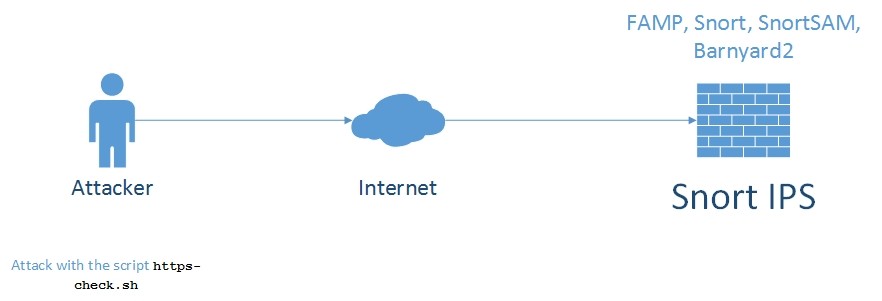
The topology will be as follows:
Apache, MySQL and PHP already installed and configured.
In /usr/local/etc/php.ini file configure the following lines:
<strong>date.timezone = 'Asia/Baku'</strong>
<strong>include_path = ".:/usr/local/share/pear:/usr/local/share/fpdf"</strong>
# Install
# create folder which we will download the rules
# Enter the folder
Register in site http://snort.org, and then download snortrules-snapshot-2970.tar.gz file to our server folder /root/snortrules:
# extract the rules
Move the rules to the necessary address:
When configure BARNYARD2 we will need ‘sid-msg.map’ and ‘gen-msg.map’ files. So we copy that before to the ‘/usr/local/etc/snort’ folder.
<strong>cp /usr/ports/security/snort/work/snort-2.9.7.0/etc/gen-msg.map /usr/local/etc/snort</strong>
turn off USBUS interface, because when SNORT will sniff the network it will use first interface usbus0 device and after that will output error. You must reboot after it:
<strong>touch /usr/local/etc/snort/rules/blacklist.rules</strong>
# Create needed files.
# Create needed files.
If we want to start snort with different user, we must create it before:
Username: <strong>snort</strong>
Full name: <strong>Snort IPS User</strong>
Uid (Leave empty for default): <strong>1003</strong>
Login group [snort]:
Login group is snort. Invite snort into other groups? []:
Login class [default]:
Shell (sh csh tcsh nologin) [sh]: <strong>nologin</strong>
Home directory [/home/snort]:
Home directory permissions (Leave empty for default):
Use password-based authentication? [yes]: <strong>no</strong>
Lock out the account after creation? [no]: <strong>no</strong>
Username : <strong>snort</strong>
Password : <strong><disabled></strong>
Full Name : <strong>Snort IPS User</strong>
Uid : <strong>1003</strong>
Class :
Groups : <strong>snort</strong>
Home : <strong>/home/snort</strong>
Home Mode :
Shell : <strong>/usr/sbin/nologin</strong>
Locked : <strong>no</strong>
# Change user and group for snort folder.
start configuration of /usr/local/etc/snort/snort.conf file:
# Declare Local Subnets in variable.
The same as in the ‘/usr/local/etc/snort/snort.conf’ file for simple rules, so-rules and preproc-rules edit and change the path. Do not forget that all error logs are collected in ‘/var/log/messages’ file.
<strong>var SO_RULE_PATH ./so_rules</strong>
<strong>var PREPROC_RULE_PATH ./preproc_rules</strong>
<strong>var WHITE_LIST_PATH ./rules</strong>
<strong>var BLACK_LIST_PATH ./rules</strong>
Set path for Dynamic preprocessor engine and detector:
<strong>dynamicengine /usr/local/lib/snort_dynamicengine/libsf_engine.so</strong>
<strong>dynamicdetection directory /usr/local/lib/snort_dynamicrules</strong>
# Create needed folder
Note: If in the folder is not found any file, we must copy needed files with command below:
<strong>preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/*</strong> <strong>/usr/local/lib/snort_dynamicpreprocessor</strong>
You can also find dynamic engine file from this path /usr/ports/security/snort/work/snort-2.9.7.0/src/dynamic-plugins/sf_engine/.libs/libsf_engine.so
whitelist $WHITE_LIST_PATH/whitelist.rules, # change the name of white_list.rules file to whitelist.rules
blacklist $BLACK_LIST_PATH/blacklist.rules # change the name of black_list.rules to blacklist.rules. Save the snort.conf file and exit.
We also find the line below in the file /usr/local/etc/snort/snort.conf and add comment before the line because, we do not need local rules:
And at the end before all includes we must set output unified2 as below (You must delete nostamp):
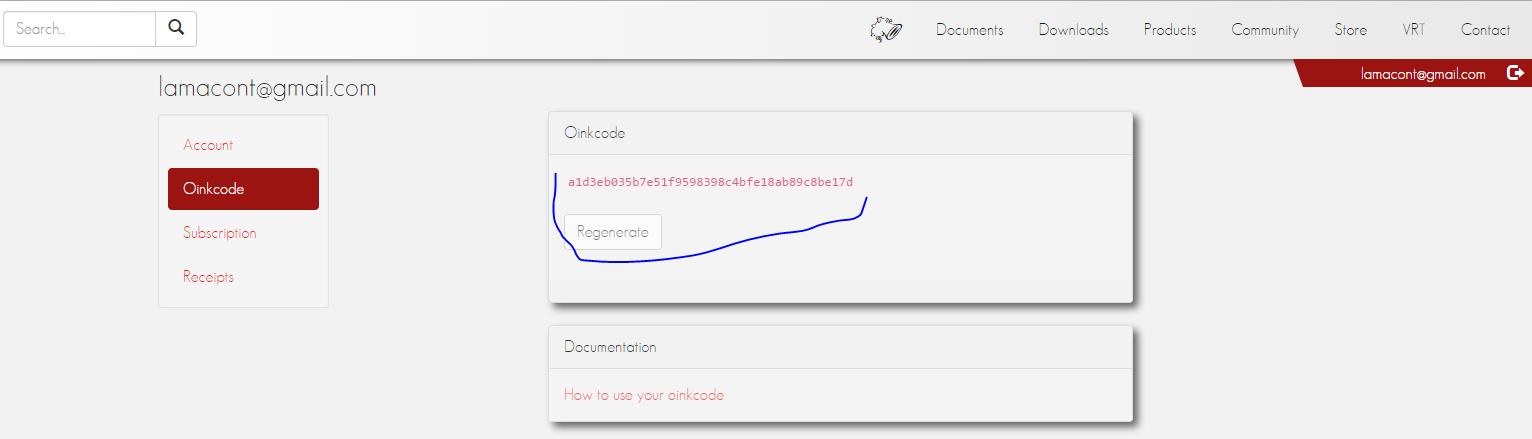
This is needed for autoupdate snort rules. But you must register in the http://snort.org site to get oinkcode because, it will be needed for update in our url link.
