Introduction
In today’s digital world, organizations are always looking for ways to optimize their IT infrastructure, improve resource utilization, and enhance operational efficiency. Enter the RHEV Hypervisor. This is a powerful virtualization solution from Red Hat that revolutionizes the way enterprises manage and deploy virtual machines (VMs). The hypervisor is built on the robust foundation of the Kernel-based Virtual Machine (KVM) technology. The technology offers a comprehensive set of features that empower organizations to maximize their virtualization capabilities.
What is the RHEV Hypervisor?
The RHEV Hypervisor, also known as the Red Hat Enterprise Virtualization Hypervisor, is a high-performance, secure, and scalable virtualization platform designed specifically for enterprise environments. Moreover, it is a key component of the Red Hat Enterprise suite, which provides a complete virtualization solution for orchestrating virtual resources across the IT infrastructure.
Key Features of the RHEV Hypervisor
Some of the key features of the Hypervisor include:
- Robust Performance: Built on the KVM hypervisor, the RHEV Hypervisor delivers exceptional performance. In addition this ensures that virtual machines run efficiently and with minimal overhead.
- Scalability: The hypervisor supports advanced features like live migration, high availability, and seamless integration with storage solutions. Above all, this enables organizations to scale their virtualization infrastructure as needed.
- Open Standards: Leveraging open standards and technologies, the RHEV Hypervisor ensures compatibility with a wide range of hardware and software platforms.
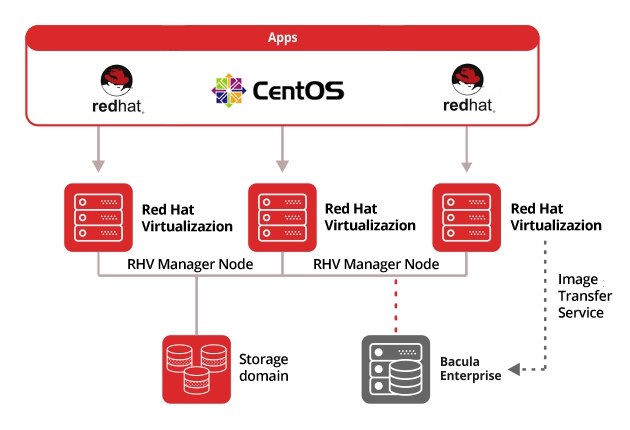
- Centralized Management: The Hypervisor seamlessly integrates with the RHEV Manager. This is a centralized management console that simplifies the deployment, monitoring, and administration of virtual resources.
- Resource Optimization: Advanced resource management capabilities enable efficient utilization of compute, storage, and network resources. In addition this reduces hardware costs and maximizing return on investment (ROI).
- Security and Compliance: The RHEV Hypervisor adheres to industry-leading security standards and provides robust compliance features, ensuring the protection of sensitive data and meeting regulatory requirements.
Benefits of the RHEV Hypervisor
There are several benefits using rhev in your organization, The advantages include;
- Increased Agility: By enabling rapid provisioning and deployment of virtual machines, the RHEV Hypervisor empowers organizations to quickly respond to changing business demands and accelerate time-to-market.
- Cost Savings: Through efficient resource utilization and consolidation, the hypervisor helps organizations reduce hardware costs, energy consumption, and overall operational expenses.
- Improved Reliability: Built-in high availability and live migration features ensure continuous uptime and minimize downtime, enhancing the reliability of mission-critical applications.
- Simplified Management: The centralized management console streamlines the administration and monitoring of virtual resources, reducing complexity and improving operational efficiency.
- Flexibility and Scalability: The RHEV Hypervisor’s support for open standards and seamless integration with storage solutions enables organizations to scale their virtualization infrastructure seamlessly as their needs grow.
Getting Started with the RHEV Hypervisor
To harness the power of the RHEV Hypervisor, organizations need to ensure their infrastructure meets the necessary requirements and follow the proper installation and setup procedures.
System Requirements
The RHEV Hypervisor has specific hardware and software requirements to ensure optimal performance and compatibility. These include:
- Supported server hardware platforms (consult the RHEV documentation for the latest supported hardware)
- Minimum system memory and CPU requirements
- Compatible storage solutions (e.g., iSCSI, FCP, NFS)
- Network infrastructure for management and virtual machine connectivity
Installation and Setup
The installation process for the RHEV Hypervisor typically involves the following steps:
- Prepare the physical server(s) by ensuring they meet the system requirements.
