OpenVPN Access Server(AS) is a full featured SSL VPN software solution that integrates OpenVPN server capabilities, enterprise management capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software packages that accommodate Windows OS, MAC OS, and Linux environments.
OpenVPN Access Server supports a wide range of configurations, including secure remote access to internal network and/or private cloud network resources and applications with fine-grained access control. It has a mobile app for Android and iOS, so that you can access the VPN server from your smartphones too.
Install OpenVPN AS on Ubuntu/Debian
OpenVPN AS is quite easy to install and configure compared to other VPN servers.
Download the latest version of OpenVPN AS with the following commands.
For Ubuntu 32bit:
$ wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-Ubuntu12.i386.deb
For Ubuntu 64bit:
$ wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-Ubuntu12.amd_64.deb
For Debian 32bit systems:
$ wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-Debian6.i386.deb
For Debian 64bit systems:
$ wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-Debian6.amd_64.deb
Install it with the following command:
sk@server1:~$ sudo dpkg -i openvpn-as-1.8.5-Ubuntu12.i386.deb
[sudo] password for sk:
Selecting previously unselected package openvpn-as.
(Reading database ... 53813 files and directories currently installed.)
Unpacking openvpn-as (from openvpn-as-1.8.5-Ubuntu12.i386.deb) ...
Setting up openvpn-as (1.8.5-Ubuntu12) ...
The Access Server has been successfully installed in /usr/local/openvpn_as
Configuration log file has been written to /usr/local/openvpn_as/init.log
Please enter "passwd openvpn" to set the initial
administrative password, then login as "openvpn" to continue
configuration here: https://192.168.1.201:943/admin
To reconfigure manually, use the /usr/local/openvpn_as/bin/ovpn-init tool.
Access Server web UIs are available here:
Admin UI: https://192.168.1.201:943/admin
Client UI: https://192.168.1.201:943/
Now OpenVPN AS has been installed.
Setup OpenVPN Admin User and Password
During installation, a default Admin user called openvpn will be created by OpenVPN AS. Set the password for the user openvpn with the following command:
sk@server1:~$ sudo passwd openvpn
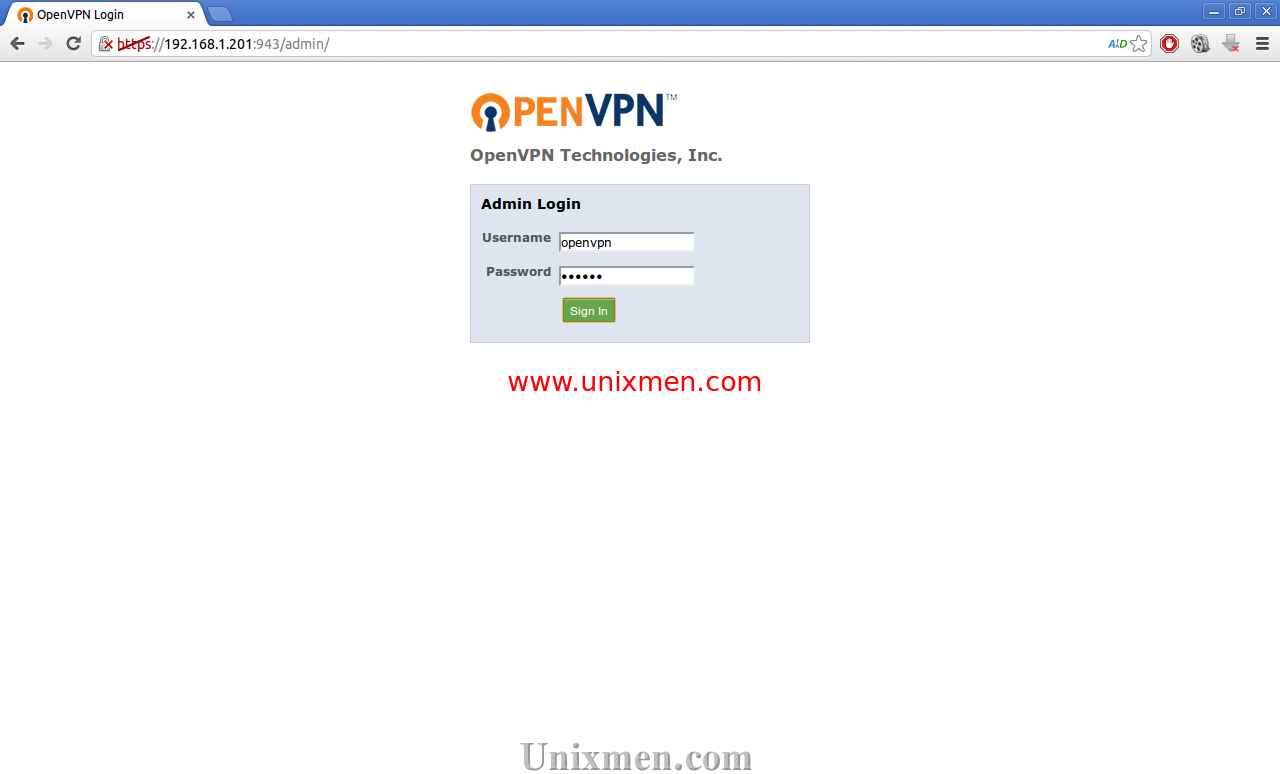
Accessing Admin Web UI
You can access the OpenVPN Access Server Admin UI with the URL https://ip-address:943/admin/ from your browser. If you want to access it from your remote systems, allow the port 943 through your router/firewall.
A SSL warning message will appear, ignore the warning by click On the Proceed anyway button. You will be prompted to enter username and password. Enter openvpn as your username with password that you have created earlier.