# Enter the port
# Install
# Turn off certificate checking for WGET
In the file /usr/local/bin/oinkmaster find the address that the following lines are in it:
# Make sure all urls look ok, and untaint them.
$#{$config{url}} = -1;
foreach my $url (@urls) {
clean_exit("incorrect URL: "$url"")
<strong># Delete the line and,</strong>
<strong>unless ($url =~ /^((?:https*|ftp|file|scp):\/\/.+\.(?:tar\.gz|tgz))$/ || $url =~ /^(dir:\/\/.+)/);</strong><strong> </strong>
<strong># Add this line</strong>
<strong> unless ($url =~ m,(http.*?://([^\s)"](?!ttp:))+),g); </strong>
my $ok_url = $1;
Prepare master configuration file for OinkMaster. But you must get generated code for OinkCode, from your registered account(As the print screen):
I must say that, the pathes of rules shown in URL starting with the name snortrules-snapshot-2970.tar.gz. You must take the number 2970 from Snort version, in order to match. You can get the version with the following command:
,,_ -*> Snort! <*-
o" )~ <strong>Version 2.9.7.0</strong> GRE (Build 149) FreeBSD
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.4.0
Using PCRE version: 8.35 2014-04-04
Using ZLIB version: 1.2.8
# Configuration file will be as follows
<strong>path = /bin:/usr/bin:/usr/local/bin</strong>
<strong>tmpdir = /home/oinkmaster/tmp/</strong>
<strong>update_files = \.rules$|\.config$|\.conf$|\.txt$|\.map$</strong>
<strong>skipfile local.rules</strong>
<strong>skipfile deleted.rules</strong>
<strong>skipfile snort.conf</strong>
# Create temp folder
We will need the makesidex.pl file for signature maps and configuration. For that do the following steps:
<strong>chmod 700 /usr/local/etc/snort/makesidex.pl</strong>
# Set as executable
In the end test updates:
Loading /usr/local/etc/oinkmaster.conf
Loading /usr/local/etc/autodisable.conf
Downloading file from http://www.snort.org/rules/snortrules-snapshot-2970.tar.gz?oinkcode=a1d3eb035b7e51f9598398c4bfe18ab89c8be17d... done.
Archive successfully downloaded, unpacking... done.
Setting up rules structures... done.
Processing downloaded rules... disabled 0, enabled 0, modified 0, total=21885
Setting up rules structures... done.
Comparing new files to the old ones... done.
[***] Results from Oinkmaster started 20141027 23:22:35 [***]
[*] Rules modifications: [*]
None.
[*] Non-rule line modifications: [*]
None.
[*] Added files: [*]
None.
For automatization our jobs we must add 5:30 schedule every morning to the /etc/crontab file(restart the cron daemon):
# Snort Rules Update
# Restart the daemon
We try to start snort from the Console. But don’t forget to check existing of /var/log/snort folder before. If it is not exist you must create.
<strong>echo 'snort_enable="YES"'>> /etc/rc.conf</strong>
# Add snort to startup
## You can also add lines below to /etc/rc.conf file.
## But in my situation I used just line before.
## Don’t forget, in my situation snort listened on all interfaces
#<strong>snort_conf="/usr/local/etc/snort/snort.conf"</strong>
#<strong>snort_group="snort"</strong>
#<strong>snort_flags="-D -q"</strong>
# Start the snort
1278 - Ss 0:09.78 <strong>/usr/local/bin/snort -D -q -c /usr/local/etc/snort/snort.conf</strong>
Remember, if snort doesn’t start you can find error logs from the /var/log/messages file. You can find answer of all problems from this file.
Note: If you remember, i said that in the /usr/local/etc/snort/snort.conf configuration file the limit of log file will reach 32Mb it will create new one. This is not in rotation and one time will take all space in your file system. Before set to cron and remove log files we must detect handle time approximately. For example interval for 15 days was normal for me.
