FreeIPA stands for Free Identity Policy Audit.
FreeIPA is a solution for managing users, groups, hosts, services, and much, much more. It uses open source solutions with some Python glue to make things work. Identity Management made easy for the Linux administrator.
Inside FreeIPA are some common pieces; The Apache Web Server, BIND, 389DS, and MIT Kerberos. Additionally, Dogtag is used for certificate management, and sssd for client side configurations. Put that all together with some python glue, and you have FreeIPA.
Installation
Installing FreeIPA is simple on a Linux system. However, there are a few things needed. This installation is being performed on a fully updated CentOS 7.0 system. An entry in the /etc/hosts matching the server ip and hostname is useful. Additionally, make sure to set the hostname properly.
echo 192.168.122.200 ipa7.example.com ipa7 >> /etc/hosts echo ipa7.example.com > /etc/hostname
This time, we will install Free IPA server. But there is a client server installation also. We will see that part on later posts. It’s recommended to use RHEL/CentOS >= 6.x or Fedora >= 14. Simply perform a yum install.
(rhel/centos) # yum install ipa-server (fedora) # yum install freeipa-server
Since FreeIPA can manage a dns server, a decision must be made. Here, we are going to choose to manage our internal dns with FreeIPA, which uses ldap via 389DS to store the records.
yum install bind-dyndb-ldap
ipa-server-install --setup-dns
The log file for this installation can be found in /var/log/ipaserver-install.log ============================================================================== This program will set up the IPA Server. This includes: * Configure a stand-alone CA (dogtag) for certificate management * Configure the Network Time Daemon (ntpd) * Create and configure an instance of Directory Server * Create and configure a Kerberos Key Distribution Center (KDC) * Configure Apache (httpd) * Configure DNS (bind) To accept the default shown in brackets, press the Enter key. WARNING: conflicting time&date synchronization service 'chronyd' will be disabled in favor of ntpd Existing BIND configuration detected, overwrite? [no]: yes
Next, define the server hostname, and the domain name (for DNS).
Enter the fully qualified domain name of the computer on which you're setting up server software. Using the form <hostname>.<domainname> Example: master.example.com. Server host name [ipa7.example.com]: ipa7.example.com Warning: skipping DNS resolution of host ipa7.example.com The domain name has been determined based on the host name. Please confirm the domain name [example.com]: example.com
Next section covers the kerberos realm, This may seem confusing, but kerberos is one of the most important thing behind FreeIPA. It makes registering client systems very simple. Kerberos realm names are always in upper case. Usually, they emulate the domain name.
The kerberos protocol requires a Realm name to be defined. This is typically the domain name converted to uppercase. Please provide a realm name [EXAMPLE.COM]: EXAMPLE.COM
Next step is configure the passwords for the Directory Manager (for ldap administration) and the IPA admin user.
Certain directory server operations require an administrative user. This user is referred to as the Directory Manager and has full access to the Directory for system management tasks and will be added to the instance of directory server created for IPA. The password must be at least 8 characters long. Directory Manager password: manager72 Password (confirm): manager72 The IPA server requires an administrative user, named 'admin'. This user is a regular system account used for IPA server administration. IPA admin password: ipaadmin72 Password (confirm): ipaadmin72
Next, the installer will asks for more DNS info.
Do you want to configure DNS forwarders? [yes]: yes Enter the IP address of DNS forwarder to use, or press Enter to finish. Enter IP address for a DNS forwarder: 8.8.8.8 DNS forwarder 8.8.8.8 added Enter IP address for a DNS forwarder: 8.8.4.4 DNS forwarder 8.8.4.4 added Enter IP address for a DNS forwarder: <enter> Do you want to configure the reverse zone? [yes]: yes Please specify the reverse zone name [122.168.192.in-addr.arpa.]: 122.168.192.in-addr.arpa Using reverse zone 122.168.192.in-addr.arpa.
Now, Our part is completed, Installer will do the rest. A verification step prints out all of the values entered. Make sure to review them carefully.