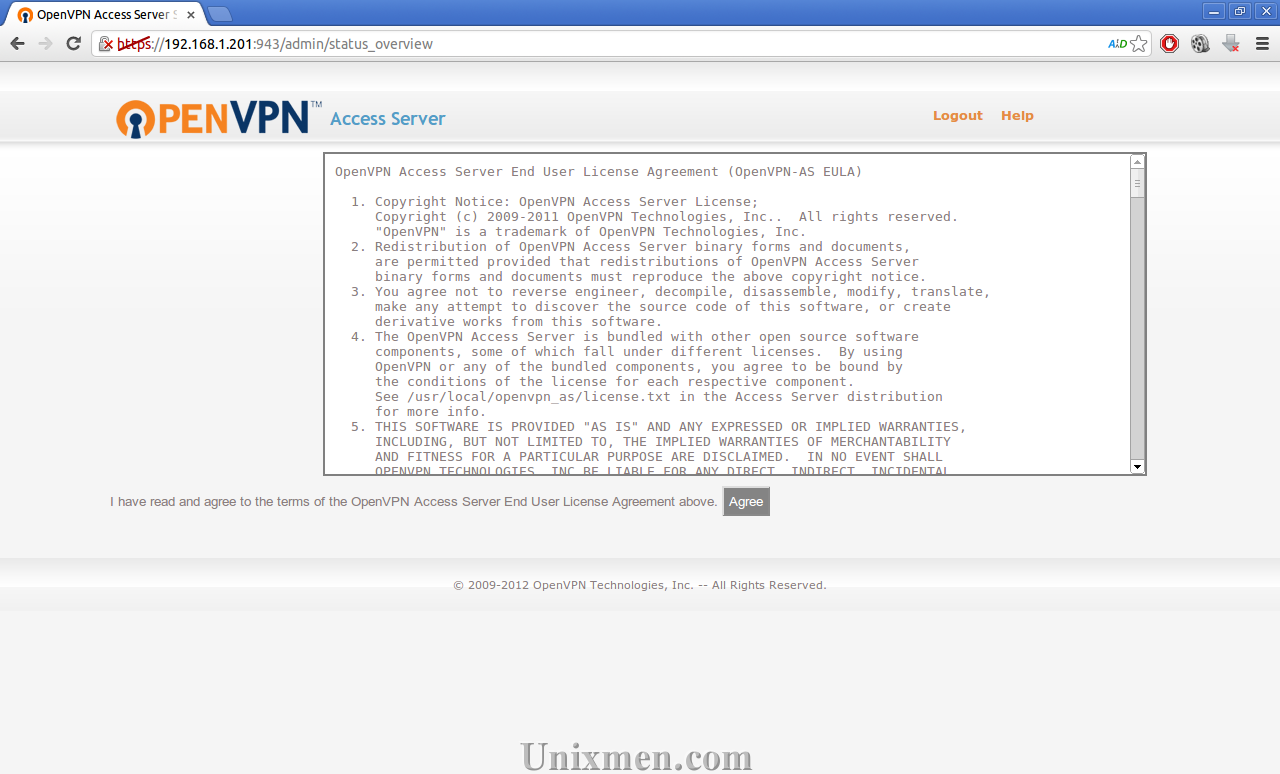
Click on Agree to accept the License Agreement.
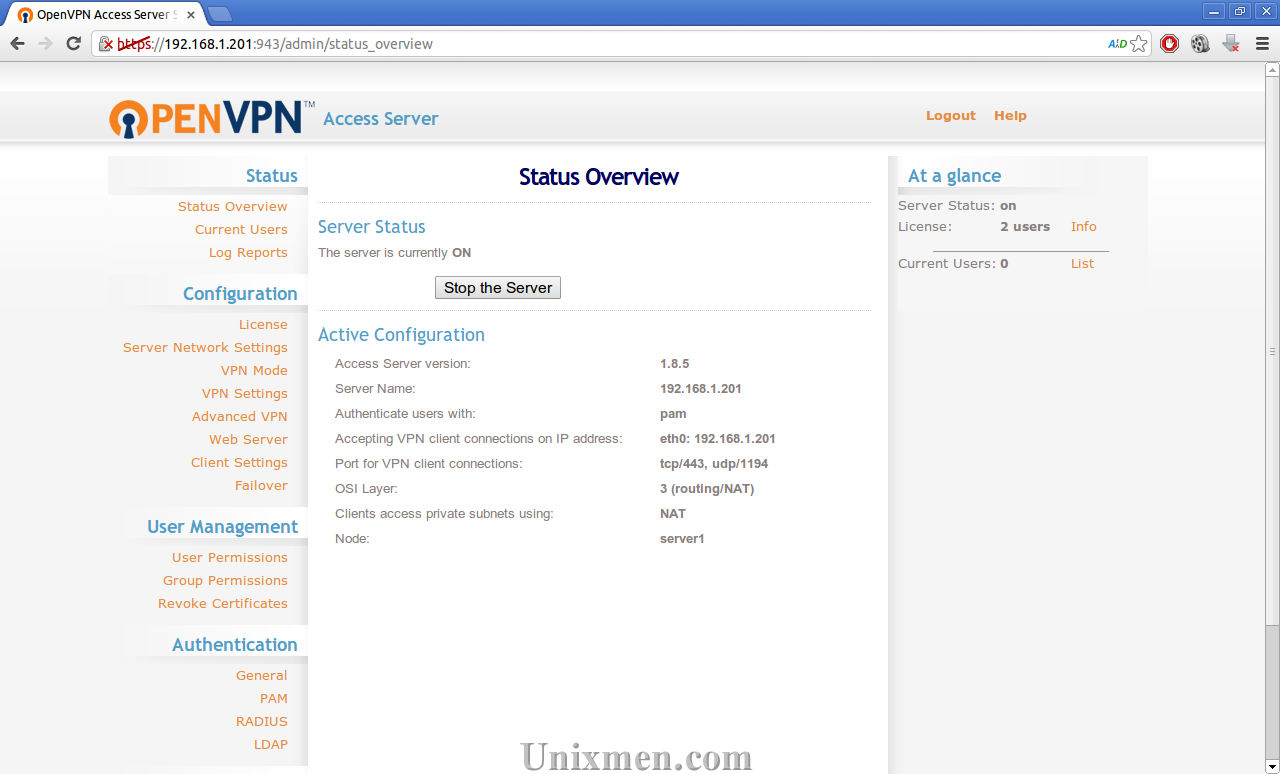
Now you will able to access the OpenVPN Administration Console. In this Admin Console, you can do various VPN administration things. Go through every menu/tab and change the required values as per your liking, although default settings will work fine.