Add the following lines to the /etc/crontab file, for clean snort alert logs each 15 days:
# Snort Alert logs clean
And now connect Snort from Barnyard2 to MySQL database:
Barnyard takes alerts from Snort logs and insert them to MySQL database:
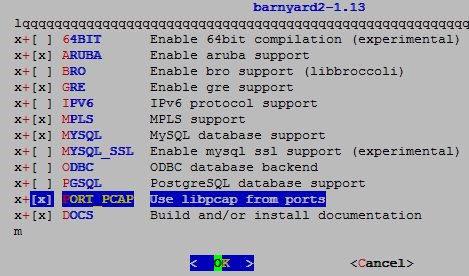
# Go to the port folder
But if we want, we can also start barnyard with different username. For that you must do the following steps:
## Add to the system user ‘barny’ with the 999 UID and GID.
Full name: <strong>Barnyard user for Snort</strong>
Uid (Leave empty for default): <strong>999</strong>
Login group [barny]:
Login group is barny. Invite barny into other groups? []:
Login class [default]:
Shell (sh csh tcsh nologin) [sh]: <strong>nologin</strong>
Home directory [/home/barny]:
Home directory permissions (Leave empty for default):
Use password-based authentication? [yes]: <strong>no</strong>
Lock out the account after creation? [no]:
Username : <strong>barny</strong>
Password : <strong><disabled></strong>
Full Name : <strong>Barnyard user for Snort</strong>
Uid : <strong>999</strong>
Class :
Groups : <strong>barny</strong>
Home : <strong>/home/barny</strong>
Home Mode :
Shell : <strong>/usr/sbin/nologin</strong>
Locked : <strong>no</strong>
OK? (yes/no): <strong>yes</strong>
# Create log folder for Barnyard2.
# Create the file.
## Set access for Snort and barny for both logs.
<strong>chmod -R 770 /var/log/barnyard2/</strong>
<strong>chown -R barny:snort /var/log/snort</strong>
<strong>chmod -R 770 /var/log/snort</strong>
<strong>touch /var/log/snortsnort.log</strong>
<strong>chown snort:barny /var/log/snortsnort.log</strong>
We also add the line below to the cron schedule to work each 1 minute. Because when each log is created, this will take owning of root user and snort group.
# Snort logs chown
# Restart the service
Create database for barnyard:
# Connect to MySQL with root username and create database, login and password. Also grant access.
<strong>GRANT ALL PRIVILEGES ON snort.* TO 'snort'@'localhost' IDENTIFIED BY 'freebsd';</strong>
<strong>FLUSH PRIVILEGES;</strong>
Create structure for Barnyard in MySQL:
our configuration file /usr/local/etc/barnyard2.conf will be as follows:
<strong>config reference_file: /usr/local/etc/snort/reference.config</strong>
<strong>config classification_file: /usr/local/etc/snort/classification.config</strong>
<strong>config gen_file: /usr/local/etc/snort/gen-msg.map</strong>
<strong>config sid_file: /usr/local/etc/snort/sid-msg.map</strong>
config event_cache_size: 4096
config logdir: /var/log/barnyard2
output alert_fast
config hostname: IT_VPS
config interface: em0
config alert_with_interface_name
config daemon
config set_gid: 999
config set_uid: 999
config waldo_file: /var/log/snort/barnyard2.waldo
input unified2
output alert_fast
output log_tcpdump: tcpdump.log
# To connect Barnyard to our database configuration line is as follows
# And this line is for connecting to SnortSAM and when its time will come we will delete comment before line
#Here it means connect to the localhost and port 777 with 123 password
Check the starting of Barnyard:
# Add Barnyard to startup
<strong>barnyard2_conf="/usr/local/etc/barnyard2.conf" </strong>
# Start the Barnyard
# Check PID of Barnyard
Remember, if snort doesn’t start you can find error logs from the /var/log/messages file. You can find answer of all problems from this file. The successful result from /var/log/messages file is as follows:
Oct 28 03:25:44 snort barnyard2[1439]: database: compiled support for (mysql)
Oct 28 03:25:44 snort barnyard2[1439]: database: configured to use mysql
Oct 28 03:25:44 snort barnyard2[1439]: database: schema version = 107
Oct 28 03:25:44 snort barnyard2[1439]: database: host = localhost
Oct 28 03:25:44 snort barnyard2[1439]: database: user = snort
Oct 28 03:25:44 snort barnyard2[1439]: database: database name = snort
Oct 28 03:25:44 snort barnyard2[1439]: database: sensor name = IT_VPS:em0
Oct 28 03:25:44 snort barnyard2[1439]: database: sensor id = 1
Oct 28 03:25:44 snort barnyard2[1439]: database: sensor cid = 3
Oct 28 03:25:44 snort barnyard2[1439]: database: data encoding = hex
Oct 28 03:25:44 snort barnyard2[1439]: database: detail level = full
Oct 28 03:25:44 snort barnyard2[1439]: database: ignore_bpf = no
Oct 28 03:25:44 snort barnyard2[1439]: database: using the “log” facility
Oct 28 03:25:44 snort barnyard2[1439]:
Oct 28 03:25:44 snort barnyard2[1439]: –== Initialization Complete ==–
Oct 28 03:25:44 snort barnyard2[1439]: Barnyard2 initialization completed successfully (pid=1439)
Oct 28 03:25:44 snort barnyard2[1439]: Using waldo file ‘/var/log/snort/barnyard2.waldo’: spool directory = /var/log/snort spool filebase = snort.log time_stamp = 1414447356 record_idx = 0
Oct 28 03:25:44 snort barnyard2[1439]: Opened spool file ‘/var/log/snort/snort.log.1414447356’
Oct 28 03:25:44 snort barnyard2[1439]: Closing spool file ‘/var/log/snort/snort.log.1414447356’. Read 0 records
Oct 28 03:25:44 snort barnyard2[1439]: Opened spool file ‘/var/log/snort/snort.log.1414451087’
Oct 28 03:25:47 snort barnyard2[1439]: Waiting for new data
Note: Usually this problem appears when restart MySQL and Barnyard2 have not access to own PID file. We must restart Barnyard when we restart MySQL. Just delete PID files as it is shown below and start Barnyard again.
