How to Run a Python Script: A Beginners Guide
What is a Python Script?
A Python script is a file containing Python code that can be executed. These files typically have a `.py` extension...
How to Uninstall NVIDIA Drivers
What are NVIDIA Drivers?
NVIDIA drivers are software packages that allow your operating system and programs to make the best use of your NVIDIA graphics...
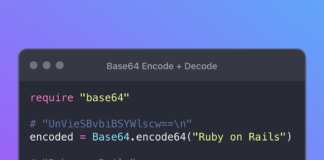
How to Decode Base64 Strings
What is Base64 Encoding?
Base64 is a binary-to-text encoding scheme that represents binary data in an ASCII string format. It's designed to carry data stored...
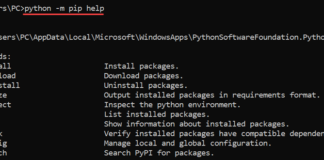
How to Update and Upgrade the Pip Command
So What exactly is Pip?
Pip, which stands for "Pip Installs Packages" or "Pip Installs Python," is the standard package manager for Python. It's an...
chmod 755: Understanding File Permissions
What is chmod 755?
The command `chmod 755` is a vital tool in Unix and Unix-like operating systems, used to set specific permissions on files...
When to Use the Grave Key
What is the Grave Key?
The grave key, also known as the backtick or backquote key, is a character (`) found on most computer keyboards....
How to Optimize WoW on Linux Using Open-Source Tools for the...
For those who are playing WoW on Linux, you are already on the right track. Linux is not only stable but also provides multiple...
Can You Play CS:GO on Linux?
Counter-Strike: Global Offensive (CS:GO) is one of the most popular first-person shooter games in the world, and many gamers are curious if it can...
Words after the Release of deepin 23
Dear deepin users and those who have yet to experience deepin on Linux,
After...
Bash String Comparison: Comparing Strings in Shell Scripts
String comparison is a crucial operation in bash scripting, essential for tasks ranging from simple conditional checks...
Bash Increment Variable: Increment and Decrement Variables
In the world of bash scripting, the ability to increment variables is a fundamental skill. Whether you're...
Bash Functions in Shell Scripts
Functions are a powerful feature in bash scripting that allow you to encapsulate and reuse code. By...
Bash Comments: Enhance Script Readability
Comments are an essential aspect of writing clean, maintainable, and understandable bash scripts. They provide valuable insights...
How to Create Binds in Linux for CS2
Binds have been a fundamental part of Counter Strike since its early versions, and their usefulness remains undeniable even with the release...
Challenges in Custom App Development
Building custom applications can be a complex and challenging endeavor. Developers often face a variety of obstacles,...
DD Command in Linux
The dd command is a powerful and versatile utility in Unix-like operating systems, including Linux. Often referred...
Bash Shebang: Using Script Interpreters
The shebang, also known as 'hashbang' or pound-bang, is a crucial element in Unix-like operating systems, including...
Sustainable Web Development: How Frontend Companies are Going Green
Frontend development company solutions that are eco-friendly are what the world is looking forward to. But in...