Access OpenVPN cerver from client systems
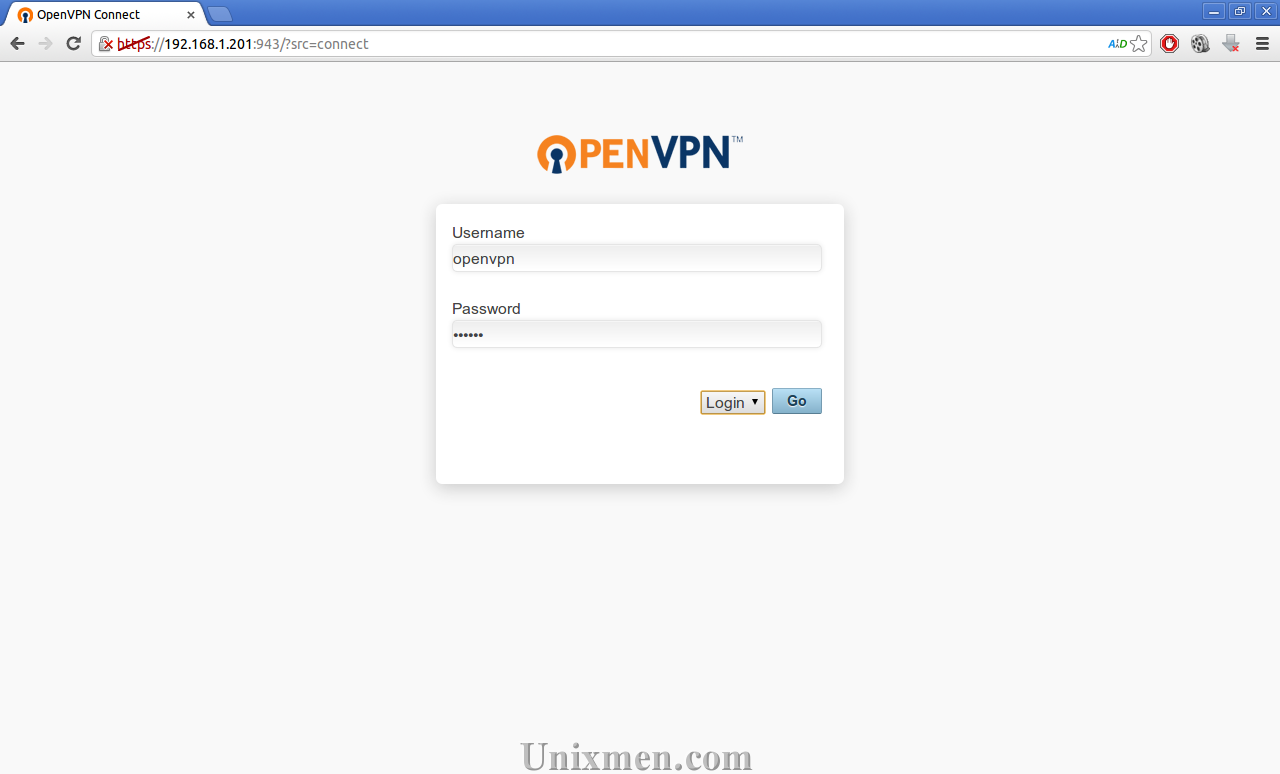
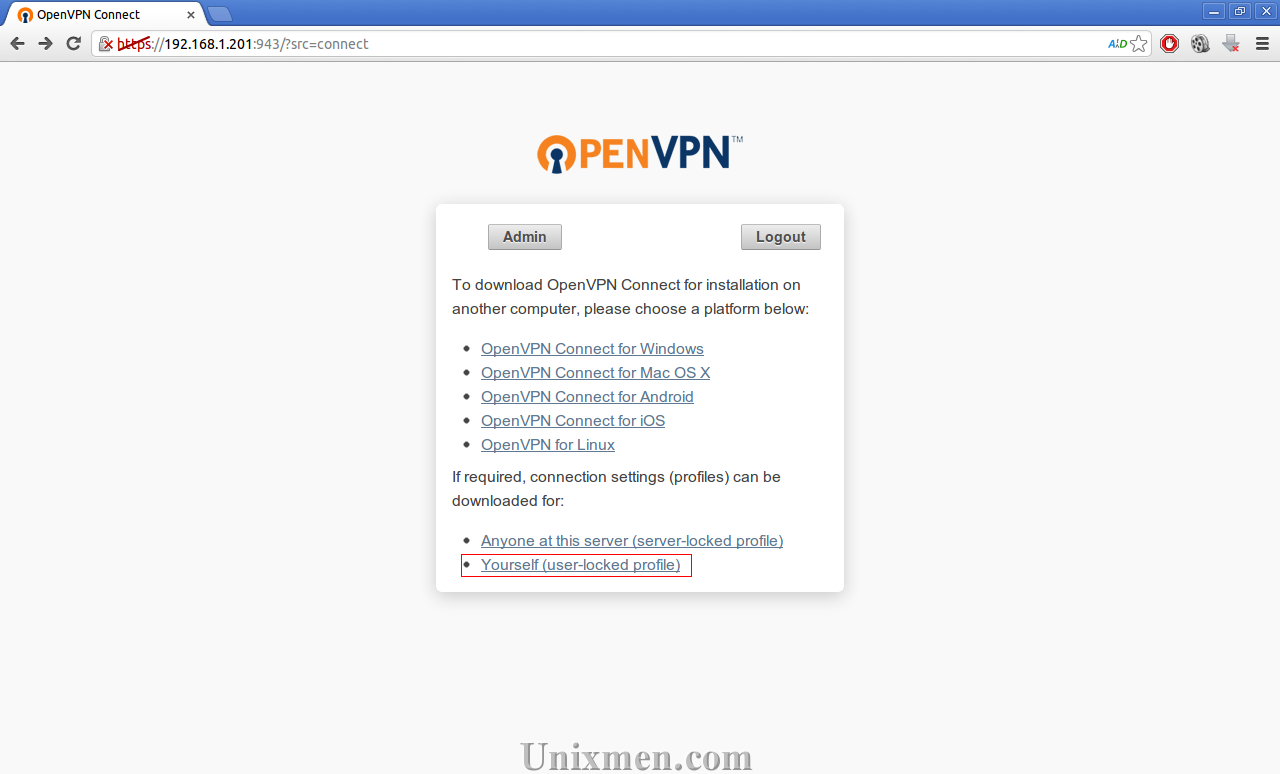
Here I use Ubuntu 13.04 Desktop as my client. Navigate to https://ip-address:943/ from your browser and login with OpenVPN administrative credentials. In my case it’s openvpn and ubuntu.