# Delete PID files
And now let’s install Snorby WEB interface:
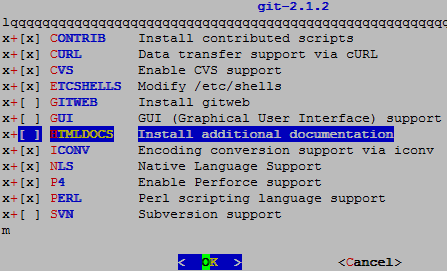
Snorby was written in Ruby-Rails programing language. And for it we must install ruby1.9: because Snorby needs only it(This will not work with 2.0 version):
# snorby needs this port
# install
After installation it will write binary files as pathes below:
<strong>/usr/local/bin/wkhtmltopdf</strong>
# Set Ruby version before
# We don’t need X.
# Go to the port
# Install
# Go to the port
# Install
After installation binary file will be written to the /usr/local/bin/gem19 path.
# Go to the GIT port
# Install
Continue installation:
/usr/local/bin/gem install prawn –no-rdoc –no-ri
/usr/local/bin/gem install rake -v 0.8.7 –no-rdoc –no-ri
/usr/local/bin/gem install rails –no-rdoc –no-ri
/usr/local/bin/gem install mysql –no-rdoc –no-ri
/usr/local/bin/gem install passenger –no-rdoc –no-ri
/usr/local/bin/passenger-install-apache2-module -a
After the installation the following lines in the /usr/local/etc/apache24/httpd.conf configuration file add after the last line of LoadModule directive:
<strong> <IfModule mod_passenger.c></strong>
<strong> PassengerRoot /usr/local/lib/ruby/gems/1.9/gems/passenger-4.0.53</strong>
<strong> PassengerDefaultRuby /usr/local/bin/ruby19</strong>
<strong></IfModule></strong>
# Restart the Daemon for commit changes.
# Create Public_HTML folder for Snorby
# Go to the folder
# Download snorby archived file
# Extract the file
# Copy the files to snorby folder
# Remove the zip file
# Remove extracted fodler
# Change owner and group of folder to www
# This command will download needed packets to the /usr/local/www/snorby/vendor/cache
# Install downloaded packets
Then copy the configuration files from sample to original:
cp /usr/local/www/snorby/config/snorby_config.yml.example /usr/local/www/snorby/config/snorby_config.yml
cp /usr/local/www/snorby/config/database.yml.example /usr/local/www/snorby/config/database.yml
Note: I detected a problem here. When Snorby tried to start it was warning snort database structure in MySQL. And that is why I had to create a new snorby database and connect to the barnyard.
# Login to the MySQL and create the database
# Create the database
# Grant access to database with username, host and password
<strong>FLUSH PRIVILEGES;</strong>
Change the /usr/local/www/snorby/config/snorby_config.yml configuration file as follows:
<strong> domain: 'localhost:3000'</strong>
<strong> wkhtmltopdf: /usr/local/bin/wkhtmltopdf</strong>
<strong> ssl: false</strong>
<strong> mailer_sender: 'snorby@snorby.org'</strong>
<strong> geoip_uri: "http://geolite.maxmind.com/download/geoip/database/GeoLiteCountry/GeoIP.dat.gz"</strong>
<strong> rules:</strong>
<strong> - "/usr/local/etc/snort/rules"</strong>
<strong> - "/usr/local/etc/snort/so_rules"</strong>
<strong> - "/usr/local/etc/snort/preproc_rules"</strong>
<strong> authentication_mode: database</strong>
<strong> time_zone: 'AZST'</strong>
<strong>development:</strong>
<strong> domain: localhost:3000</strong>
<strong> wkhtmltopdf: /Users/mephux/.rvm/gems/ruby-1.9.2-p0/bin/wkhtmltopdf</strong>
<strong> ssl: false</strong>
<strong> mailer_sender: 'snorby@snorby.org'</strong>
<strong> geoip_uri: "http://geolite.maxmind.com/download/geoip/database/GeoLiteCountry/GeoIP.dat.gz"</strong>
<strong> rules:</strong>
<strong> - "/Users/mephux/.snort/rules"</strong>
<strong> - "/Users/mephux/.snort/so_rules"</strong>
<strong> authentication_mode: database</strong>
<strong>test:</strong>
<strong> domain: localhost:3000</strong>
<strong> wkhtmltopdf: /usr/local/bin/wkhtmltopdf</strong>
<strong> mailer_sender: 'snorby@snorby.org'</strong>
<strong> geoip_uri: "http://geolite.maxmind.com/download/geoip/database/GeoLiteCountry/GeoIP.dat.gz"</strong>
<strong> authentication_mode: database</strong>
The configuration file /usr/local/www/snorby/config/database.yml for database will be as follows:
<strong> adapter: mysql</strong>
<strong> username: snorby</strong>
<strong> password: "freebsd" # Example: password: "s3cr3tsauce"</strong>
<strong> host: localhost</strong>
development:
database: snorby
<<: *snorby
test:
database: snorby
<<: *snorby
production:
database: snorby
<<: *snorby
If you want to configure mail, you can change the /usr/local/www/snorby/config/initializers/mail_config.rb file as lines below. For example configuration of Gmail.
# Snorby Mail Configuration
# #
# Gmail Example:
#
# ActionMailer::Base.delivery_method = :smtp
# ActionMailer::Base.smtp_settings = {
# :address => “smtp.gmail.com”,
# :port => 587,
# :domain => “snorby.org”,
# :user_name => “snorby”,
# :password => “snorby”,
# :authentication => “plain”,
# :enable_starttls_auto => true
# }
# #
# Sendmail Example:
#
# ActionMailer::Base.delivery_method = :sendmail
# ActionMailer::Base.sendmail_settings = {
# :location => ‘/usr/sbin/sendmail’,
# :arguments => ‘-i -t’
<strong>ActionMailer::Base.raise_delivery_errors = true</strong>
# Mail.register_interceptor(DevelopmentMailInterceptor) if Rails.env.development?
At the end start.
# Enter the address and start
Jammit Warning: Asset compression disabled — Java unavailable.
