OpenLDAP is a free open source Light Weight Directory Access protocol developed by the OpenLDAP project. It is a platform independent protocol, so that it runs on all Linux/Unix like systems, Windows, AIX, Solaris and Android.
In this tutorial i am going to describe how to install and configure OpenLDAP in Ubuntu / Debian server. Due to lack of resources and time, i tested this how-to only on Ubuntu 12.10/13.10 and Debian 7. I hope these steps will work on other version of Ubuntu and Debian. If you have any issues, do let me know, i will check and update this how-to.
Well, let us begin to setup LDAP server.
Operating System : Debian 7 Server Hostname : server.unixmen.com IP Address : 192.168.1.200
Replace the above values with your own.
Install OpenLDAP in Ubuntu/Debian
Enter the following command in Terminal to install openldap.
All steps must be done using ‘root’ user or you should use ‘sudo’ in-front of every command.
# apt-get install slapd ldap-utils
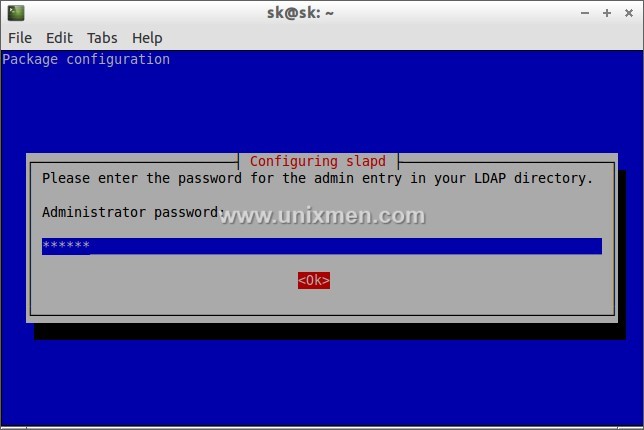
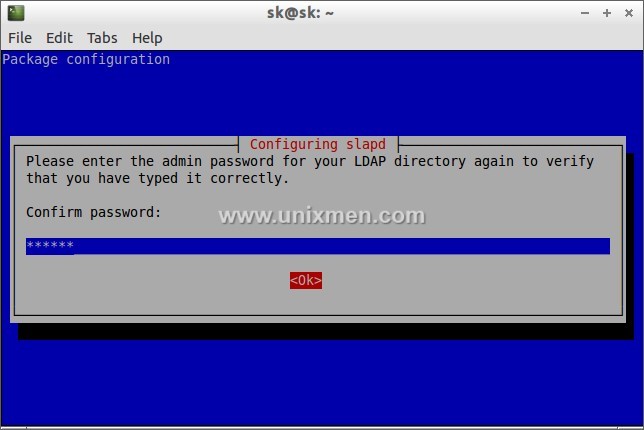
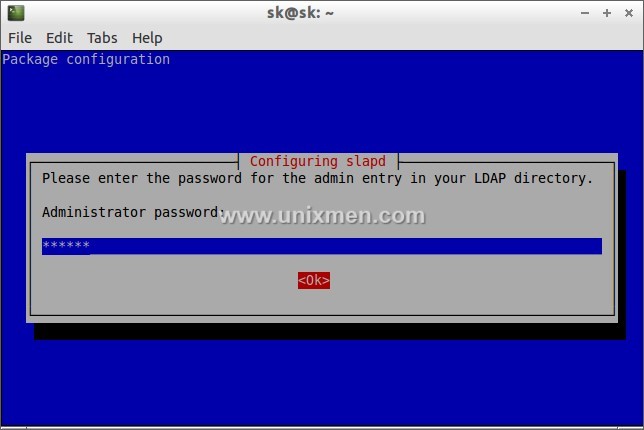
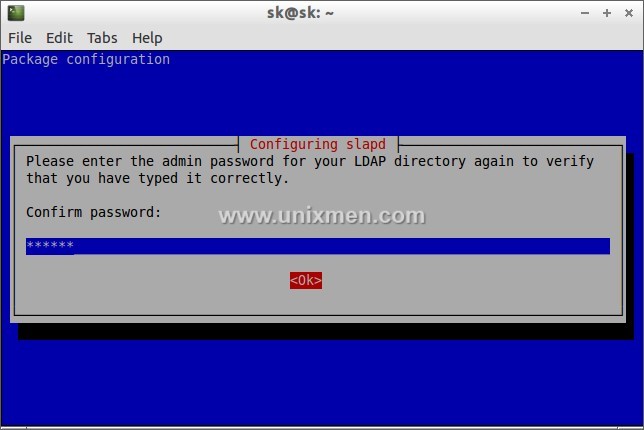
During the installation it will ask the password for LDAP admin account. Enter your admin password here.