Download the client config file. Click on Yourself (user-locked profile) tab to download the user client config file.
I have downloaded this file to /home/Downloads directory.
Install openvpn package in your client system:
sk@sk:~$ sudo apt-get install openvpn
Now connect to VPN server with following command:
sk@sk:~$ sudo openvpn --config Downloads/client.ovpn Thu Jun 27 11:36:43 2013 OpenVPN 2.2.1 x86_64-linux-gnu [SSL] [LZO2] [EPOLL] [PKCS11] [eurephia] [MH] [PF_INET6] [IPv6 payload 20110424-2 (2.2RC2)] built on Feb 13 2013 Enter Auth Username:openvpn Enter Auth Password: Thu Jun 27 11:36:50 2013 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables Thu Jun 27 11:36:50 2013 Control Channel Authentication: tls-auth using INLINE static key file Thu Jun 27 11:36:50 2013 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Thu Jun 27 11:36:50 2013 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Thu Jun 27 11:36:50 2013 LZO compression initialized Thu Jun 27 11:36:50 2013 Control Channel MTU parms [ L:1542 D:166 EF:66 EB:0 ET:0 EL:0 ] Thu Jun 27 11:36:50 2013 Socket Buffers: R=[212992->200000] S=[212992->200000] Thu Jun 27 11:36:50 2013 Data Channel MTU parms [ L:1542 D:1450 EF:42 EB:135 ET:0 EL:0 AF:3/1 ] Thu Jun 27 11:36:50 2013 Local Options hash (VER=V4): '504e774e' Thu Jun 27 11:36:50 2013 Expected Remote Options hash (VER=V4): '14168603' Thu Jun 27 11:36:50 2013 UDPv4 link local: [undef] Thu Jun 27 11:36:50 2013 UDPv4 link remote: [AF_INET]192.168.1.201:1194 Thu Jun 27 11:36:50 2013 TLS: Initial packet from [AF_INET]192.168.1.201:1194, sid=9b431007 26bc1d62 Thu Jun 27 11:36:50 2013 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Thu Jun 27 11:36:50 2013 VERIFY OK: depth=1, /CN=OpenVPN_CA Thu Jun 27 11:36:50 2013 VERIFY OK: nsCertType=SERVER Thu Jun 27 11:36:50 2013 VERIFY OK: depth=0, /CN=OpenVPN_Server Thu Jun 27 11:36:50 2013 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key Thu Jun 27 11:36:50 2013 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Thu Jun 27 11:36:50 2013 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key Thu Jun 27 11:36:50 2013 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Thu Jun 27 11:36:50 2013 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA Thu Jun 27 11:36:50 2013 [OpenVPN_Server] Peer Connection Initiated with [AF_INET]192.168.1.201:1194 Thu Jun 27 11:36:53 2013 SENT CONTROL [OpenVPN_Server]: 'PUSH_REQUEST' (status=1) Thu Jun 27 11:36:53 2013 PUSH: Received