Introduction
Justniffer is a network protocol analyzer that can be used as alternative to Snort. It is a very popular network analyzer tool, it work interactively to trace/sniff a live network. It can capture traffic from a live environment, support “lipcap” a “tcpdump” file formats. It helps the users to perform analysis in a complex network where it is difficult to capture traffic with wireshark. Specially it help to analyze application layer traffic very significantly and can extract http contents like images, scripts, HTML etc easily. Justsniffer is helpful in understanding how communication occur among different components.
Features
This is the advantage of Justniffer that it collect all traffic from a complex network without affecting system performance, and can save logs for future analysis, some of the important features of Justniffer are:
1. Reliable TCP flow rebuilding
It can record and reassemble TCP segments and IP fragments using a portion of host Linux kernel.
2. Logging
Log are saved for future analysis and can be customized as and when required.
3. Extensible
Can be extended with external python, perl and bash scripts to get some additional results from analysis reports.
4. Performance Management
Retrieve information on the basis of Connection time, close time, response time or request time etc.
Installation
Justsniffer can be installed with ppa.
To add the repo, run:
$ sudo add-apt-repository ppa:oreste-notelli/ppa
Update System:
$ sudo apt-get update
Install Justniffer tool:
$ sudo apt-get install justniffer
It failed to install in make then i run following command and try to reinstall service
$ sudoapt-get -f install
Examples
First of all verify installed version of Justniffer with -V option, you will need super user privileges to utilize that tool.
$ sudo justniffer -V
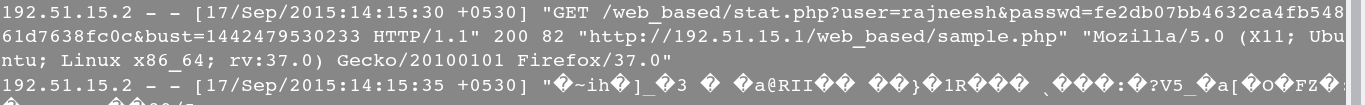
1. Dump Traffic to terminal in apache like format for eth1 interface, type
$ sudo justniffer -i eth1
Sample output:
2. You can trace running tcp stream with following option
$ sudo justniffer -i eth1 -r
Sample output:
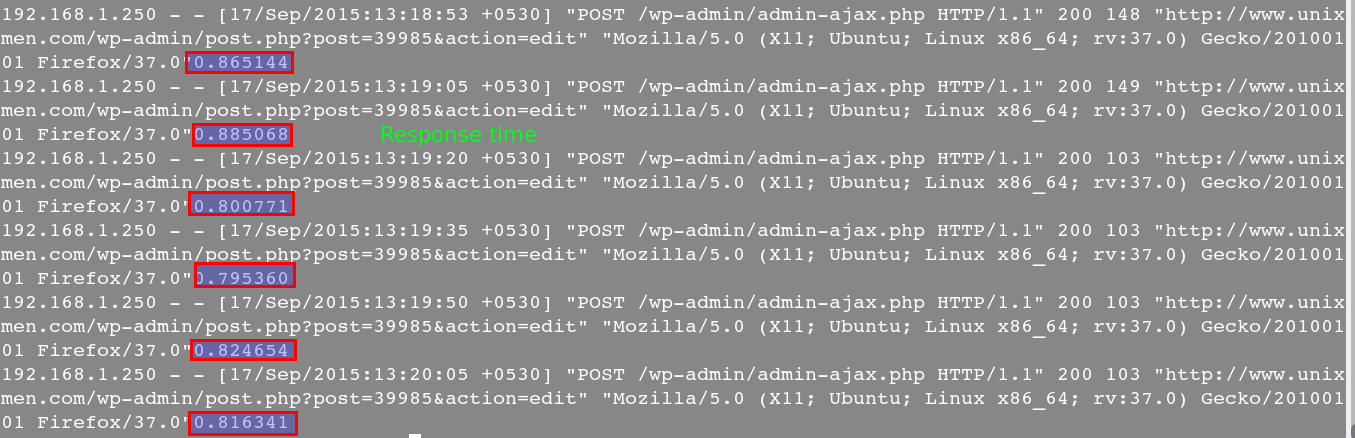