No time_zone specified in snorby_config.yml; detected time_zone: Asia/Baku
97c2e4924cd06a2ebec95759dfce4292e70c0dd816c90f8eb80b7c7c8da3fe56b6f702fa548170d3dd2bf30842970e1 0903a1039f2f09b6819ca26043989b049
# Don’t look at error because we have already created the database.
ERROR 1007 (HY000) at line 1: Can’t create database ‘snorby’; database exists
[datamapper] Finished auto_upgrade! for :default repository ‘snorby’
[~] Adding `index_timestamp_cid_sid` index to the event table
[~] Adding `index_caches_ran_at` index to the caches table
[~] Adding `id` to the event table
[~] Building `aggregated_events` database view
[~] Building `events_with_join` database view
* Removing old jobs
* Starting the Snorby worker process.
Jammit Warning: Asset compression disabled — Java unavailable.
* Adding jobs to the queue
# Change owner and group to www
# We can start Bu emr ile production server from console by this command. But we will do it from apache.
Before we will create for that virtualhost in apache configuration and then will add needed port for listen to apache configuration file:
Add the lines below to /usr/local/domen/snorby.atl.az file:
<strong> ServerAdmin webmaster@localhost</strong>
<strong> DocumentRoot "/usr/local/www/snorby/public"</strong>
<strong> ServerName snorby.atl.az</strong>
<strong> ServerAlias www.snorby.atl.az</strong>
<strong> <Directory "/usr/local/www/snorby/public"></strong>
<strong> AllowOverride all</strong>
<strong> Options -MultiViews</strong>
<strong> Require all granted</strong>
<strong> </Directory></strong>
<strong></VirtualHost></strong>
In the /usr/local/etc/apache24/httpd.conf configuration file, after Listen 80 directive add new listen directive to start snorby as below:
<strong>Listen 3000</strong>
# At the end restart the web server
At last go to this link http://snorby.atl.az:3000/users/login get the page below:
Username: snorby@snorby.org
Pass: snorby
If login successfully the following page will be shown:
Before all you must change the password:
And we see that there is nothing in the logs. Because, as I said before snorby didn’t want to work without creating database and so I had to create a database named snorby, in order to connect and write there. And that is why we can’t see the barnyard’s logs. And it means that now in real there is no connection between snorby and snort in database. Let’s fix it. Login to MySQL and add needed access:
# Login to MySQL with root account and grant access to barnyard for snorby database. After flush privileges for commit changes.
<strong>FLUSH PRIVILEGES;</strong>
Also in the /usr/local/etc/barnyard2.conf configuration file change the line below to connect to the snorby database:
# Stop the barnyard
# Start the barnyard
Analyze the /var/log/messages file and if we see the lines below, then all our works is success:
Oct 28 14:39:18 snort barnyard2[92208]: Barnyard2 initialization completed successfully (pid=92208
Oct 28 14:39:18 snort barnyard2[92208]: Using waldo file ‘/var/log/snort/barnyard2.waldo’: spool directory = /var/log/snort spool filebase = snort.log time_stamp = 1414451087 record_idx = 25412
Oct 28 14:39:18 snort barnyard2[92208]: Opened spool file ‘/var/log/snort/snort.log.1414451087’
Oct 28 14:39:20 snort barnyard2[92208]: Waiting for new data
You must wait minimum 10 minute, because barnyard must write all events to mysql database.
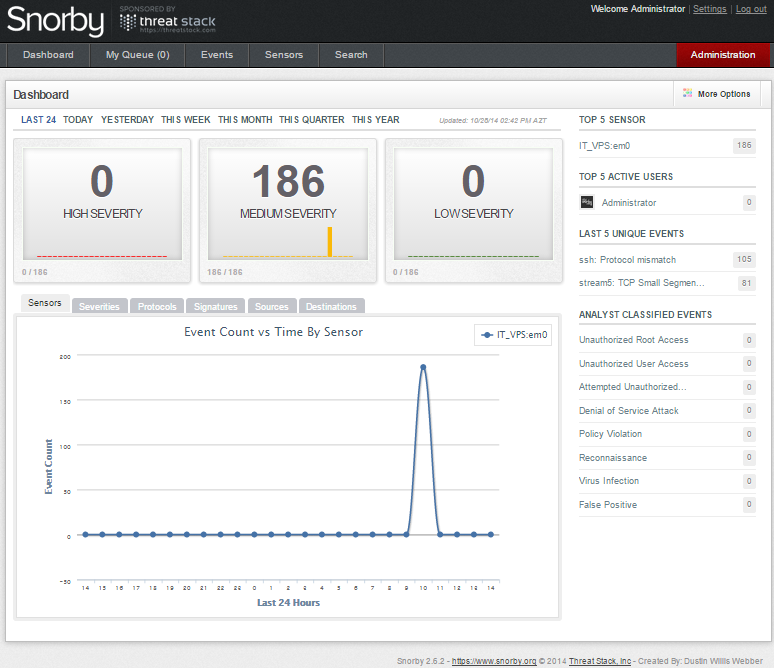
After success the statistics will be shown as below:
If you will see the error Snorby worker is not currently working you can fix this as below:
What it is for:
- When snorby starts one process in background which starts snorby in production mode. You can see about this at the end of first page of https://snorby.org/ official page and the lines that I showed below.