control message: 'PUSH_REPLY,explicit-exit-notify,topology subnet,route-delay 5 30,dhcp-pre-release,dhcp-renew,dhcp-release,route-metric 101,ping 12,ping-restart 50,redirect-gateway def1,redirect-gateway bypass-dhcp,redirect-gateway autolocal,route-gateway 5.5.8.1,dhcp-option DNS 8.8.8.8,register-dns,auth-token SESS_ID_LsWOIk847WhraSg97ZADEg==,comp-lzo no,ifconfig 5.5.8.3 255.255.248.0' Thu Jun 27 11:36:53 2013 Unrecognized option or missing parameter(s) in [PUSH-OPTIONS]:4: dhcp-pre-release (2.2.1) Thu Jun 27 11:36:53 2013 Unrecognized option or missing parameter(s) in [PUSH-OPTIONS]:5: dhcp-renew (2.2.1) Thu Jun 27 11:36:53 2013 Unrecognized option or missing parameter(s) in [PUSH-OPTIONS]:6: dhcp-release (2.2.1) Thu Jun 27 11:36:53 2013 Unrecognized option or missing parameter(s) in [PUSH-OPTIONS]:15: register-dns (2.2.1) Thu Jun 27 11:36:53 2013 Unrecognized option or missing parameter(s) in [PUSH-OPTIONS]:16: auth-token (2.2.1) Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: timers and/or timeouts modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: explicit notify parm(s) modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: LZO parms modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: --ifconfig/up options modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: route options modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: route-related options modified Thu Jun 27 11:36:53 2013 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified Thu Jun 27 11:36:53 2013 ROUTE default_gateway=192.168.1.1 Thu Jun 27 11:36:53 2013 TUN/TAP device tun0 opened Thu Jun 27 11:36:53 2013 TUN/TAP TX queue length set to 100 Thu Jun 27 11:36:53 2013 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Thu Jun 27 11:36:53 2013 /sbin/ifconfig tun0 5.5.8.3 netmask 255.255.248.0 mtu 1500 broadcast 5.5.15.255 Thu Jun 27 11:36:58 2013 /sbin/route add -net 192.168.1.201 netmask 255.255.255.255 gw 192.168.1.1 Thu Jun 27 11:36:58 2013 /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 5.5.8.1 Thu Jun 27 11:36:58 2013 /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 5.5.8.1 Thu Jun 27 11:36:58 2013 Initialization Sequence Completed
Verify VPN users
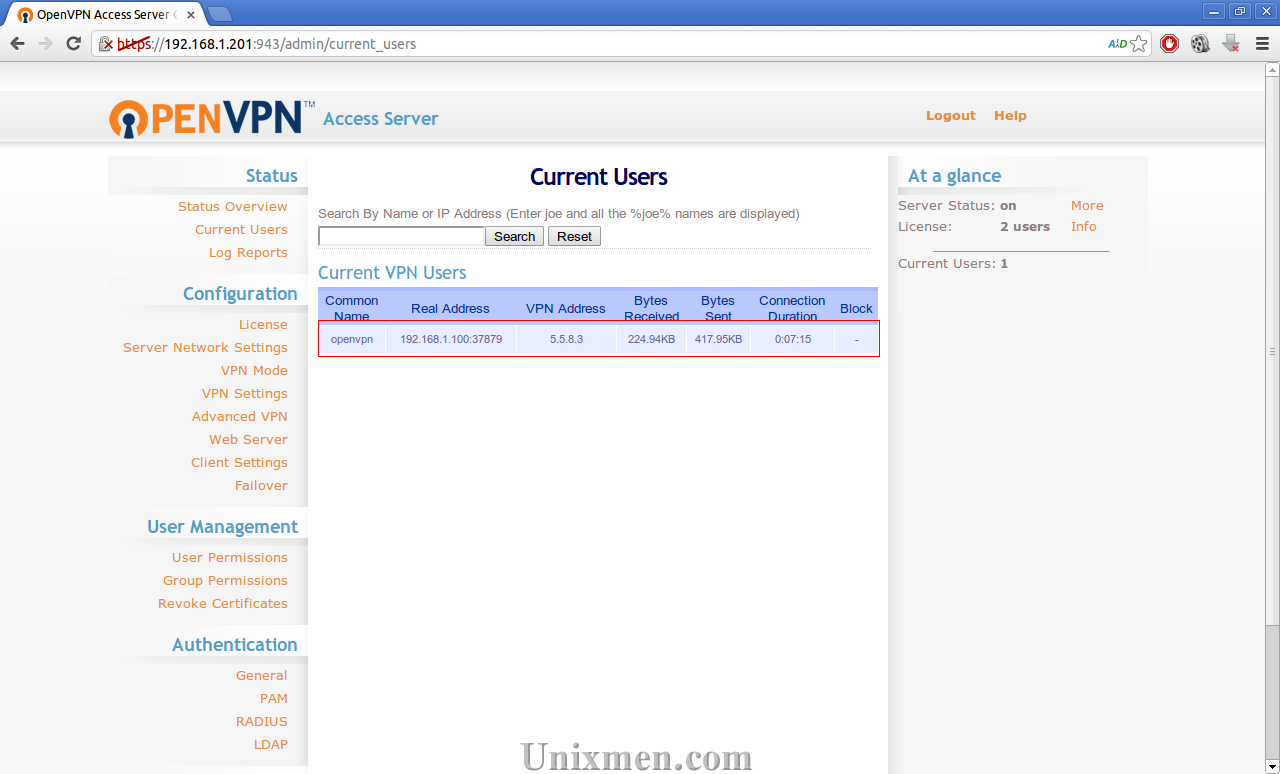
Login to your OpenVPN admin interface. Click on the Current users in the Status tab. You will see that there is a client user is connected to your VPN server.
As per the above screen shot the user ‘openvpn’ is accessing the VPN server.