Open the “/etc/ldap/ldap.conf” file,
# vi /etc/ldap/ldap.conf
Find, uncomment and edit the lines as shown below with your domain name and IP Address.
# # LDAP Defaults # # See ldap.conf(5) for details # This file should be world readable but not world writable. BASE dc=unixmen,dc=com URI ldap://server.unixmen.com ldap://server.unixmen.com:666 #SIZELIMIT 12 #TIMELIMIT 15 #DEREF never # TLS certificates (needed for GnuTLS) TLS_CACERT /etc/ssl/certs/ca-certificates.crt
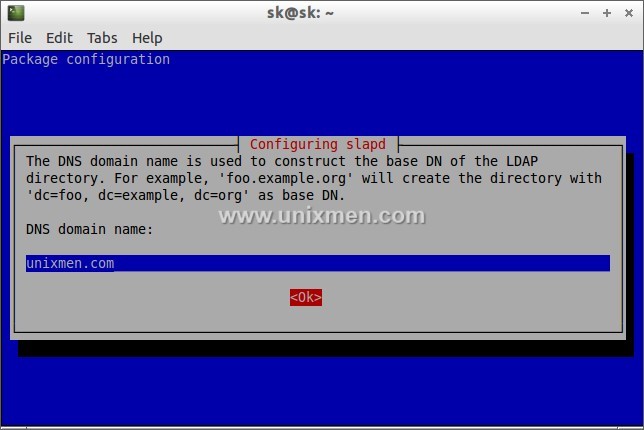
Run the Configuration assistant.
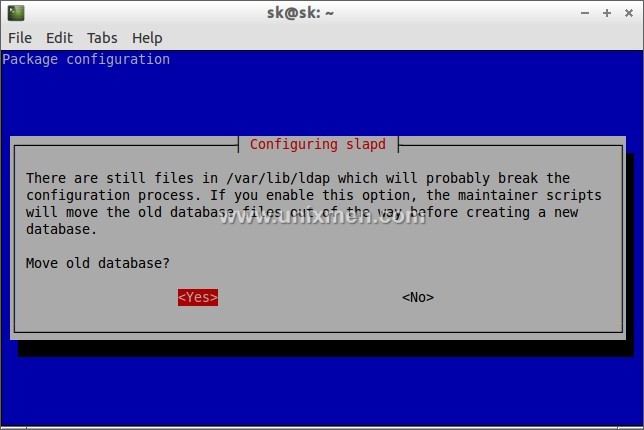
# dpkg-reconfigure slapd
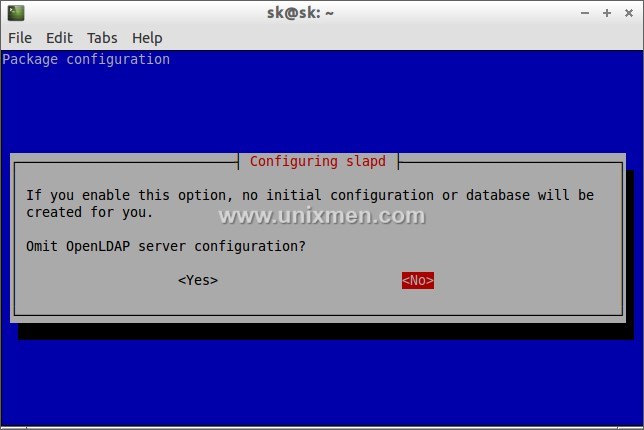
The following screen should appear. Select “No” and press Enter.