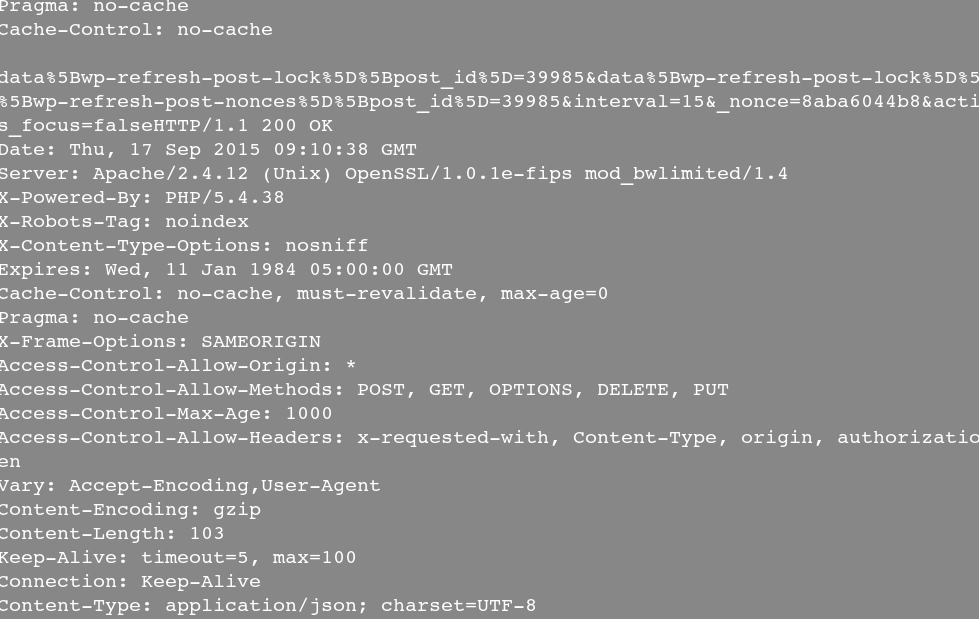
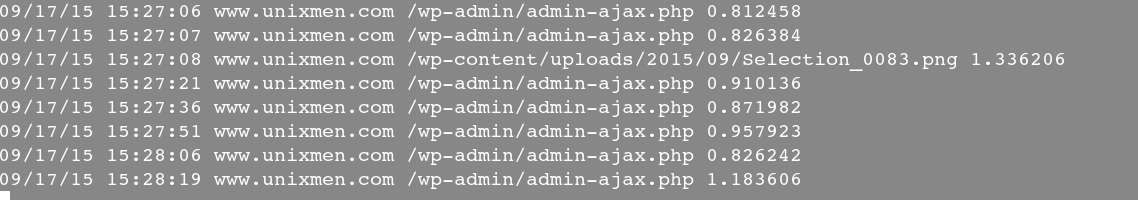
3. To get the response time of web server, type
$ sudo justniffer -i eth1 -a " %response.time"
Sample output:
4. Read a tcpdump captured file with Justniffer
First, capture traffic with tcpdump.
$ sudo tcpdump -w /tmp/file.cap -s0 -i eth0
Now access that data with justniffer
$ justniffer -f file.cap
Sample output:
5. Capture http only data
$ sudo justniffer -i eth1 -r -p "port 80 or port 8080"
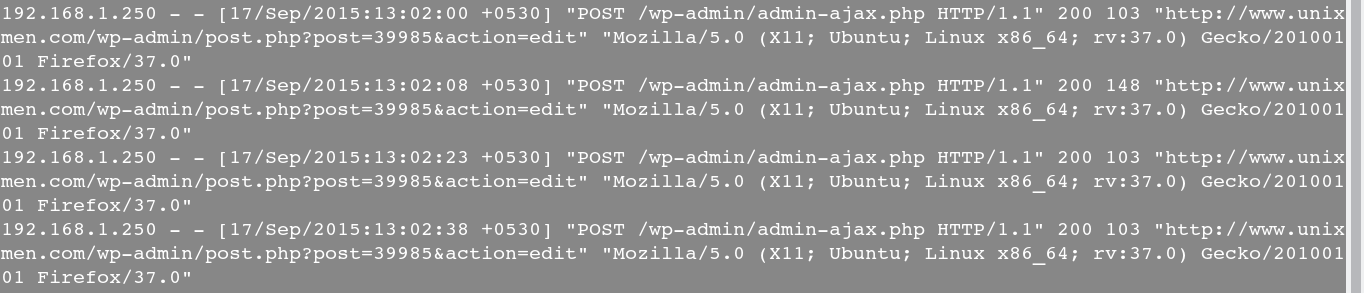
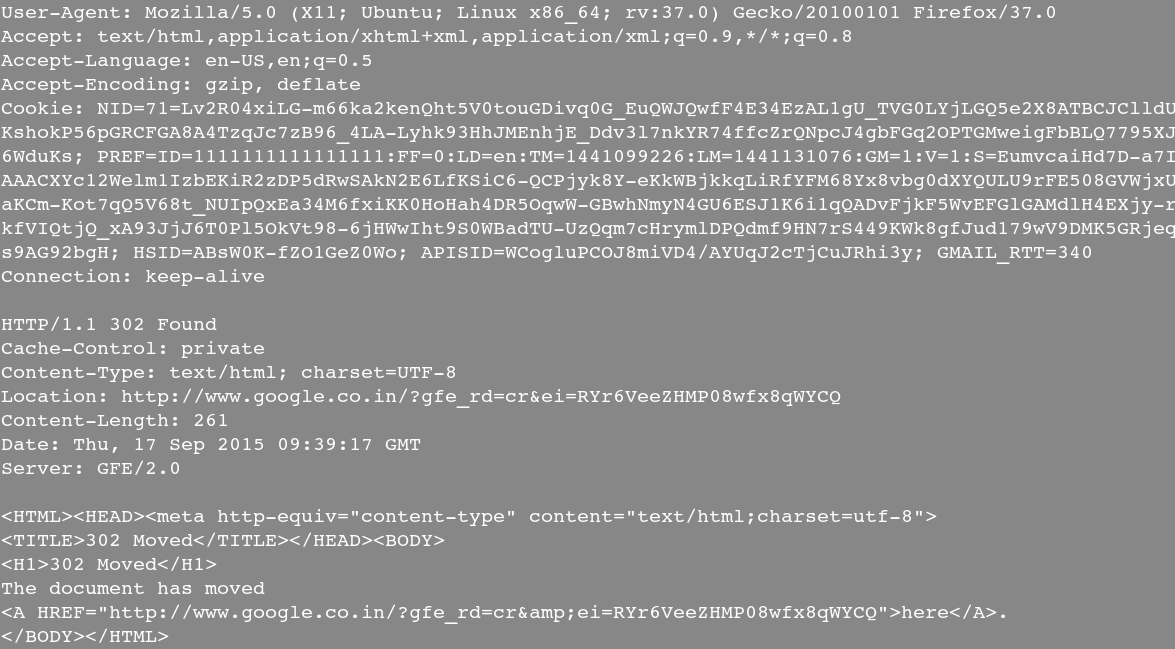
6. Get http only data from a specific host
$ justniffer -i eth1 -r -p "host 192.168.1.250 and tcp port 80"
Sample output:
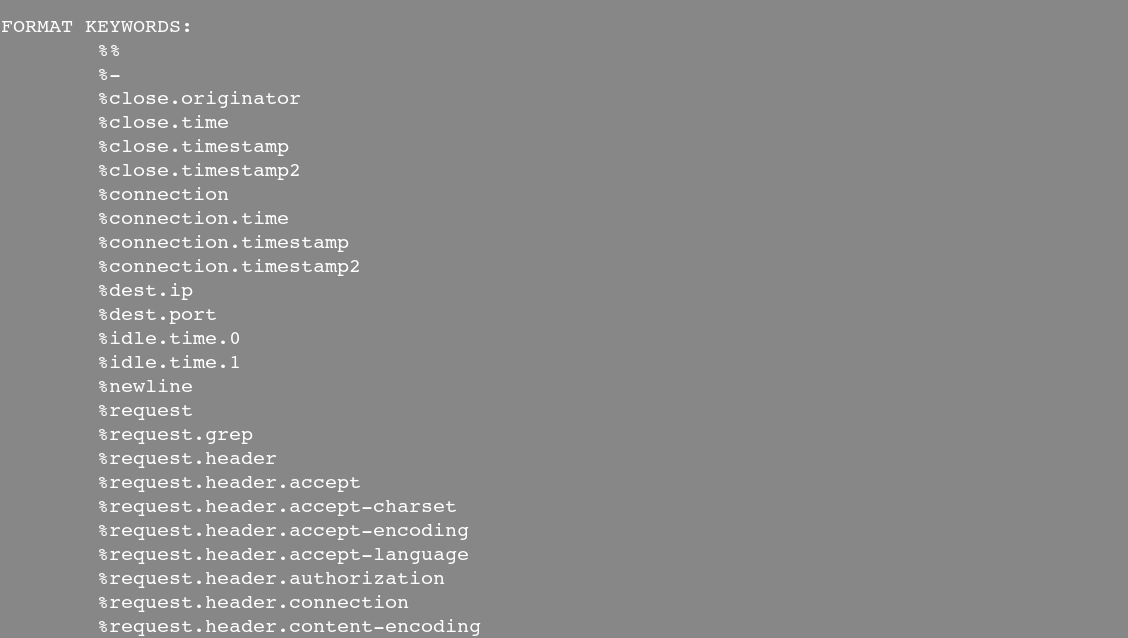
7. Capture data in a more preciser format
When you will type justniffer -h You will see a lots of format key words which help to get data in more preciser way
$ justniffer -h
Sample Output:
Let us retrieve data with some predefined parameter provided with justniffer
$ justniffer -i eth1 -l "%request.timestamp %request.header.host %request.url %response.time"