Introduction
Spiderfoot is a very unique application used as footprint tool. It is open source tool available for both Linux and Microsoft windows platform. A very quick to use tool written in python, simply give a domain name which you wants to scan and define which modules you will be using as active, it can be used to gather information of a target and a user can identify what information your organization is freely accessible for outside attackers.It can be used either offensively to gather important informations of the target or defensively to test what your organization is providing freely to outside attackers.
FEATURES
1.fully open source and you can fork it on git.
2. based on java script and data can be export in csv form which can be utilized by using other tools.
3. a web based application which hardly require any dependencies.
4. based on pyhton and highly modular. whenever a module discover some data the data is transferred to all of other other modules which are interested in that piece of information.Modules included in spiderfoot are really a long list.
5. All of the collected data is stored in SQLite data base which make this unique piece of pen tester to run faster.
6. User can perform penetration testing for more then one targets simultaneously.
Installation
Prerequisites
Installation of Spiderfoot will take very fewer and uncomplicated steps.It require a Ubuntu 15.10 machine with minimum 2 GB RAM, 4 GB of free hard disk space and dual core process, it is recommended to have a good internet speed during penetration testing process. Apache2 server, git and python modules are required to be installed first.
Install required packages
$ sudo apt-get install git python-dev python-pip python-m2crypto python-netaddr python-pypdf python-stem python-lxml
Additionally you will require to install cherrypy and mako to install
$ sudo pip install cherrypy $ sudo pip install mako
Download the package finally
$ sudo cd /tmp && wget http://downloads.sourceforge.net/project/spiderfoot/spiderfoot-2.6.1-src.tar.gz
Decompress the package
$ tar -xvfx spiderfoot-2.6.1-src.tar.gz
Go the the directory and run Spiderfoot
$ cd spiderfoot-2.6.1 $ ./sf.py
Sample output
Starting web server at http://127.0.0.1:5001 ... ************************************************************* Use SpiderFoot by starting your web browser of choice and browse to http://127.0.0.1:5001 ************************************************************* [09/Dec/2015:21:43:13] ENGINE Listening for