Adding new users to OpenVPN server
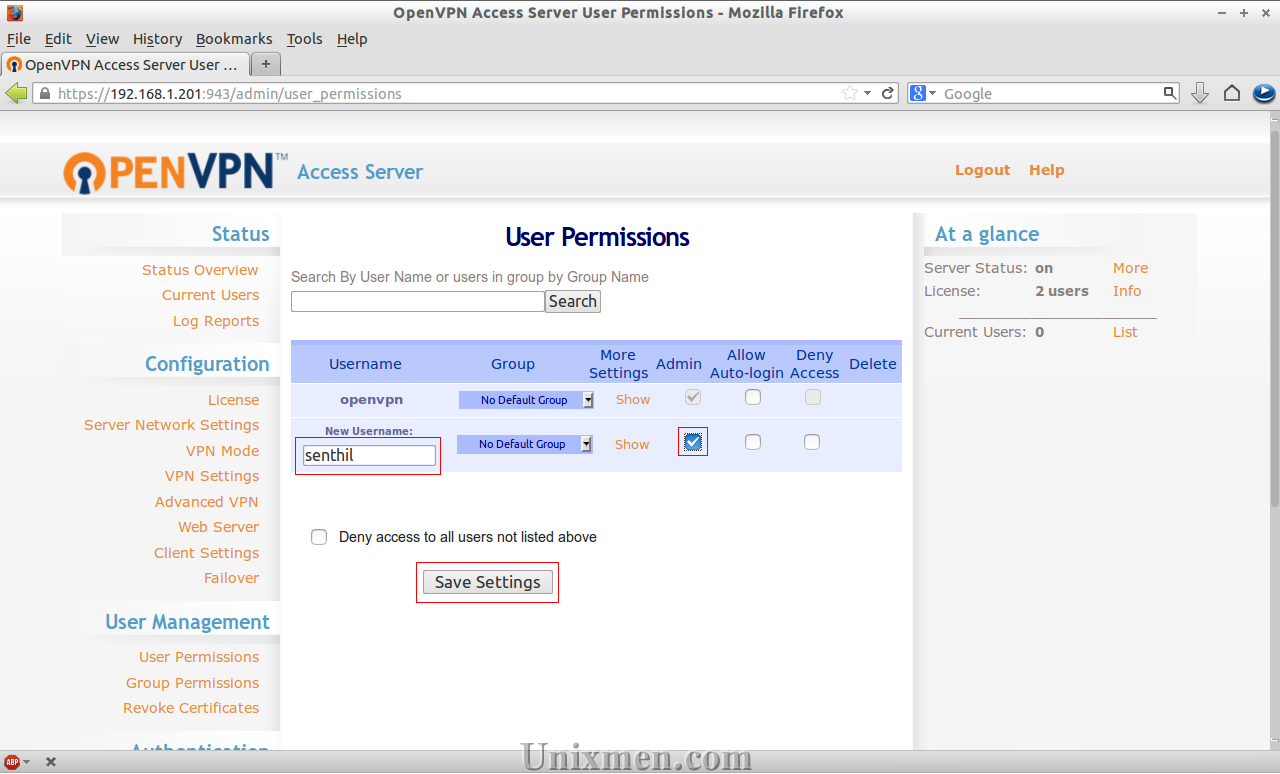
First create a new user (let us call it as senthil) in your server:
sk@server1:~$ sudo useradd senthil [sudo] password for sk:
Create a password for the user senthil:
sk@server1:~$ sudo passwd senthil Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
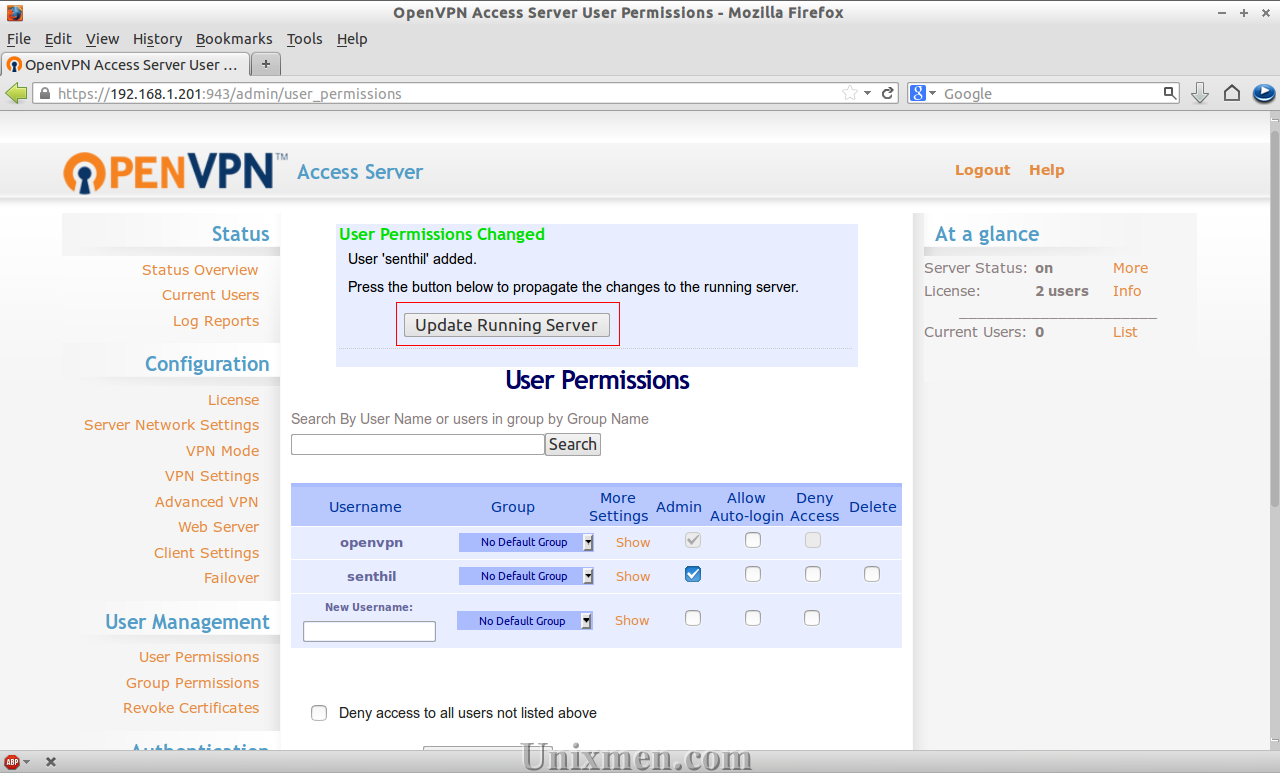
Now login to the OpenVPN admin console by navigating to https://ip-address:943/admin/ from your browser. Enter username as openvpn and password of openvpn. Go to User Management section. Add the newly created senthil and click Save Settings.
