Ad Network vs. Ad Exchange: differences & similarities
Programmatic advertising is a great way to create influencing and profitable marketing campaigns. As this concept gains...
What are custom AdTech solutions?
Now that the world is firmly in a digital age, everything is starting to lean in that...
Tar Command in Linux: A Step-by-step Guide to Mastery
At Unixmen, we have been explaining each and every important Linux command in detail that would help...
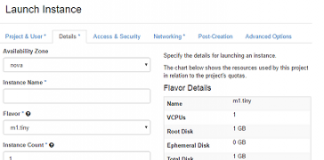
How To Create Instances (Virtual Machines) With External Network Connectivity In...
Hello Friends, today we will discuss how to create virtual machines (known as "instances" in openstack terminology) using Horizon Dashboard. We tested these steps...
6 Reasons to Pick Linux Over Windows
Almost all students do their work on laptops and PCs that run on Windows. Of course, some of you are lucky enough to afford...
A Guide to Using Bash Arrays: Examples
The Bourne Again Shell is the default shell on virtually every Linux distribution. While it's not as fleshed out as most programming languages, it...
35 Essential Linux Commands That Every User Should Know
For anyone working with Linux, having a solid understanding of essential commands is crucial for efficiently navigating and managing the system. Knowing how to...
The Importance of Linux in Developing Secure Medical Devices
Introduction
The use of open source software solutions, particularly for medical devices, is growing in popularity. Opеn source solutions provide a numbеr of benefits over...
A guide to app redesign: Making it evolve!
If you want your app to be a long-standing one, you should adapt it to the environment. Times change, and user tastes are changing...
IT Asset Management Software For Linux: Everything You Need to Know
Introduction to IT Asset Management Software
In today's digital age, managing IT assets efficiently...
How Threat Intelligence Reduces Cybercrime
Companies that perform most of their operations online risk being attacked by cybercriminals trying to steal their...
Untar tar.gz file: The Only How-to Guide You Will Need
If you are someone who works with so many files (especially compressed files), you will come across...
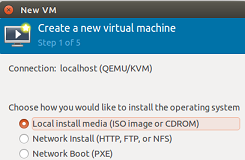
Install and Configure KVM (Kernel Based Virtual Machine) On Ubuntu Linux...
KVM (Kernel Based Virtual Machine) is a free virtualization tool which lets you create virtual machines on your host operating system. It works on...
5 Linux Cybersecurity Mistakes Small Businesses Commonly Make
Running a small business on Linux doesn’t mean having a small workload. You need to take care of so many things yourself or with...
Top 10 Linux Distros for Small Students
If your question is what is the best Linux distribution for small students? Then the answer would not be one. This is because of...
How Linux Users Can Protect Their Business
If your business uses Linux as an operating system, it is important that you know the best ways to protect your operations. Cybercrime is...
Ways to Enhance the Security of Your Linux Server
Security has always been the cornerstone of any Linux software. Since Linux is open-source software, people can audit code to find and patch any...
Proxy Servers that you can combine with Linux or Unix
Proxies, in their various forms, serve as vital intermediaries between your network and the websites or services you access. When it comes to choosing...