SIGHUP. [09/Dec/2015:21:43:13] ENGINE Listening for SIGTERM. [09/Dec/2015:21:43:13] ENGINE Listening for SIGUSR1. [09/Dec/2015:21:43:13] ENGINE Bus STARTING [09/Dec/2015:21:43:13] ENGINE Started monitor thread '_TimeoutMonitor'. [09/Dec/2015:21:43:14] ENGINE Serving on http://127.0.0.1:5001 [09/Dec/2015:21:43:14] ENGINE Bus STARTED
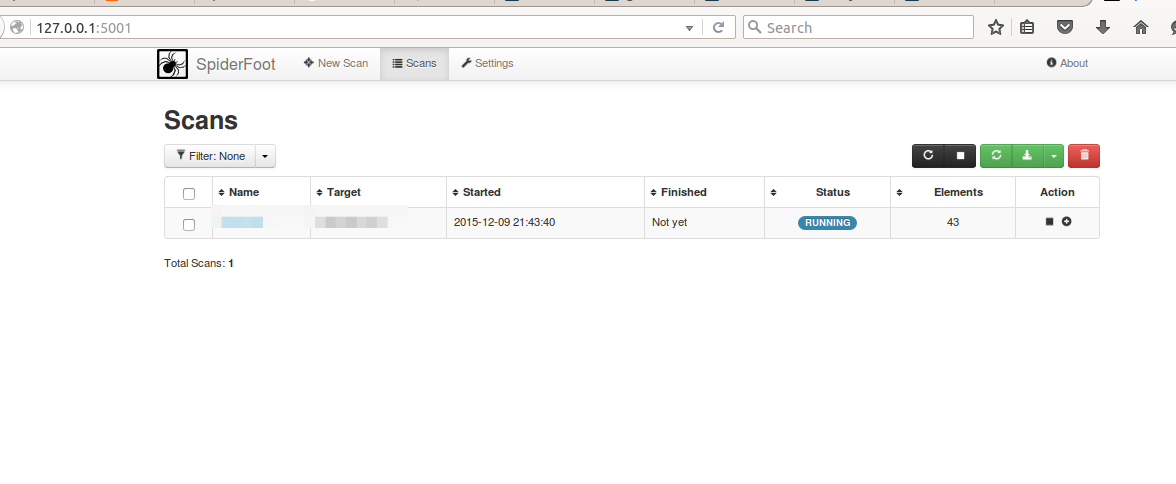
Open browser and type 127.0.0.1:5001
Start scanning for certain target
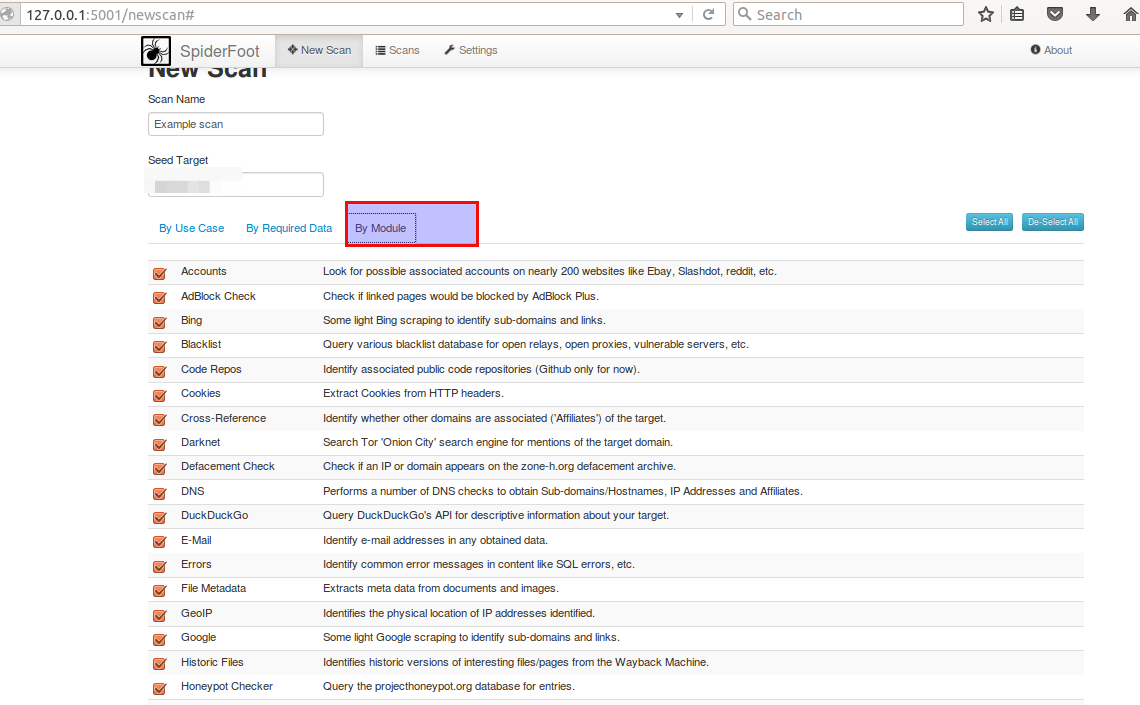
Start a new scan go to home page of sash board give any name to the operation and provide name of the website for which you wants to run this operation
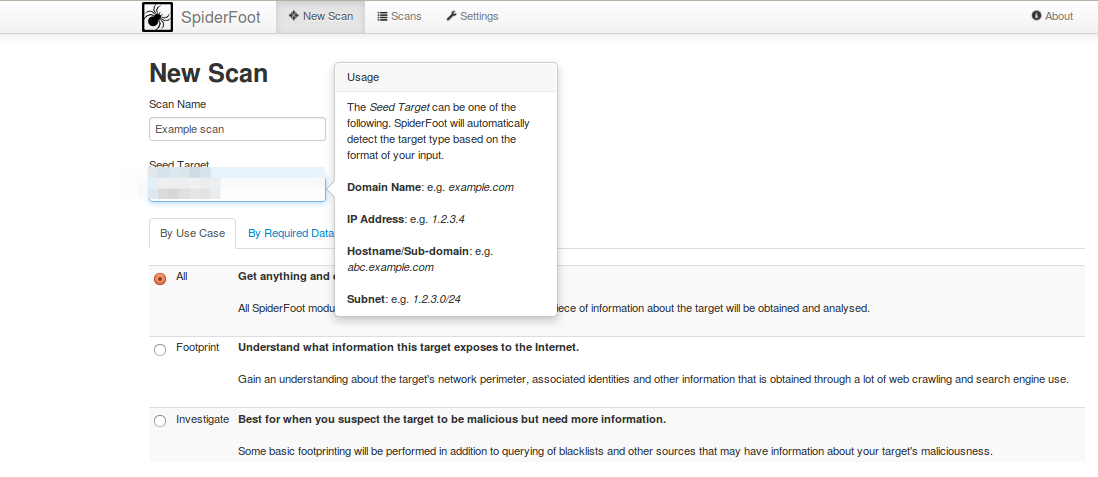
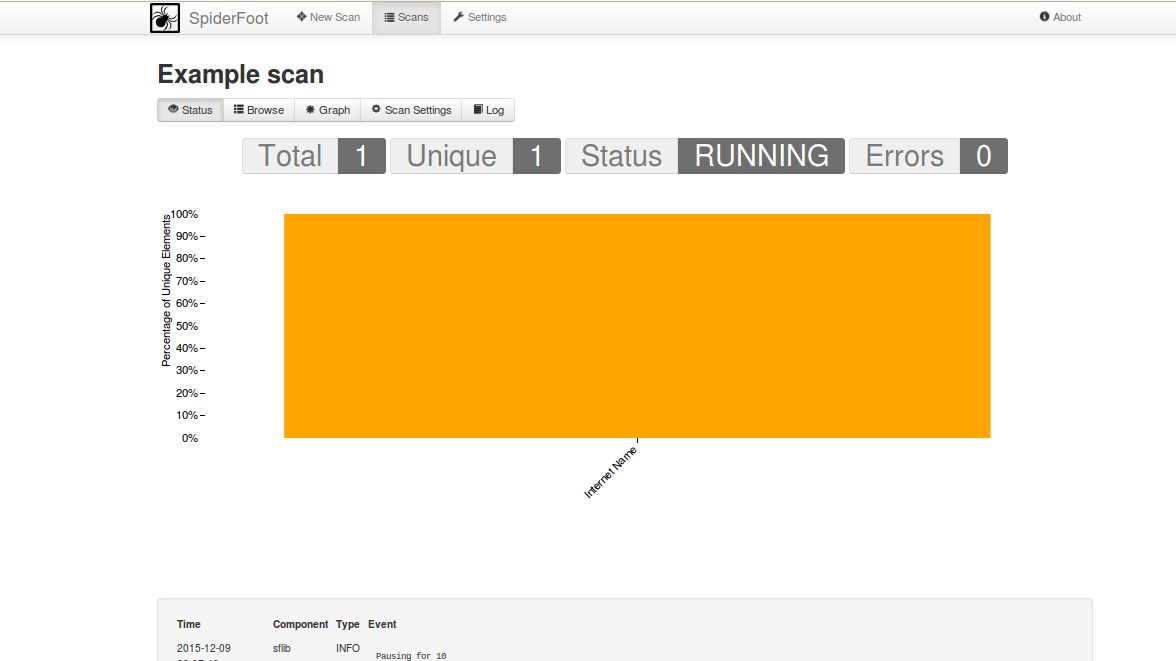
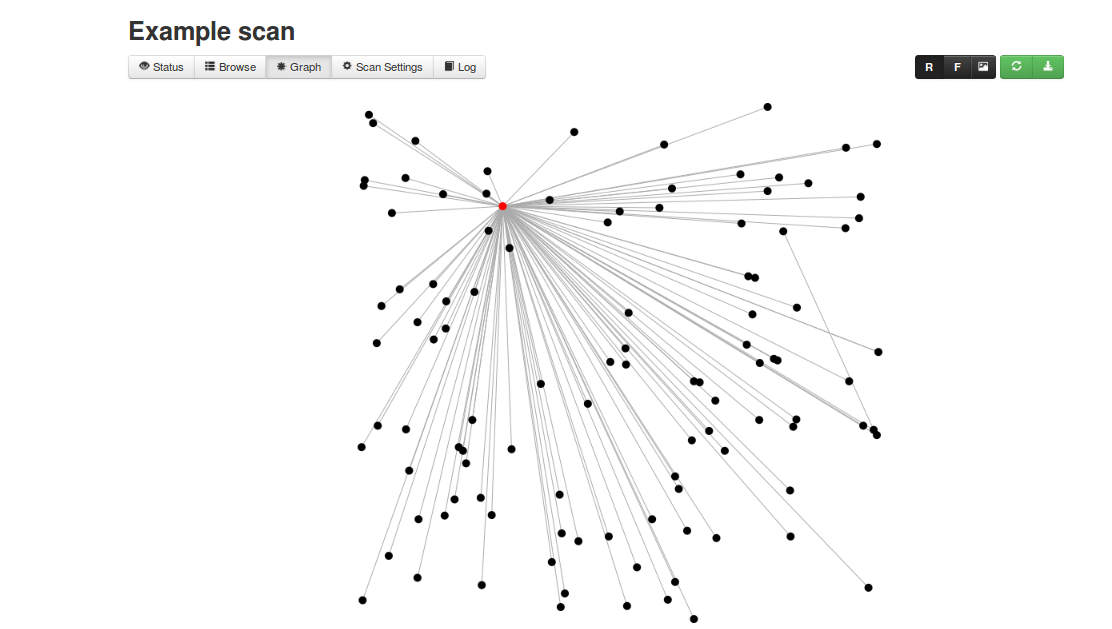
Let us begin the scan process by clicking on run scan, graph will look something like below at the beginning time of scan process