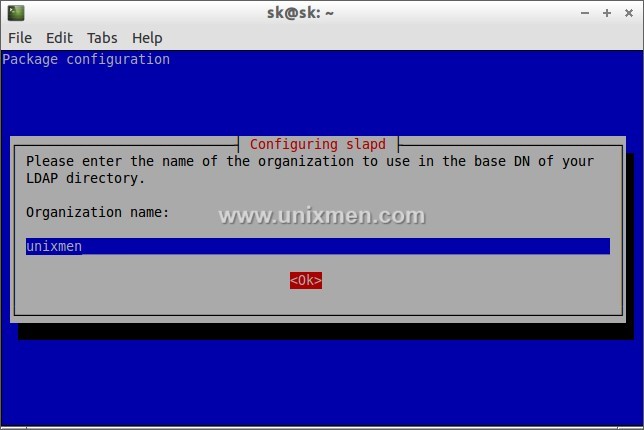
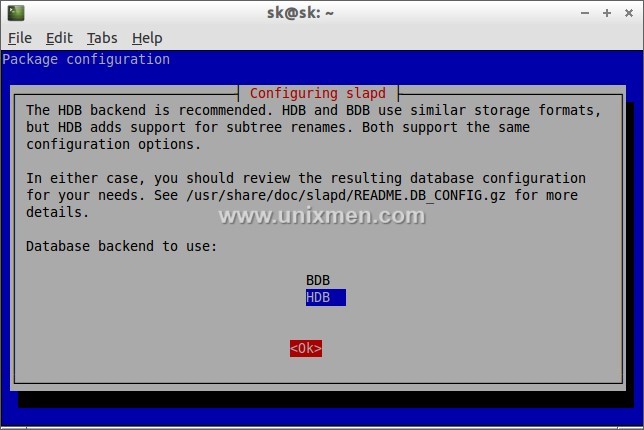
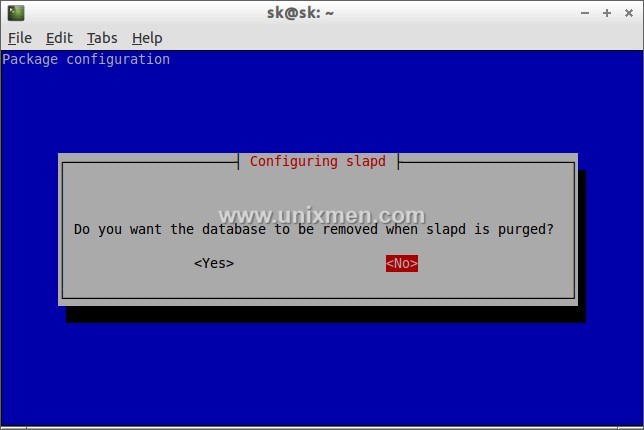
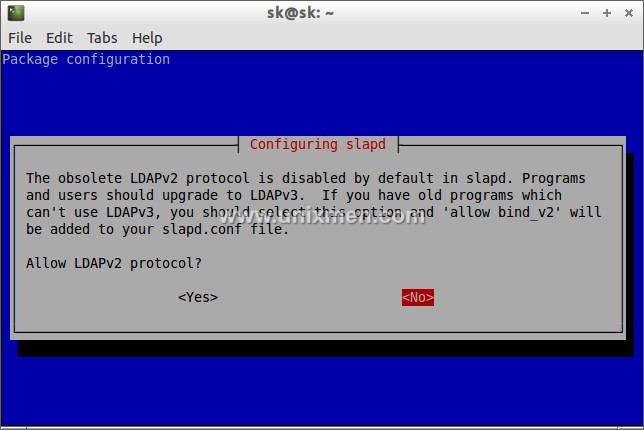
Test LDAP Server
Enter the following command “ldapsearch -x”, then you will have the following result.
# ldapsearch -x
Sample output:
# extended LDIF
#
# LDAPv3
# base <dc=unixmen,dc=com> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# unixmen.com
dn: dc=unixmen,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: unixmen
dc: unixmen
# admin, unixmen.com
dn: cn=admin,dc=unixmen,dc=com
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
LDAP Server Administration
Administration of LDAP server in command mode is quite difficult, so that here i have used a easier GUI administration tool called “phpldapadmin”.
Install phpLDAPadmin
phpLDAPadmin is a web-based LDAP administration tool for managing your LDAP server. Using phpLDAPadmin, you can browse your LDAP tree, view LDAP schema, perform searches, create, delete, copy and edit LDAP entries. You can even copy entries between servers.
Enter the following command to install phpLDAPAdmin
# apt-get install phpldapadmin
Create a symbolic link for phpldapadmin directory.
# ln -s /usr/share/phpldapadmin/ /var/www/phpldapadmin
Now open the “/etc/phpldapadmin/config.php” file,
# vi /etc/phpldapadmin/config.php
and replace the domain names with your own values. Goto “Define LDAP Servers” section in the config file and edit the following lines as shown below.
[...]
// Uncomment and set your timezone //
$config->custom->appearance['timezone'] = 'Asia/Kolkata';
[...]
