As I could see there are lot of articles about knockd and it’s implementation. So, what are my efforts to make this unique? I made it simple, but detail oriented and have commented on controversies and criticism that exist.
Here is an outline on what I’ve discussed.
What is port knocking?
What is knockd?
– How it works?
– Installation
– What we are trying to achieve
– Pre-requisite before implementation of knockd:
– Implementation scenario
– Testing
– Comments on controversies and criticism
Disclaimer
So, here we go.
What is port knocking?
Wikipedia Definition:
Port knocking is a method of externally opening ports on a firewall by generating a connection attempt on a set of prespecified closed ports (in this case, telnet). Once a correct sequence of connection attempts is received, the firewall rules are dynamically modified to allow the host which sent the connection attempts to connect over specific port(s)
/* in this article point of view, it’s ssh port 22 */
It’s basically like, every request would knock the door (firewall) to get through it. Knocking is necessary to get past the door. You shall either implement it using knockd and iptables or just iptables alone.
To know how to implement port knocking using iptables, refer our previous article “Port knocking: Enhance Security Using knockd and/or Iptables From Basics”
Now, using knockd.
What is knockd?
Knockd – Definition from zeroflux.org:
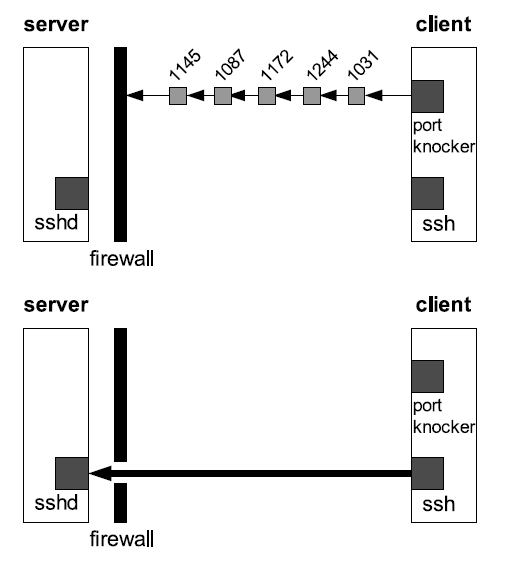
knockd is a port-knock server. It listens to all traffic on an Ethernet interface, looking for special “knock” sequences of port-hits. A client makes these port-hits by sending a TCP (or UDP) packet to a port on the server. This port need not be open — since knockd listens at the link-layer level, it sees all traffic even if it’s destined for a closed port. When the server detects a specific sequence of port-hits, it runs a command defined in its configuration file. This can be used to open up holes in a firewall for quick access.
How it works?
1. Knockd daemon installed/running in the server.
2. Configure some port sequences (tcp, udp, or both), and the appropriate actions for each sequence.
3. once knockd sees a defined port sequence, it will run the configured action for that sequence
Note:
It is completely stealth and it will not open any ports on the server, by default.
When a port knock is successfully used to open a port, the firewall rules are generally only opened to the ip_address that supplied the correct knock.
Note: Don’t copy/paste the commands. Type it manually to avoid errors that could occur due to the format.
# yum install libpcap*
/* dependency – * in the end installs libpcap-devel which is a pre-requisite, as well */
There are several ways to install, whereas I have followed rpm installation.
Download suitable rpm package from http://pkgs.repoforge.org/knock/
Then run,
# rpm –ivh knock-0.5-3.el6.rf.x86_64.rpm
/*Here, I have downloaded knock 0.5-3 for 64-bit centos and hence the rpm name*/
Now, what all got installed?
Knockd – knock server daemon
Knock – knock client, which aids in knocking.
Note that this (knock) is default client comes along with knockd, whereas there are other advanced clients like hping, sendip & packit.
What we are trying to achieve:
A way to stop the attacks altogether, yet allow ssh access from anywhere, when needed.
Pre-requisite before implementation of knockd:
As mentioned earlier, an existing firewall (iptables) is a pre-requisite.
Follow the below steps to configure firewall
# iptables -I INPUT -p tcp -m state --state RELATED,ESTABLISHED -j ACCEPT
-I —– Inserting the rule as first line in the firewall setup
-p —– protocol
-m —–match against the states RELATED, ESTABLISHED, in this case
-j —– jump to action, which is ACCPET here.
/* This rule says to allow currently on-going session through firewall. It is essential so that if you have currrently taken remote session on this computer using SSH, it will be preserved and not get terminated by further rules where you might want to block ssh or all services */
# iptables -I INPUT -p icmp -j ACCEPT
/* This is to make your machine ping-able from any machine, so that you can check the availability of your machine (whether it’s up or down) */
# iptables –A INPUT –j REJECT
/* Rejecting everything else – Appending it as last line, since, if inserted as first line all other rules will not be considered and every request would be rejected*/
Implementation scenario:
Now, try to ssh to the machine where you have implemented firewall. Let’s call the machine as server.
You could not ssh to the server since the firewall setup in server rejects everything except on-going session and ping requests.
Now, knockd implementation:
Now, in server, that you have installed knockd, run the following commands
# vi /etc/knockd.conf
/*As a result of rpm installation, this configuration file will exist */
Edit the file as below and save/exit.