<strong>ruby script/delayed_job start RAILS_ENV=production</strong>
You can use the following command to start from CLI:
To automate our work we will use expect language and for using it we must install it:
# Go to the port
# install
Add the following lines to this /root/run_snorby_WP file:
<strong>set timeout 1000</strong>
<strong>spawn /bin/ps aux</strong>
<strong>expect "delayed_job" {</strong>
<strong> exit</strong>
<strong>}</strong>
<strong>cd /usr/local/www/snorby</strong>
<strong>spawn /usr/local/bin/ruby script/delayed_job start</strong>
<strong>expect "ERROR: there is already one or more instance(s) of the program running" {</strong>
<strong> cd /usr/local/www/snorby</strong>
<strong> system /usr/local/bin/ruby script/delayed_job restart</strong>
<strong>}</strong>
<strong>exit</strong>
# Doing executable for root user
# With this command you can run from CLI to test it
For kill you can use command below:
Add cron schedule to check work each 15 minutes and automatic work after reboot:
<strong>@reboot root /usr/local/bin/expect -f /root/run_snorby_WP >/dev/null 2>&1</strong>
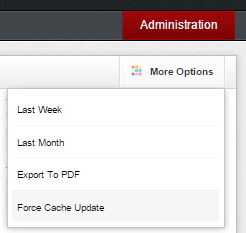
But Snorby can work unstable and can’t update itself. Then we will do it manually from the link as it is shown following screenshot More Options -> Force Cache Update.
Note: Because of the fault below your database can be widen illogically and we don’t need this.
The only way to solve it is to TRUNCATE all coloums with big numerals.
stream5: TCP session without 3-way handshake
At last it is time Snortsam
We can say that Snortsam has no documentation and it is in dead position.The only solution way is its communication with barnyard.You can read about it from the README.snortsam documentation.
# Go to the port folder
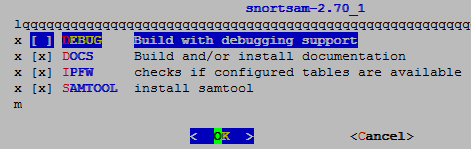
# Don’t forget to select IPFW module and don’t check debug cause it will not compile
# install
After installation copy all all sample files to the original:
<strong>cp /usr/local/etc/snortsam/rootservers.cfg.sample /usr/local/etc/snortsam/rootservers.cfg</strong>
<strong>cp /usr/local/etc/snortsam/snortsam.conf.sample /usr/local/etc/snortsam/snortsam.conf</strong>
The configuration /usr/local/etc/snortsam/snortsam.conf file will be consist of the following lines:
# 123 is the key which we use to talk with barnyard
# Listen on the port 777
# Allow to access from the 127.0.0.1 IP address with the 123 password
# Set the log file
# Log level debug for detail information
# Used firewall IPFW
# Listen on em0 and write rules to table 1 and 2
# Start in daemon mode for working automatically
#include /usr/local/etc/snortsam/country-rootservers.conf
# Create log file to see logs
We create /etc/ipfw.conf configuration file for our firewall and write the following lines in it:
<strong>ipfw add 00011 deny ip from "table(2)" to any via em0</strong>
ipfw add 00200 deny ip from any to 127.0.0.0/8
ipfw add 00300 deny ip from 127.0.0.0/8 to any
ipfw add 65000 allow ip from any to any
Add the following lines to /etc/rc.conf file for working after reboot:
<strong>firewall_type="UNKNOWN"</strong>
<strong>firewall_script="/etc/ipfw.conf"</strong>
<strong>gateway_enable="YES"</strong>
In the configuration /boot/loader.conf file will be the following lines or you must add IPDIVERT and IPFW options to your kernel and recompile to work IPFW firewall:
<strong>ipfw_load="YES"</strong>
<strong>hw.usb.no_pf=1</strong>
At the end we delete the comment that was in the last line of /usr/local/etc/barnyard2.conf configuration file and then restart it in order to connect to snortsam:
Add the following lines to /etc/rc.conf configuration file for working snortsam after rebooting:
<strong>snortsam_conf="/usr/local/etc/snortsam/snortsam.conf"</strong>
# We start Daemon and successful result must be as follows.
SnortSam, v 2.70.
Copyright (c) 2001-2009 Frank Knobbe <frank@knobbe.us>. All rights reserved.
Plugin ‘fwsam’: v 2.5, by Frank Knobbe
Plugin ‘fwexec’: v 2.7, by Frank Knobbe
Plugin ‘pix’: v 2.9, by Frank Knobbe
Plugin ‘ciscoacl’: v 2.12, by Ali Basel <alib@sabanciuniv.edu>
Plugin ‘cisconullroute’: v 2.5, by Frank Knobbe
Plugin ‘cisconullroute2’: v 2.2, by Wouter de Jong <maddog2k@maddog2k.net>
Plugin ‘netscreen’: v 2.10, by Frank Knobbe
Plugin ‘ipf’: v 2.16, by Erik Sneep <erik@webflex.nl>
Plugin ‘pf2’: v 3.3, by Olaf Schreck <chakl@syscall.de>
Plugin ‘ipfw2’: v 2.4, by Robert Rolfe <rob@wehostwebpages.com>
Plugin ‘watchguard’: v 2.7, by Thomas Maier <thomas.maier@arcos.de>
Plugin ’email’: v 2.12, by Frank Knobbe
Plugin ’email-blocks-only’: v 2.12, by Frank Knobbe
Plugin ‘snmpinterfacedown’: v 2.3, by Ali BASEL <ali@basel.name.tr>
Plugin ‘forward’: v 2.8, by Frank Knobbe
Parsing config file /usr/local/etc/snortsam/snortsam.conf…
Linking plugin ‘fwexec’…
Linking plugin ‘ipfw2’…
Checking for existing state file “/var/db/snortsam.state”.
Found. Reading state file.
Starting to listen for Snort alerts.
# We must see the following result in the log file
2014/10/28, 22:27:34, -, 1, snortsam, Starting to listen for Snort alerts.
