations! Enjoy your Monitoring platform Nagios Core.