Unveiling the Life Stories of Linux Innovators
Linux, the open-source operating system that powers millions of devices worldwide, is a testament to the collaborative efforts of countless innovators. While the Linux...
5 Reasons to Switch to Remote Work of DevOps Engineers
Do you work in an office, but you would like to work from anywhere? This is quite real.If you are truly a professional in...
How To Setup A Proxy Server: A Beginner’s Guide For Linux...
So, you want to set up a proxy server on your Linux machine? That’s awesome!
6 Factors that Make Linux Important for your Small Business
A huge number of modern companies know about Linux firsthand. Many of them have been using various distributions in one form or another for...
Linux vs. Mac vs. Windows OS Guide
Linux, Windows, and MacOS are the three most prominent operating systems (OS) in the digital world, each...
Maximizing Your Security on Google Cloud: Essential Tips with Linux and...
Google Cloud is being extensively used by businesses to harness its capabilities as part of their cloud...
Unlock the Power Reverse Email Lookup With Linux: Improving Security and...
Email is a major communication mode in today’s digital era. Whether you use it for personal interactions,...
The Best VPN GUI For Linux
Setting up a VPN on Linux used to involve the terminal, Stack Overflow and a computer science degree. Nowadays, the process is a lot...
Leveraging Linux/Unix for Preventing Repeat Signups in E-commerce
E-commerce websites face a range of challenges, from managing inventory to ensuring secure transactions. One often-overlooked issue...
Bash Increment Variable: Increment and Decrement Variables
In the world of bash scripting, the ability to increment variables is a fundamental skill. Whether you're...
DevSecOps in Linux: Enhancing Security Without Compromising Agility
Does Linux help DevSecOps grow or is it DevSecOps that helps software development with Linux better? The relationship between Linux and security-fortified DevOps is...
A Guide To Implementing Segregation of Duties (SoD) in Linux Environments
In today's ever-evolving cyber threats, organizations must implement robust security measures that safeguard their valuable data and resources. One such essential measure is the...
Linux vs Windows: Here are 9 Most Essential Differences
Linux and Windows are the two most popular operating systems for personal computers. Both of the systems have different purposes and functionality. But each...
The Impact of Artificial Intelligence on Linux Security
Many computer users, especially those lacking tech-savvy, tend to believe that Linux is considerably more secure than...
How to Leverage Cybersecurity With Linux Systems
Linux is one of the operating systems such as Windows, Mac OS, and IOS. Linux also powers the Android system that most popular platforms...
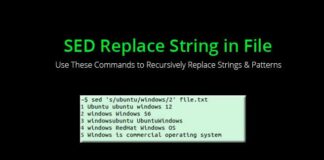
SED Replace: How to Manipulate Text in Unix
So, what is SED Replace?
SED stands for Stream Editor. This is a powerful...
3 Reasons Why Linux is the Best Choice to Achieve Optimal...
With technological advancements, hackers are becoming increasingly adept at identifying vulnerabilities and gaps in security systems. This makes unauthorized access to secure data and...
Crash Course on Organizing Your Workday on Linux
Crash Course on Organizing Your Workday on Linux
As a Linux distribution user,...