The IPA Master Server will be configured with: Hostname: ipa7.example.com IP address: 192.168.122.200 Domain name: example.com Realm name: EXAMPLE.COM BIND DNS server will be configured to serve IPA domain with: Forwarders: 8.8.8.8, 8.8.4.4 Reverse zone: 122.168.192.in-addr.arpa.
Now take some rest, Installation takes anywhere from 10-30 minutes.
Continue to configure the system with these values? [no]: yes The following operations may take some minutes to complete. Please wait until the prompt is returned. Configuring NTP daemon (ntpd) [1/4]: stopping ntpd [2/4]: writing configuration [3/4]: configuring ntpd to start on boot [4/4]: starting ntpd .......
When complete, the installation gives some of useful information about the ports which should be opened.
Setup complete Next steps: 1. You must make sure these network ports are open: TCP Ports: * 80, 443: HTTP/HTTPS * 389, 636: LDAP/LDAPS * 88, 464: kerberos * 53: bind UDP Ports: * 88, 464: kerberos * 53: bind * 123: ntp 2. You can now obtain a kerberos ticket using the command: 'kinit admin' This ticket will allow you to use the IPA tools (e.g., ipa user-add) and the web user interface. Be sure to back up the CA certificate stored in /root/cacert.p12 This file is required to create replicas. The password for this file is the Directory Manager password
Configure the firewall:
firewall-cmd --permanent --add-service=ntp firewall-cmd --permanent --add-service=http firewall-cmd --permanent --add-service=https firewall-cmd --permanent --add-service=ldap firewall-cmd --permanent --add-service=ldaps firewall-cmd --permanent --add-service=kerberos firewall-cmd --permanent --add-service=kpasswd
use authconfig to ensure home directories are created. Followed by a quick reboot.
authconfig --enablemkhomedir --update chkconfig sssd on Note: Forwarding request to 'systemctl enable sssd.service'. init 6
Logging into FreeIPA can be done in two different ways; from the browser, or via kerberos. For now, login via the web browser as the admin user.
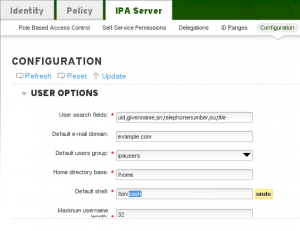
After login, we need to Change the default shell for all users to /bin/bash. This is done by choosing IPA Server ->Configuration. Once modified, click Update.
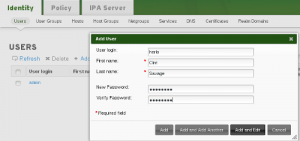
Now it’s time to add a user. Choose the Identity tab. Then click Add.
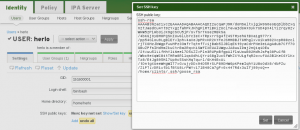
Clicking Add and Edit presents the user’s data. This is useful for adding an ssh key.
Don’t forget to click Update after setting the key.
This will now allow ssh into the FreeIPA server as the new user. For this we should configured the FreeIPA server as a resolver. The simplest way is to update the /etc/resolv.conf file.
cat /etc/resolv.conf
search egavas.org nameserver 192.168.122.200 ......
host ipa7.example.com
ipa7.example.com has address 192.168.122.200
Once the FreeIPA server is resolvable, ssh will now work.
[jijoo@x220 ~]$ ssh ipa7.example.com The authenticity of host 'ipa7.example.com (192.168.122.200)' can't be established. ECDSA key fingerprint is 42:96:09:a7:1b:ac:df:dd:1c:de:73:2b:86:51:19:b1. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'ipa7.example.com' (ECDSA) to the list of known hosts. Creating home directory for herlo. Last login: Thu Jan 8 02:27:44 2014 from 112.133.198.126 [jijo@ipa7 ~]$ id uid=151600001(herlo) gid=151600001(herlo) groups=151600001(herlo) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c102
Well Done, The FreeIPA server is now configured.
Cheers!!
See you guys with next post.