// Set your LDAP server name //
$servers->setValue('server','name','Unixmen LDAP Server');
[...]
// Set your LDAP server IP address //
$servers->setValue('server','host','192.168.1.200');
[...]
// Set Server domain name //
$servers->setValue('server','base',array('dc=unixmen,dc=com'));
[...]
// Set Server domain name //
$servers->setValue('login','bind_id','cn=admin,dc=unixmen,dc=com');
[...]
Restart the apache service.
# /etc/init.d/apache2 restart
Make sure that you have opened apache server port “80” and LDAP default port “389” in your firewall/router configuration.
$ sudo ufw allow 80 Rules updated Rules updated (v6)
$ sudo ufw allow 389 Rules updated Rules updated (v6)
The above steps are not necessary for Debian systems.
Test phpLDAPadmin
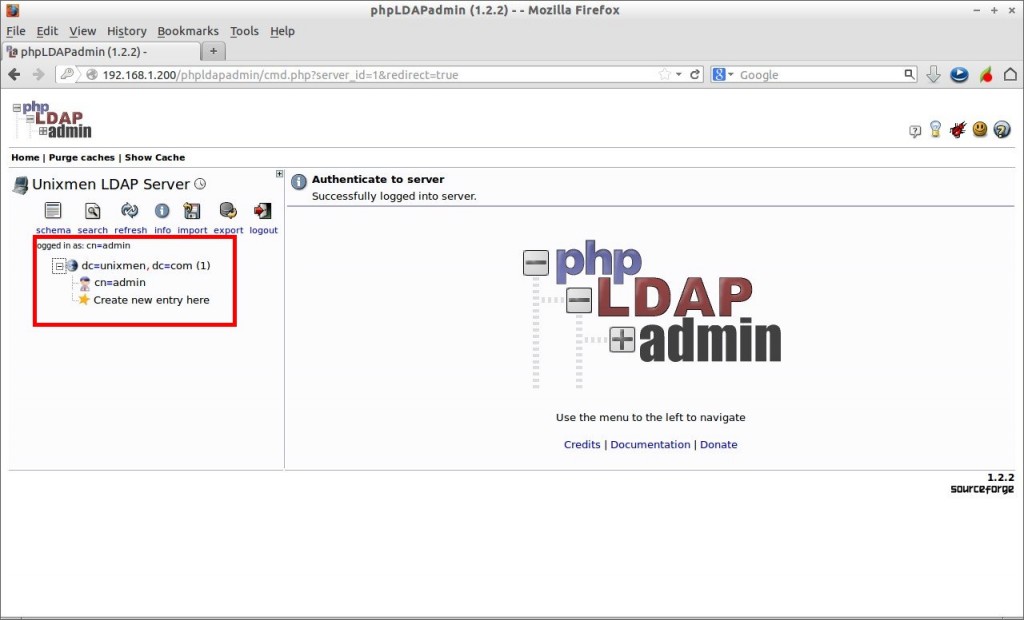
Now point your web browser with “http://192.168.1.200/phpldapadmin”. The following screen should appear.
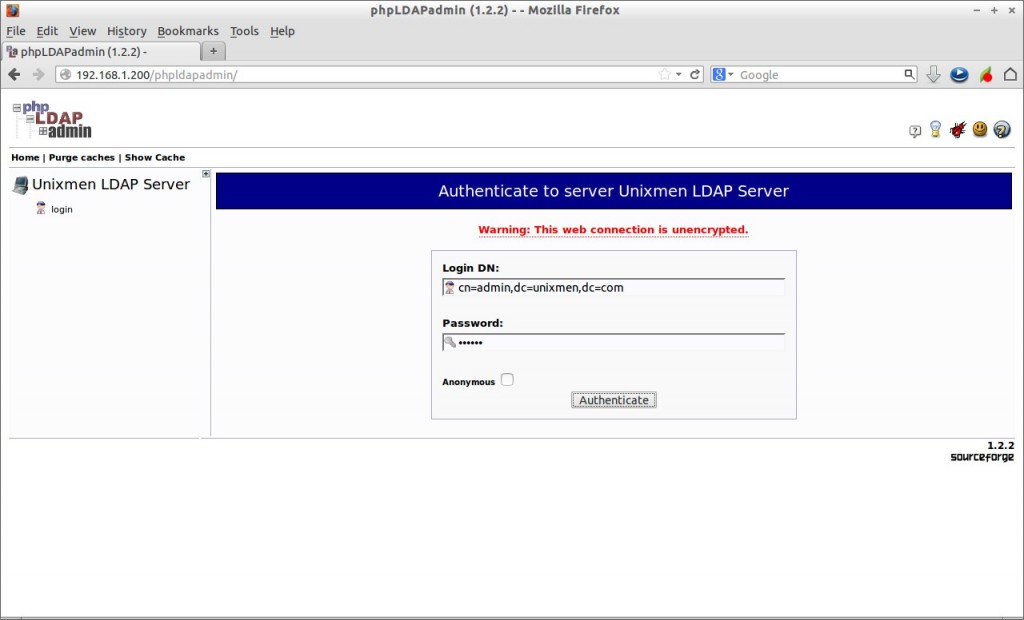
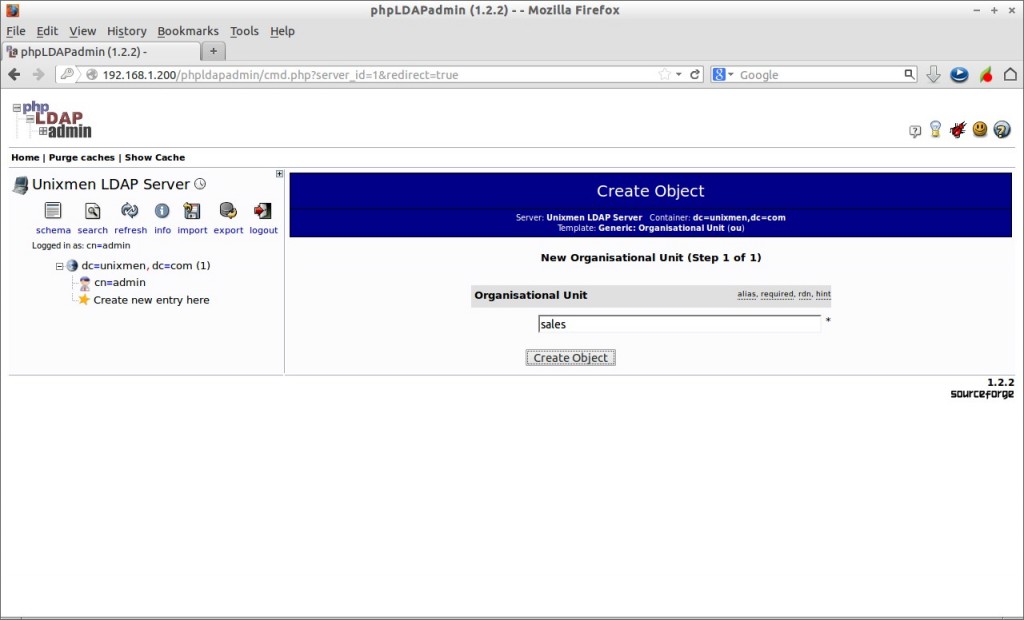
Create Organizational Unit:
Lets create some sample objects using phpldapadmin interface and check them whether they are present in the LDAP server configuration.
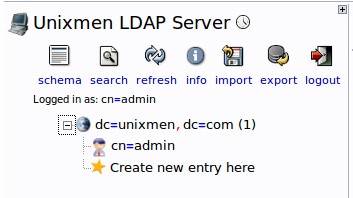
Click on the “+” sign near the line “dc=unixmen” and click “Create new entry here” link.