This is how the status bar will look like after few minutes
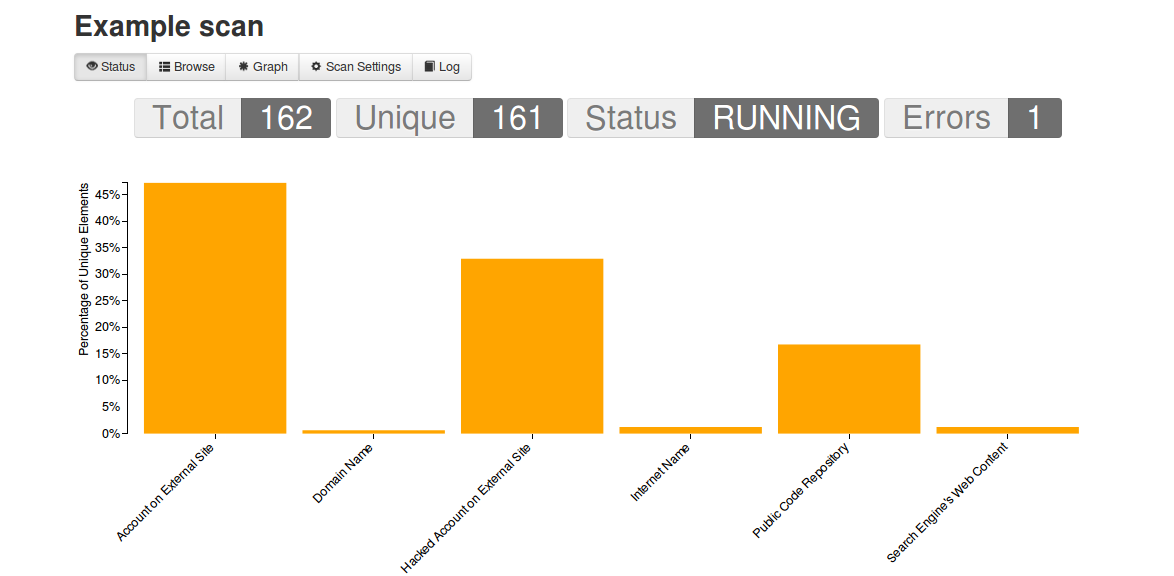
Graphs status will look something like below
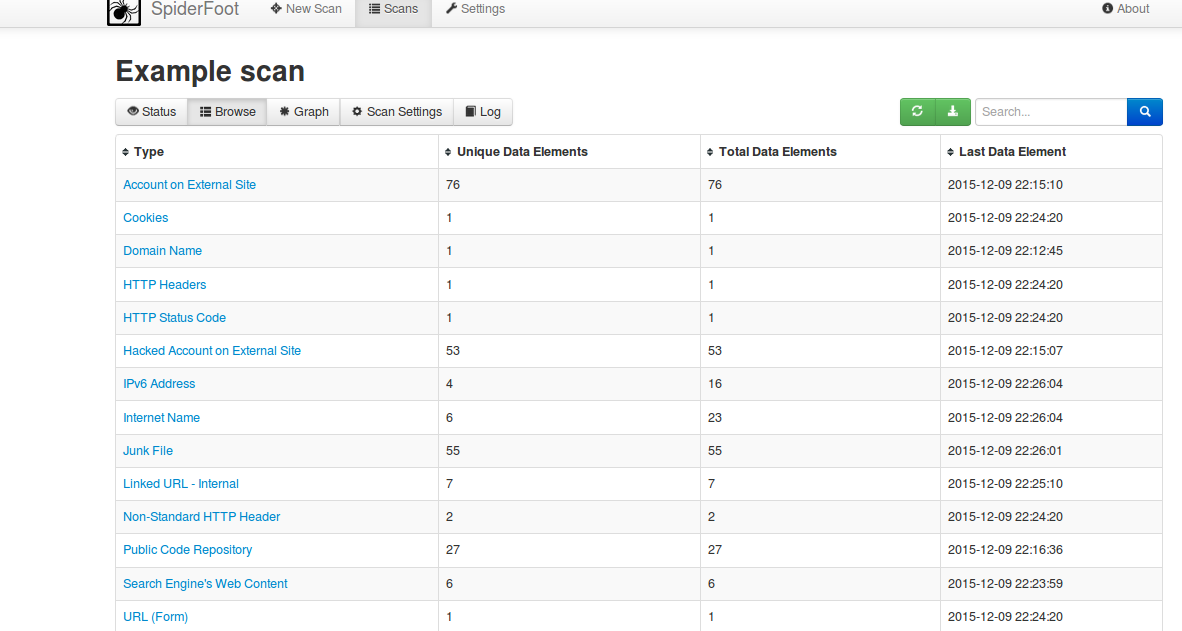
By click on Browser you can have a look on data based on various types
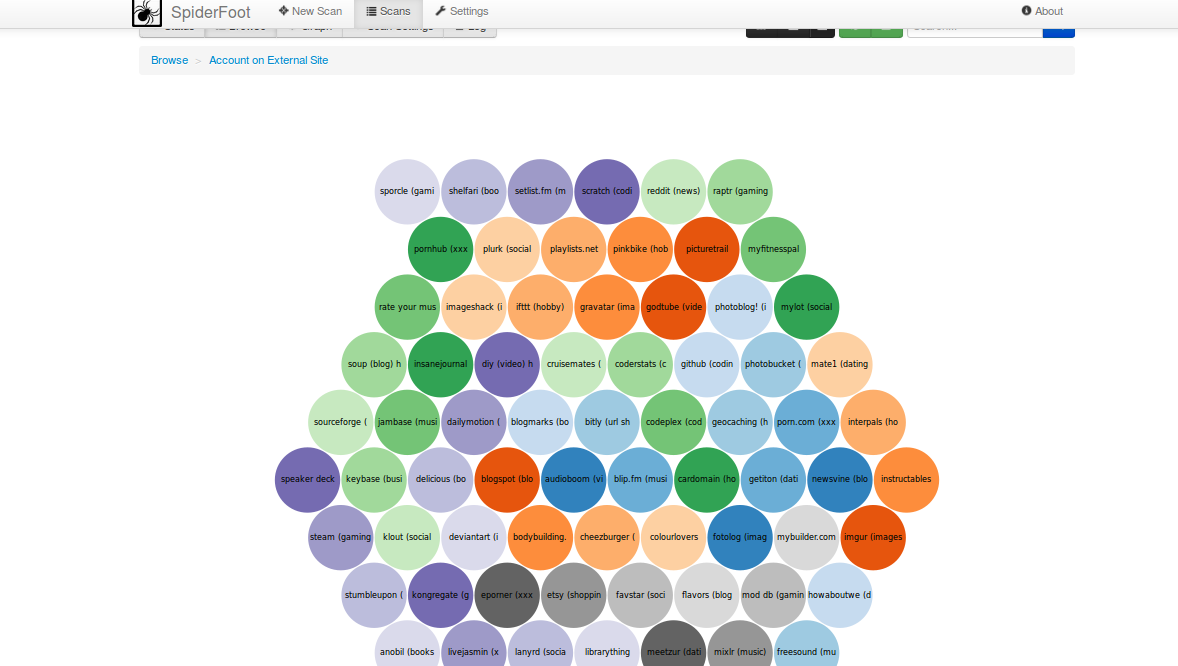
Now click on any Browser link to have visuals and data elements
In discovery path mode data view will be something like
This is how the bubble view will look like
conclusion
A must have for users performing penetration settings, avoid to use directly on running or live web services as this application does not provided with user authentication but this features will be soon available in future. very easy to use, a running scan can be delete, pause or resume at any time.
Have Fun!!