Update the running OpenVPN server.
Download client config file for the new user
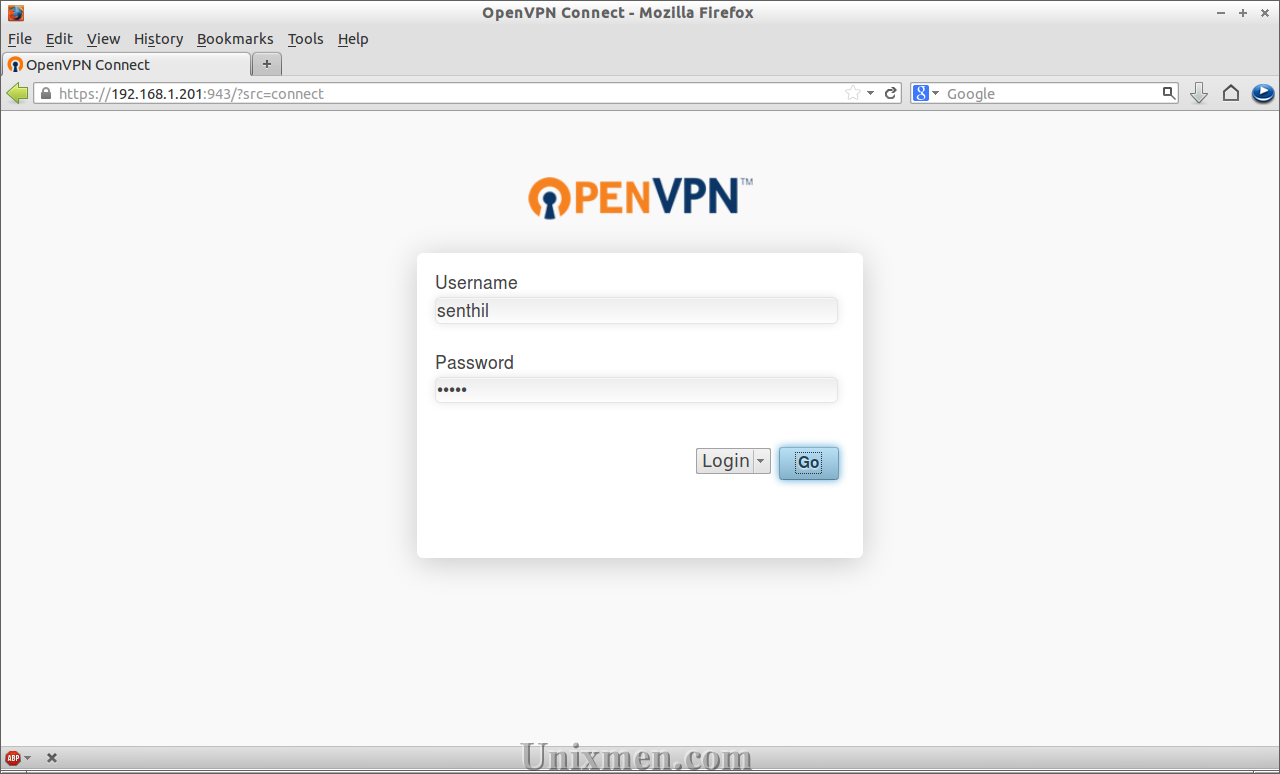
Navigate to https://ip-address:943/ from your browser. Enter username as senthil with password that you’ve created.
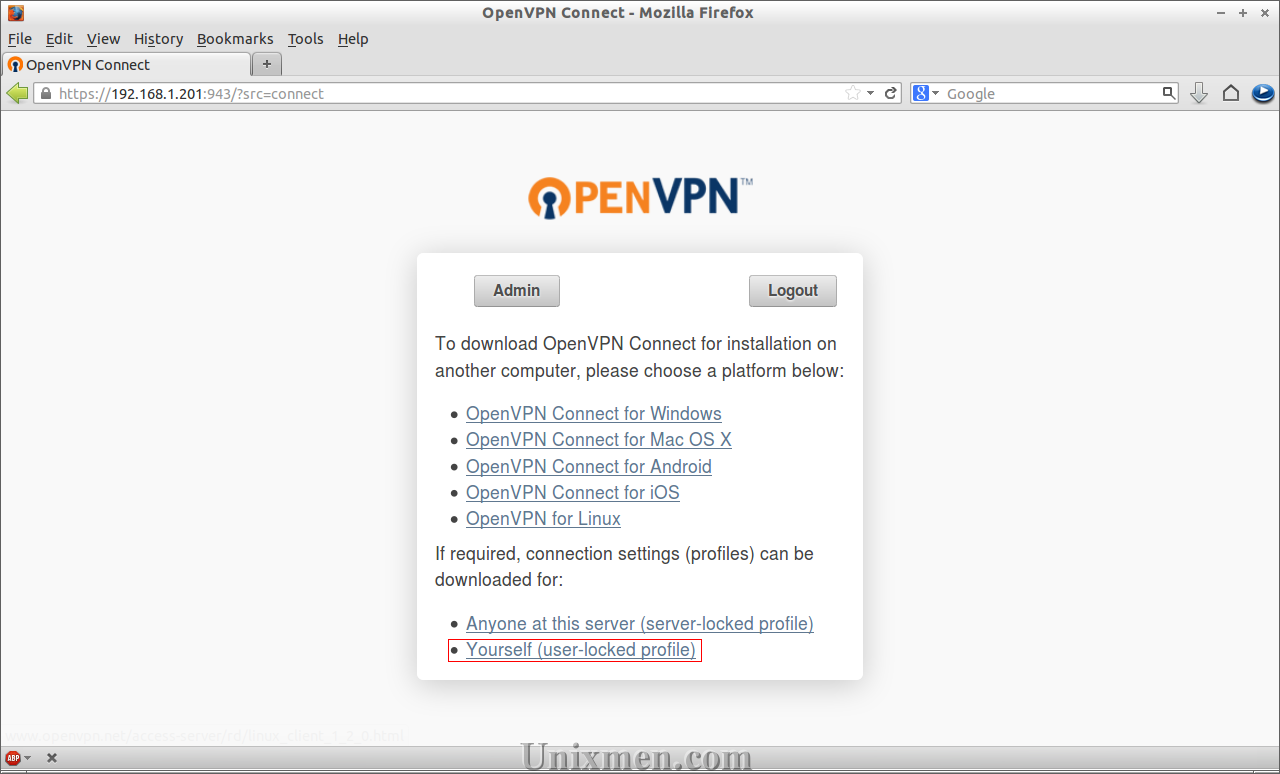
Download the config file by clicking on the tab Yourself (user-locked profile).
