Introduction
Sftp (SSH or Secure file transfer protocol, Instead of using vsftpd we can use sftp, Sftp is the only secure way while comparing to vsftpd. Sftp performs all operations over an encrypted ssh Connection. It has the features of using ssh public key authentication and more as like ssh. If a user only allowed to access his files without ssh shell access we can create a chroot environment for those user’s. While chroot enabled user’s will be jailed into there own home directory. Let we see how to setup a Sftp in RHEL/Centos 7
My Environment Setup:
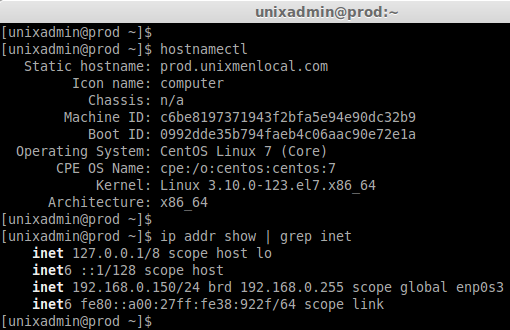
Hostname : prod.unixmen.com
IP address : 192.168.0.150
hostnamectl
ip addr show | grep inet
Step 1: create a group for SFTP
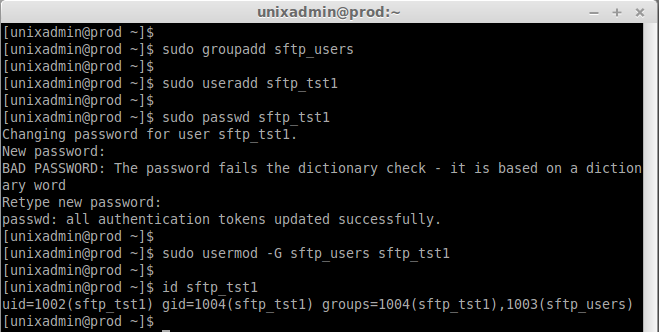
First we need to create a group for sftp, Let we create a sftp group in the name of sftp_users and add the user’s to sftp group.
sudo groupadd sftp_users
Let we create one user in our server for testing purpose, Then join the created user to sftp group.
sudo useradd sftp_tst1
sudo passwd sftp_tst1
sudo usermod -G sftp_users sftp_tst1
id sftp_tst1
Step 2: Sftp Configuration changes.
Edit the sshd config to configure the sftp.
sudo vim /etc/ssh/sshd_config
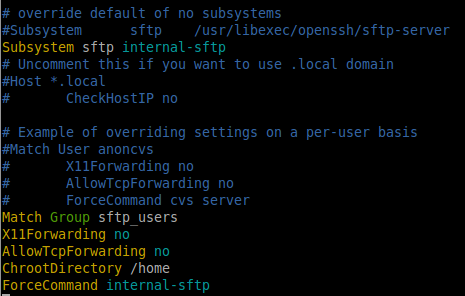
In Line 147, Comment the Existing line, Yank the line for additional configurations.
Subsystem sftp /usr/libexec/openssh/sftp-server
Remove the /usr/libexec/openssh/sftp-server and add internal-sftp in Yanked Line.
Subsystem sftp internal-sftp
Add the below content to the end of file to add the sftp chroot environment. By default there will come some line’s exisits, Overide the default by adding the below configs.
Match Group sftp_users X11Forwarding no AllowTcpForwarding no ChrootDirectory /home ForceCommand internal-sftp
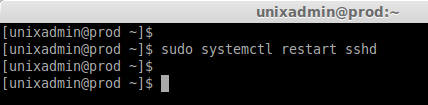
Restart the sftp by restarting sshd service.
sudo systemctl restart sshd
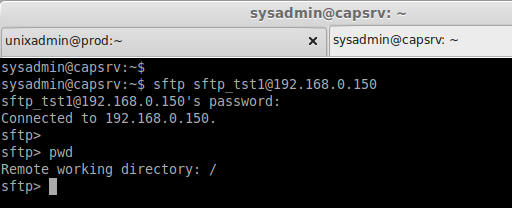
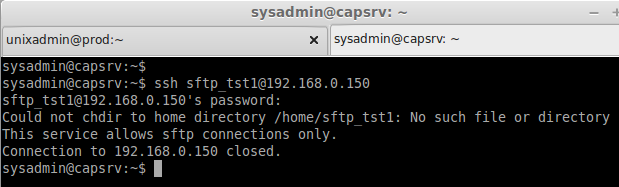
Check the sftp from any Client machines. This will only allow the sftp connections. If we try to connect ssh it won’t allow us to get connect.
sftp sftp_tst1@192.168.0.150
ssh sftp_tst1@192.168.0.150
Above we can see the user sftp_tst1 defined only to use sftp, He can’t access the ssh. That’s it we have configured a secure way to transfer files using sftp.
Conclusion
Many of them used to wonder how to give only ftp access for specified unprivileged user’s. For that we can configure sftp (Secured) instead of using ftp (Unsecured). Above setup have defined using Chroot so that particular user jailed into his home directory.