- Download the RHEV Hypervisor ISO image from the Red Hat Customer Portal.
- Boot the server from the ISO image and follow the guided installation wizard.
- Configure network settings, storage connections, and other necessary components.
- Register the RHEV Hypervisor with the RHEV Manager for centralized management and monitoring.
Managing Virtual Machines
Once the RHEV Hypervisor is installed and registered, administrators can leverage the RHEV Manager to perform various virtual machine management tasks, such as:
- Creating and deploying new virtual machines
- Managing virtual machine resources (CPU, memory, storage)
- Monitoring virtual machine performance and utilization
- Performing live migrations and high availability operations
- Configuring virtual machine networking and storage
Advanced Capabilities
The RHEV Hypervisor offers a range of advanced capabilities that enhance its functionality and versatility:
Live Migration
Live migration enables administrators to move running virtual machines from one physical host to another without disrupting services or causing downtime. This feature is particularly useful for hardware maintenance, load balancing, and optimizing resource utilization.
High Availability
The RHEV Hypervisor supports high availability clustering, ensuring that virtual machines are automatically restarted on other available hosts in the event of a hardware failure or planned maintenance, minimizing service interruptions and maximizing uptime.
Storage Integration
The hypervisor seamlessly integrates with various storage solutions, including iSCSI, Fibre Channel, and NFS, enabling organizations to leverage their existing storage infrastructure and providing flexibility in managing virtual machine storage requirements.
Security and Compliance
In today’s cybersecurity landscape, ensuring the protection of sensitive data and adhering to compliance regulations is of utmost importance. The RHEV Hypervisor addresses these concerns through a range of security features and compliance certifications:
- Secure Virtualization: Firstly the hypervisor leverages advanced virtualization technologies, such as Kernel-based Virtual Machine (KVM) and Security-Enhanced Linux (SELinux). Additionally this provides robust isolation and protection of virtual machines.
- Access Controls: Granular access controls and role-based access management ensure that only authorized personnel can perform specific actions on virtual resources. Additionally minimizing the risk of unauthorized access or changes.
- Encryption and Auditing: The Hypervisor supports encryption for virtual machine data and provides comprehensive auditing capabilities, enabling organizations to meet regulatory compliance requirements and maintain data integrity.
- Compliance Certifications: Red Hat’s virtualization solutions, including the RHEV Hypervisor, are certified for various industry standards and regulatory requirements, such as FIPS 140-2, DISA STIG, and PCI DSS. This ensures compliance with stringent security and data protection regulations.
RHEV Hypervisor vs. Other Hypervisors
While there are several virtualization solutions available in the market, the RHEV Hypervisor stands out with its robust enterprise-grade features, open standards, and seamless integration with the Red Hat ecosystem. When compared to other hypervisors, such as VMware ESXi or Microsoft Hyper-V, the RHEV Hypervisor offers several advantages:
- Open Source and Open Standards: Firstly by leveraging open-source technologies and adhering to open standards, the Hypervisor ensures greater interoperability. This avoids vendor lock-in.
- Comprehensive Management: The RHEV Manager provides a centralized management console for administering virtual resources across the entire virtualization infrastructure. More importantly, this simplifies management tasks and improving operational efficiency.
- Tight Integration with Red Hat Ecosystem: As a part of the Red Hat Enterprise Virtualization suite, the Hypervisor seamlessly integrates with other Red Hat products and solutions. Additionally this enables organizations to leverage the full power of Red Hat’s enterprise-grade technologies.
- Strong Security and Compliance: Built with security and compliance in mind, the virtualization software adheres to industry-leading security standards and provides robust compliance features. Moreover this ensures the protection of sensitive data and meeting regulatory requirements.
- Scalability and High Availability: The RHEV Hypervisor supports advanced features like live migration, high availability clustering, and seamless integration with storage solutions. This enables organizations to scale their virtualization infrastructure and ensure continuous uptime for critical applications.
Leveraging these advantages, organizations can benefit from a powerful and flexible virtualization solution.
Related Articles
RHEV 3.1 storage: Functionality and considerations
How to Monitor Red Hat Enterprise Virtualization (RHEV)
More Articles from Unixmen
Red Hat Enterprise Linux 6.5 Has Been Released!
RHE Virtualization via web portal
Proxmox Virtual Environment (ProxmoxVE) Is An Open Source Virtualization Solution