At the end we reboot server and can see the following lines in the /var/log/snortsam.log file where connection from localhost coming to snortsam:
<strong>2014/10/28, 22:42:25, 127.0.0.1, 3, snortsam, Adding sensor 127.0.0.1 to list.</strong>
If you do all steps exactly, after reboot everything will work. Because when I did everything worked. But, in any way if snortsam will not start, add the following lines to the /etc/crontab file and remove snortsam lines from /etc/rc.conf file. It will be enough.
For testing create rule and test our IPS
# Create folder for rule
Add the following lines to the /usr/local/etc/snort/rules/local.rules/test.rules file:
<strong>alert tcp any any -> 88.8.81.134 443 (msg:"TEST block remoteserver port 443"; sid:5555502; rev:1; priority:1;)</strong>
# Change owner and group to snort
– It is the version of the rule, if we don’t write it, the rule won’t work.
– It is the priority of the rule, it will be red.
– And just with it comes block commant to IPFW.
It means that we block access for 10 minutes from any of source IP address and ports to our server IP 88.8.81.134 and ports 80,443(If we write here dst it will be block for destination). If you noticed exactly, you saw every rule had it own SID.
We have to add these SIDs with similar syntax to the /usr/local/etc/sid-block.map file to block source which are match the rules. sid-block.map file is roughly defined in barnyard2 code that it must be in the same address with its configuration file. It means if barnyard2.conf configuration file is located in /usr/local/etc/ address, sid-block.map file has to be in the same address.
Then we create /usr/local/etc/sid-block.map named file in the folder that barnyard.conf is located and add the following lines:
# Here we write SID, traffic direction and block time.
# Here we write SID, traffic direction and block time
Explain the syntax from sid-block.map file:
sid – This is Snort ID which is communicating with Snort SAM rule
who – src(source), dst(destination)
IP address which will block with snort ID
how – In, out, src, dest, either, both, this, conn, connection
It is not required parameter which says to SnortSAM that block any coming packets, In and Out from this host.
time – Blocking time with seconds. (It is possible ‘days‘, ‘months‘, ‘weeks‘,
‘years‘, ‘minutes‘, ‘seconds‘, ‘hours‘. Alternative way with writing
0(always) or PERManent, INFinite, ALWAYS you can block it for ever
(Be careful with this!).
Examples:
<strong>1292: dst[in], 2 days 4 hours</strong>
<strong>1638: src, 1 hour</strong>
We add the following line to the configuration file /usr/local/etc/snort/snort.conf where include is located, to start the rules:
Then we restart Snort and BarnYard. Or we reboot server for test all startups.
<strong>/usr/local/etc/rc.d/barnyard2 restart</strong>
Then we test by attacking to server where snort is located with our following script(Add lines below to https-check.sh file):
# cat https-check.sh
if ! [ -x “$(type -P ab)” ]; then
echo “ERROR: script requires apache bench”
echo “For FreeBSD and friends get it with ‘pkg_add -r apache22′”
echo “If you have it, perhaps you don’t have permissions to run it, try ‘sudo $(basename $0)'”
exit 1
fi
if [ “$#” -ne “4” ]; then
echo “ERROR: script needs four arguments, where:”
echo
echo “1. Number of times to repeat test (e.g. 10)”
echo “2. Total number of requests per run (e.g. 100)”
echo “3. How many requests to make at once (e.g. 50)”
echo “4. URL of the site to test (e.g. http://yoursite.org/)”
echo
echo “Example:”
echo ” $(basename $0) 10 100 50 http://yoursite.org/”
echo
echo “The above will send 100 GET requests (50 at a time) to http://yoursite.org. The test will be repeated 10 times.”
exit 1
else
runs=$1
number=$2
concurrency=$3
site=$4
fi
log=ab.$(echo $site | sed -r ‘s|https?://||;s|/$||;s|/|_|g;’).log
if [ -f $log ]; then
echo removing $log
rm $log
fi
echo “==================================================================”
echo ” Results”
echo “==================================================================”
echo ” site ………. $site”
echo ” requests …… $number”
echo ” concurrency … $concurrency”
echo “——————————————————————”
for run in $(seq 1 $runs); do
ab -c$concurrency -n$number $site >> $log
echo -e ” run $run: \t $(grep “^Requests per second” $log | tail -1 | awk ‘{print$4}’) reqs/sec”
done
avg=$(awk -v runs=$runs ‘/^Requests per second/ {sum+=$4; avg=sum/runs} END {print avg}’ $log)
echo “——————————————————————”
echo ” average ……. $avg requests/sec”
echo
echo “see $log for details”
Execute this script and use for attack:
<strong># ./https.sh 3 4000 500 http://snort.server.ip/</strong>
apr_socket_recv: Connection reset by peer (54)
run 1: reqs/sec
apr_socket_recv: Connection reset by peer (54)
run 2: reqs/sec
apr_socket_connect(): Permission denied (13)
We will see in Snort log file that Snort send the requests to Barnyard and Barnyard insert these requests to MySQL database. After complete this insert it will connect to SnortSAM and send alert. SnortSAM get this alert, and send request to IPFW2 for adding IP address of coming source to 1st and 2nd table:
1 Query INSERT INTO opt (sid,cid,optid,opt_proto,opt_code,opt_len,opt_data) VALUES (1,1185659,0,6,2,2,’05B4′)
1 Query INSERT INTO iphdr (sid, cid, ip_src, ip_dst, ip_ver, ip_hlen, ip_tos, ip_len, ip_id, ip_flags, ip_off,ip_ttl, ip_proto, ip_csum) VALUES (1,1185659,423182146,1578389894,4,5,0,48,766,0,0,124,6,62388)
1 Query COMMIT
1 Query BEGIN
1 Query INSERT INTO event (sid,cid,signature,timestamp) VALUES (1, 1185660, 509, ‘2014-10-29 14:04:07′)
1 Query INSERT INTO tcphdr (sid, cid, tcp_sport, tcp_dport, tcp_seq, tcp_ack, tcp_off, tcp_res, tcp_flags, tcp_win, tcp_csum, tcp_urp) VALUES (1,1185660,3072,80,4200216406,2152351244,7,0,2,8192,41671,0)
1 Query INSERT INTO opt (sid,cid,optid,opt_proto,opt_code,opt_len,opt_data) VALUES (1,1185660,0,6,2,2,’05B4’)
1 Query INSERT INTO iphdr (sid, cid, ip_src, ip_dst, ip_ver, ip_hlen, ip_tos, ip_len, ip_id, ip_flags, ip_off,ip_ttl, ip_proto, ip_csum) VALUES (1,1185660,241434114,1578389894,4,5,0,48,766,0,0,124,6,16330)
1 Query COMMIT
1 Query BEGIN
We see in SnortSAM log that it added information about blocking to IP address sourced 99.45.57.58 to IPFW tables:
2014/10/29, 02:23:21, 127.0.0.1, 2, snortsam, Blocking host 99.45.57.58 completely for 600 seconds (Sig_ID: 5555501).