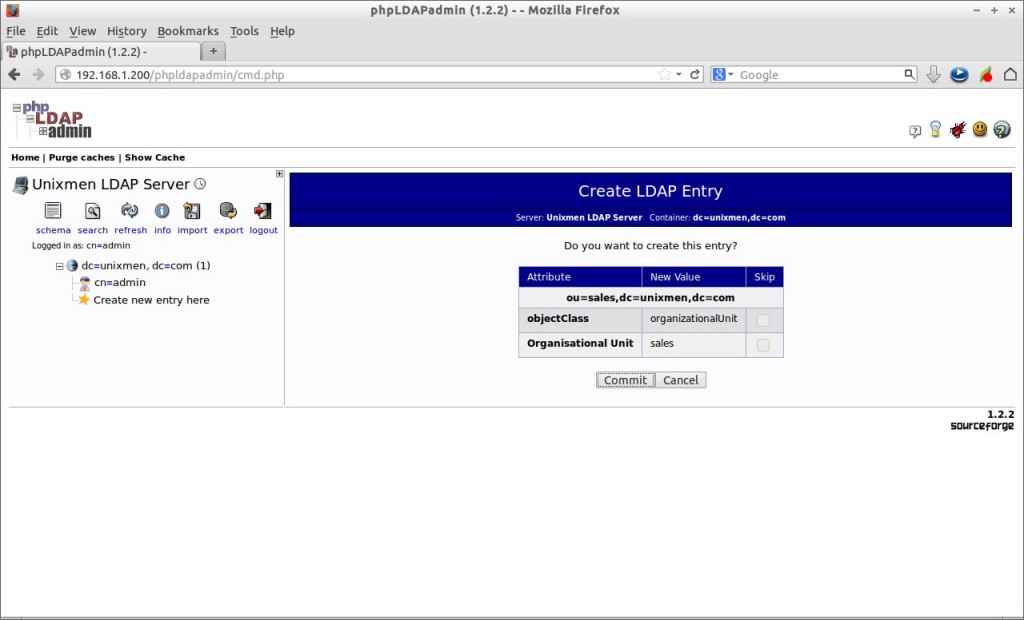
Create Group:
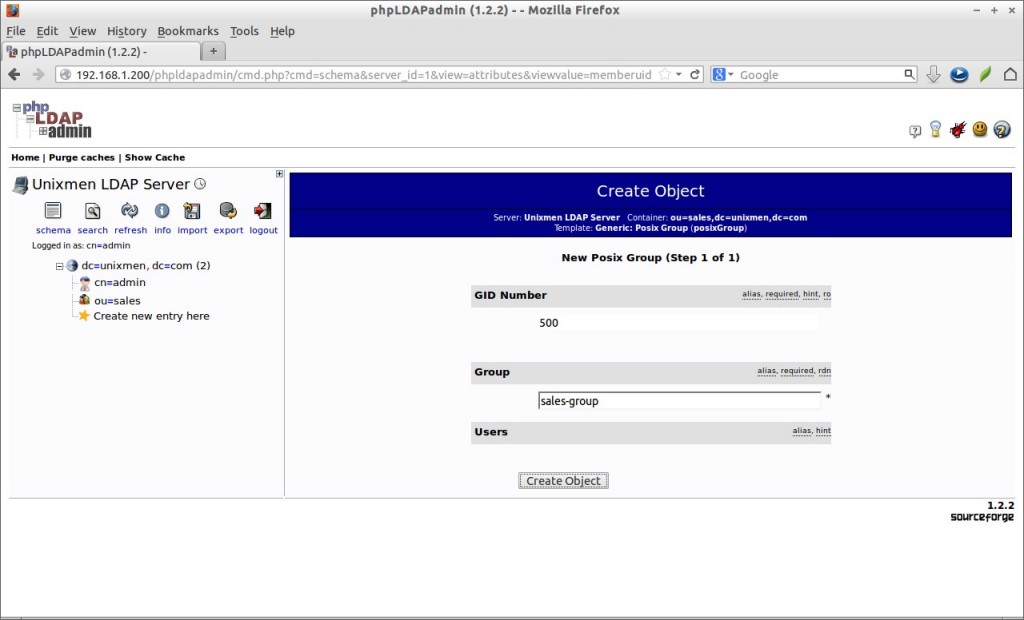
Click on the sales ou tree on the left pane and click on “Create a child entry” link.