[options] logfile = /var/log/knockd.log [opencloseSSH] sequence = 2222:udp,3333:tcp,4444:udp seq_timeout = 15 start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT cmd_timeout = 10 stop_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn
First line of the file defines where the error/warnings pertaining to knockd gets logged. In case, if you’re unable to successfully launch connection between client and server using knockd/knock, then this is where you need to check – Server log.
sequence = 2222:udp,3333:tcp,4444:udp /* the sequence of knocking */
seq_timeout = 15 /* once the above mentioned sequence is knocked, it’s valid only for next 15 seconds */
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp –dport 22 -j ACCEPT
/* once the right sequence is knocked, the above command gets executed, where %IP% is the ip_addr of host which knocks. Hence, this allows, ssh connection from knocker (client) to server. One thing to be noted is that, ssh connection need to be established within next 15 seconds of knock. Also, note that I have given iptables –I, since I want this rule to be inserted as first line, because, in case if I append, it won’t have any effect, since iptables reject everything rule comes before this in the list*/
cmd_timeout = 10 /* the stop_command will be execued in 10 seconds from start_command execution. */
stop_command = /sbin/iptables -D INPUT -s %IP% -p tcp –dport 22 -j ACCEPT
/* I am deleting the rule which I inserted to allow the SSH connection from knocker (client) to server. Now, doesn’t it ends my ssh connection? – It doesn’t.
How? The existing rule in my iptables, #iptables -I INPUT -p tcp -m state –state RELATED,ESTABLISHED -j ACCEPT helps me to retain the established connection. In case, if this rule is not specified, then ur ssh connection will be lost in 10 seconds (i.e) cmd_timeout */
tcpflags = syn /* In TCP 3 way handshake, Client sends a TCP SYNchronize packet to Server */
Note that there are other ways to configure your knockd server. For example, a port sequence to open ssh, and another port sequence to close your ssh (unlike the above mentioned one), but in this case, after terminating your ssh session, you need to manually hit the port sequence from client, in order to close the ssh port for it.
Now, that we have configured our server to allow ssh for client only when the client hits the right sequence, which is 2222:udp,3333:tcp,4444:udp here.
Now, you need to start knockd service. Copy the below script as /etc/rc.d/init.d/knockd in your machine.
Runlevel script.
#!/bin/sh
# description: Start and stop knockd
# Check if that config file exist
[ -f /etc/knockd.conf ] || exit 0
# Source function library
. /etc/rc.d/init.d/functions
# Source networking configuration
. /etc/sysconfig/network
# Check that networking is up
[ "$NETWORKING" = "no" ] && exit 0
start() {
echo "Starting knockd ..."
/usr/sbin/knockd &
}
stop() {
echo "Shutting down knockd ..."
kill `pidof /usr/sbin/knockd`
}
case "$1" in
start)
start
;;
stop)
stop
;;
restart)
stop
start
;;
*)
echo "Usage: $0 {start|stop|restart}"
;;
esac
exit 0
Now, run the following commands, so that you shall start/stop/restart knockd like other services
# chmod 755 /etc/rc.d/init.d/knocd /* making the script executable by root */ # chkconfig --add knockd /* adding knockd to chkconfig list */ # chkconfig --level 35 knockd on /* service will be started as part of runlevel 3 & 5 */ # service knockd start
whenever you modify your /etc/knockd.conf, you need to restart the service.
Testing:
From client, run the following commands.
Note that there are other ways to knock, whereas I am using knock client which comes along with the knockd package. So, you need to have it installed in client, as well.
Now,
# knock –v server_ip 2222:udp 3333:tcp 4444:udp ;ssh server_ip
-v for verbose
server_ip substituted by your server’s ip address.
We are knocking the sequence which we mentioned in server’s /etc/knockd.conf file
Now, you shall successfully establish ssh session to server. Also, the port gets closed for further sessions. So, every time when you want to establish ssh connection to server, you need to knock and then ssh.
Comments on controversies and criticism:
What if the knock sequence are determined by brute force attack ?
Excerpt from wikipedia answers this:
——————————————————————————————————————————–
Consider that, if an external attacker did not know the port knock sequence, even the simplest of sequences would require a massive brute force effort in order to be discovered. A three-knock simple TCP sequence (e.g. port 1000, 2000, 3000) would require an attacker without prior knowledge of the sequence to test every combination of three ports in the range 1-65535, and then to scan each port in between to see if anything had opened. As a stateful system, the port would not open until after the correct three-digit sequence had been received in order, without other packets in between.
That equates to a maximum of 655363 packets in order to obtain and detect a single successful opening, in the worst case scenario. That’s 281,474,976,710,656 or over 281 trillion packets. On average, an attempt would take approximately 9.2 quintillion packets to successfully open a single, simple three-port TCP-only knock by brute force. This is made even more impractical when knock attempt-limiting is used to stop brute force attacks, longer and more complex sequences are used.
——————————————————————————————————————————–
Also, there are other port knocking solutions, where the knocks are encrypted, which makes it even harder to hack.
When we have simple, robust and reliable solution named VPN access, why to go for port knocking?
Port knocking plus VPN tunnels for added security. If you have another VPN server in your network, you shall protect it from brute force attacks by hiding it behind a knock sequence.
Disclaimer:
Port knocking is not intended to be complete solution, but can be an added layer of security.
Also, it needs to be configured properly according to the needs.
A network that is connected to the Internet is never secure. There is no perfect lock!
The best that we can do is to make the system as secure as possible for today. Possibly
tomorrow someone will figure out how to get through our security code.
A security system is only as strong as its weakest link.
But, I believe “Port knocking” adds security to the existing setup, and doesn’t make your system vulnerable to attacks, as few people claim.
Thanks for reading. Cheers !