Try to connect with the new user ‘senthil’. Now you will be able to connect to OpenVPN server.
sk@sk:~$ sudo openvpn --config Downloads/client.ovpn Thu Jun 27 12:33:07 2013 OpenVPN 2.2.1 x86_64-linux-gnu [SSL] [LZO2] [EPOLL] [PKCS11] [eurephia] [MH] [PF_INET6] [IPv6 payload 20110424-2 (2.2RC2)] built on Feb 13 2013 Enter Auth Username:senthil Enter Auth Password: Thu Jun 27 12:33:13 2013 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables [...] Thu Jun 27 12:33:15 2013 ROUTE default_gateway=192.168.1.1 Thu Jun 27 12:33:15 2013 TUN/TAP device tun0 opened Thu Jun 27 12:33:15 2013 TUN/TAP TX queue length set to 100 Thu Jun 27 12:33:15 2013 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Thu Jun 27 12:33:15 2013 /sbin/ifconfig tun0 5.5.8.7 netmask 255.255.248.0 mtu 1500 broadcast 5.5.15.255 Thu Jun 27 12:33:21 2013 /sbin/route add -net 192.168.1.201 netmask 255.255.255.255 gw 192.168.1.1 Thu Jun 27 12:33:21 2013 /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 5.5.8.1 Thu Jun 27 12:33:21 2013 /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 5.5.8.1 Thu Jun 27 12:33:21 2013 Initialization Sequence Completed
Verify VPN users
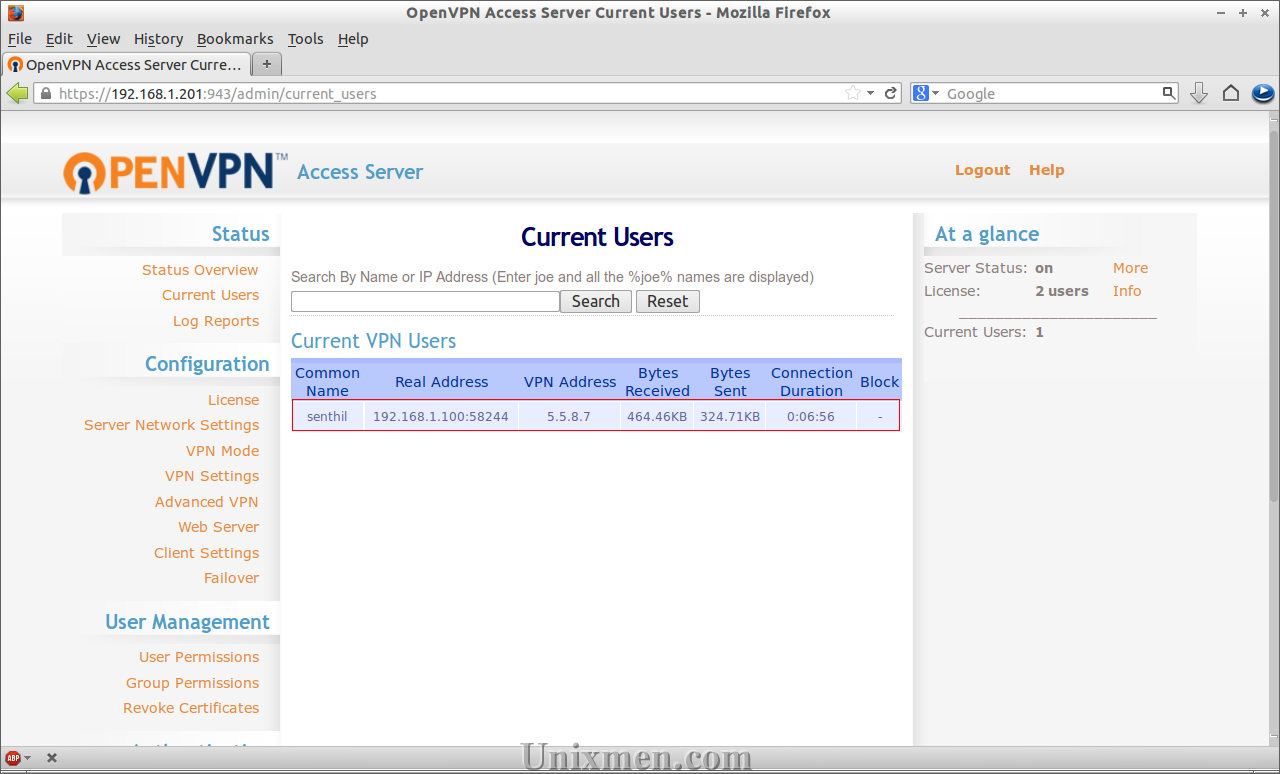
Check it in the Current Users section of OpenVPN admin console.
As per the above screenshot, the user senthil is accessing the VPN server.
For a detailed information about installation and configuration, I suggest you read the official page.
That’s it. Happy VPN’ing!