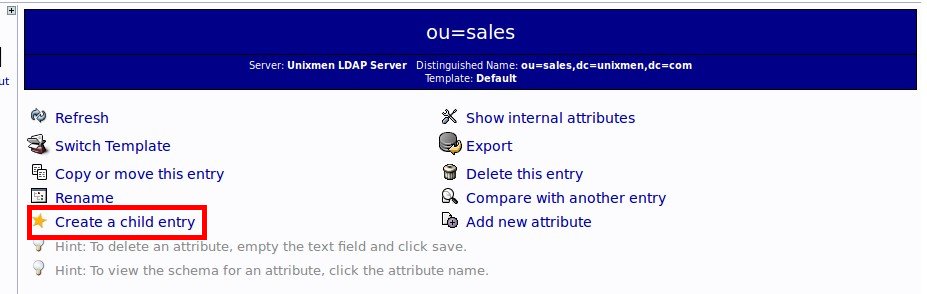
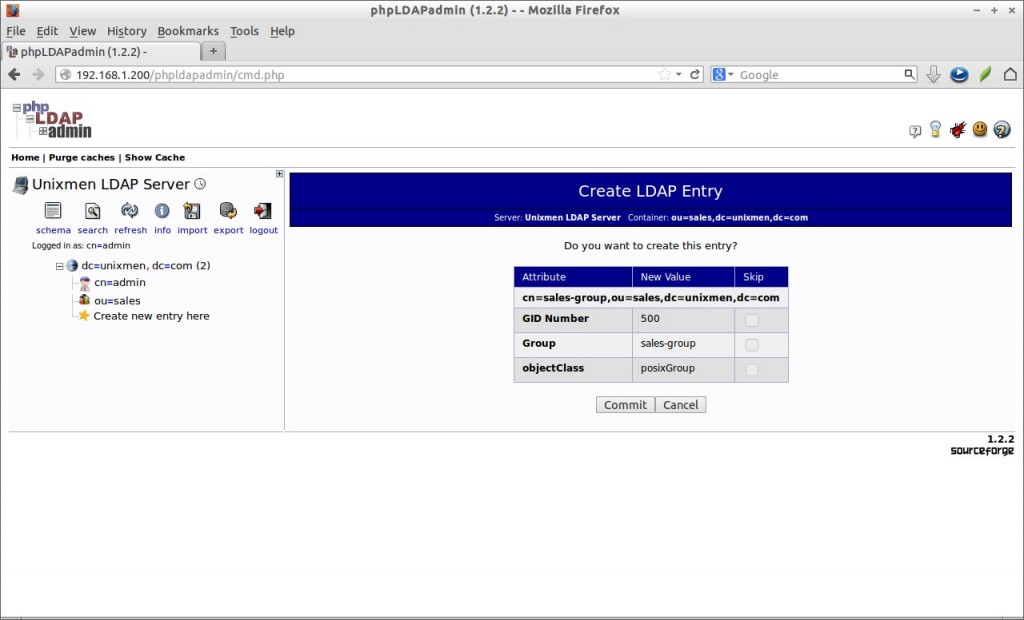
Click on the sales-group on the left and select Create a child entry link button.
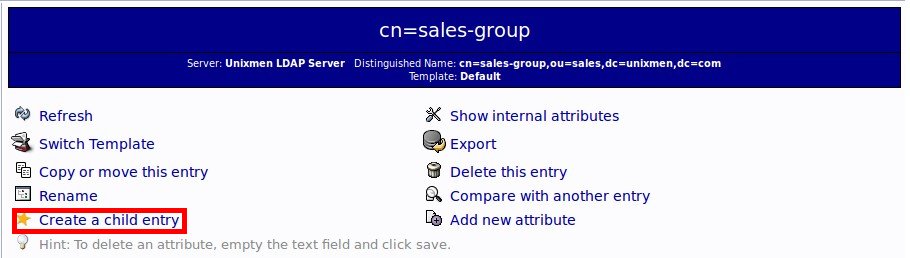
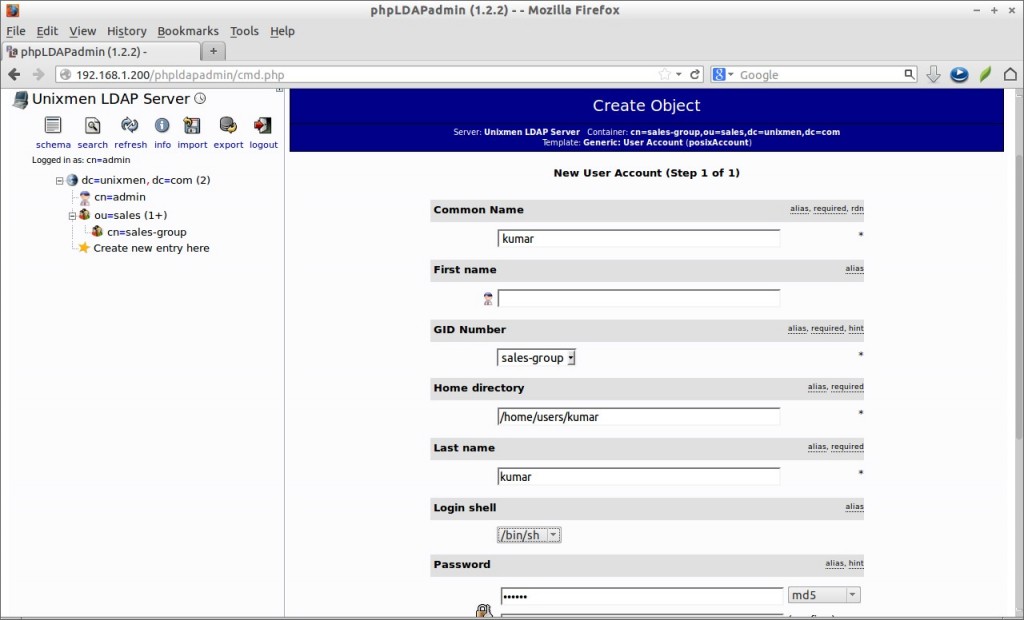
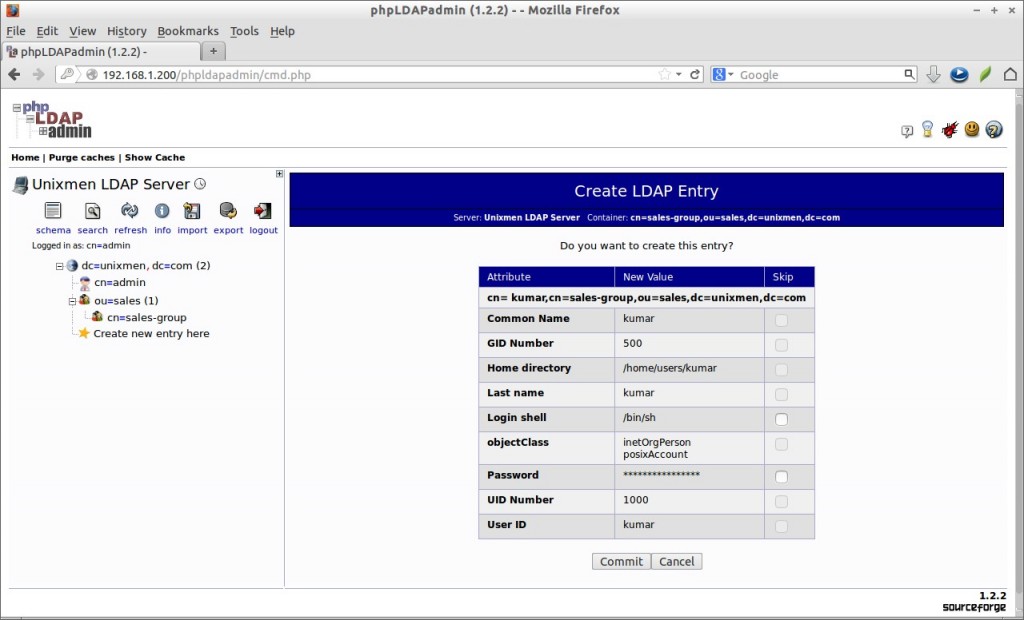
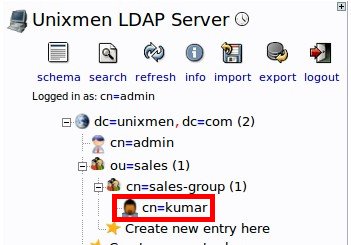
# ldapsearch -x
Sample output:
# extended LDIF # # LDAPv3 # base <dc=unixmen,dc=com> (default) with scope subtree # filter: (objectclass=*) # requesting: ALL # # unixmen.com dn: dc=unixmen,dc=com objectClass: top objectClass: dcObject objectClass: organization o: unixmen dc: unixmen # admin, unixmen.com dn: cn=admin,dc=unixmen,dc=com objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator # sales, unixmen.com dn: ou=sales,dc=unixmen,dc=com objectClass: organizationalUnit objectClass: top ou: sales # sales-group, sales, unixmen.com dn: cn=sales-group,ou=sales,dc=unixmen,dc=com gidNumber: 500 cn: sales-group objectClass: posixGroup objectClass: top # kumar, sales-group, sales, unixmen.com dn: cn=kumar,cn=sales-group,ou=sales,dc=unixmen,dc=com cn:: IGt1bWFy gidNumber: 500 homeDirectory: /home/users/kumar sn: kumar loginShell: /bin/sh objectClass: inetOrgPerson objectClass: posixAccount objectClass: top uidNumber: 1000 uid: kumar # search result search: 2 result: 0 Success # numResponses: 6 # numEntries: 5
Now OpenLDAP Server is ready to use. Good Luck!
So you have installed LDAP server, what now? Please refer next article How To Configure Linux Clients To Authenticate Using OpenLDAP.