2014/10/29, 02:23:21, -, 3, ipfw2, Info: Command “/sbin/ipfw table 1 add 99.45.57.58/32;/sbin/ipfw table 2 add 99.45.57.58/32” Executed Successfully
We look at the rules in 1st and 2nd tables of IPFW:
99.45.57.58/32 0.0.0.0
<strong>ipfw -i table 2 list | grep</strong> <strong>99.45.57.58/32</strong>
99.45.57.58/32 0.0.0.0
# Also we can see in the log file of barnyard that it send alert to SnortSAM.
10/29-02:23:20.735311 [**] [1:5555501:1] <em0> Snort Alert [1:5555501:1] [**] [Classification ID: 0] [Priority ID: 1] {TCP} 99.45.57.58:1024 -> 88.8.81.134:80
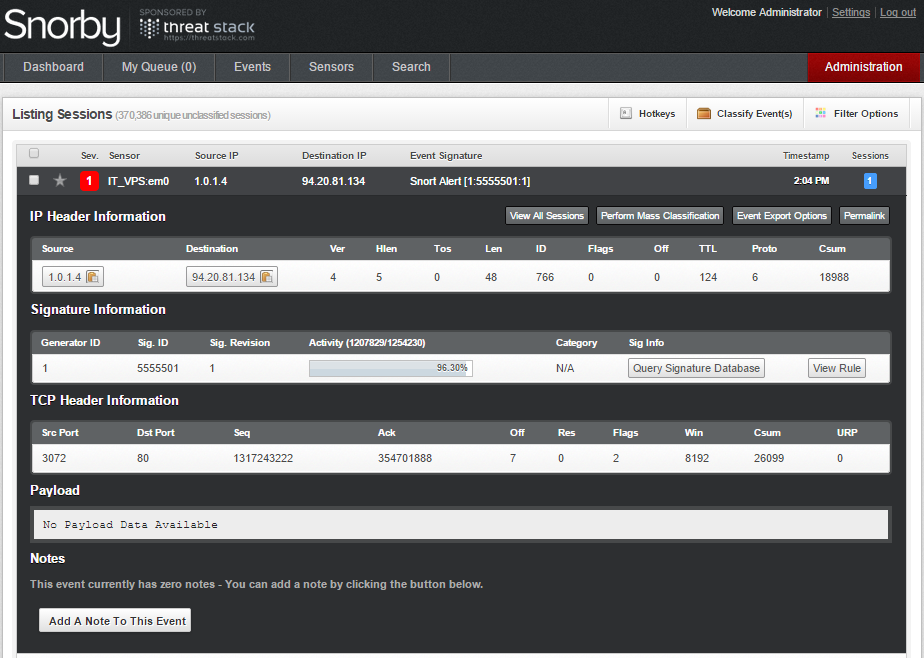
For example we can see in our Snort server the attack of different host to the server which IPS is located:
But the /usr/local/etc/sid-block.map file’s filling automatically, working dynamically is not a day’s work. But we can do it something.For doing this it was used a lot of regex syntax and let’s explain them before:
We match the Regex lines:
^[^\#] – # Started with the symbol
.*sid: – Any symbol on the left and any word with sid word on the right:
(.[0-9]*[0-9]\) – () the inner is which we want to catch, but [0-9]*[0-9] any ordered amount of numbers.
.* – At the end wildcard for the sed
s// – The operator which writes it \1″:” “src,” “30min”/p”
\1 – that we catched before
“:” “src,” “30min” – It is the text that we connect to, if here will be double brackets ” ” it means space
\p – Go to the new line
Then we write pathes of files with spaces. Remember that it is not needed to write all rules for src-a gore yazilmali deyil. In my case this is just an example.
Result:
# Restart the Barnyard daemon.
Automatize all things!
Update rules from Snort site and after block!
OinkMaster is busy and that is why we will do it next!
First we must create rules for src and dst block!
/tmp/test/blocksrc.rules – The file for src block
/tmp/test/blockdst.rules – The file for dst blocks
We need 2 sed command:
Delete old file and add content for src from blocksrc.rules file.
Delete old file and add content for dst from blockdst.rules file.
The blocking of first file wasn’t done succesfully with sed , and that is why we join two files with the 3rd command.
At the end we add the following line to /etc/crontab file after OinkMaster finishing its work, for Barnyard collecting blocked files and restarting it.
It is needed resources for this system, because,there can be emergency, Snort can create big traffic. It is true that snort will write them quickly to its files. But Barnyard2 and MySQL can take them for an hour!
For example snort generated 310MB traffic for 2 minutes. In my virtual machine was 1 CPU, 4 core and 4GB RAM, but I waited insert from barnyard2 to MySQL more than an hour.
Used sources: http://www.itcooky.com/